|
| |
Glossary of Terms
A -
B -
C -
D
- E
- F
- G
-
H -
I -
J -
K
- L
- M
- N
-
O -
P -
Q -
R
- S
- T
- U
-
V -
W -
X -
Y
- Z
0G -
PTT, MTS, IMTS, AMTS are 0G
standards.
0.5G -
Autotel/PALM and ARP are 0.5G
standards.
1G
- First Generation. The first
generation of cellular wireless (1G) was based on analog technology. The systems
were designed only to carry voice technology. NMT, AMPS, Hicap, CDPD, Mobitex,
DataTac are 1G standards.
2G
- Second Generation.
Second-generation (2G) technology converts voice to digital data for
transmission over the air and then back to voice. Most 2G systems provide
9.6–14.4-Kbps circuit-switched data service. Examples would be
GSM, iDEN, D-AMPS, CDMAOne, PDC,
CSD, and PHS.
2.5G -
2.5G refers to technology that is added to a 2G network to provide packet-data
service. In practice, 2.5G is synonymous with the GPRS technology that has been
added to GSM networks. HSCSD, and WiDEN are other examples of 2.5G
2.75G -
CDMA20001xRTT and EGPRS or EDGE (a
further evolution of GPRS)
3G -
Third Generation. Third-generation
(3G) systems have been designed for both voice and data. By International
Telecommunications Union (ITU) definition, 3G systems must provide a minimum of
144-Kbps packet-data service. 3G examples are: W-CDMA UMTS FOMA, CDM2000
1xEV, TD-SCDMA, and UMA standards.
3.5G -
HSDPA is a 3.5G standard.
3.75G -
HSUPA is a 3.75G standard.
3GPP -
The 3rd Generation
Partnership Project is a collaboration agreement that was established in
December 1998. It's a co-operation between ETSI (Europe), ARIB/TTC (Japan), CCSA
(China), ATIS (North America) and TTA (South Korea). The scope of 3GPP is
to make a globally applicable third generation (3G) mobile phone system
specification within the scope of the ITU's IMT-2000 project. 3GPP
specifications are based on evolved GSM specifications, now generally known as
the UMTS system. Note that 3GPP should not be confused with 3GPP2, which
specifies standards for another 3G technology based on IS-95 (CDMA), commonly
known as CDMA2000.
3GPP standards are structured as Releases. Discussion of 3GPP thus
frequently refers to the functionality in one release or another: Release 98
and earlier releases specify pre-3G GSM networks.
Release 99 specify the
first UMTS 3G networks, incorporating a CDMA air interface. Release 4 -
originally Release 2000 - adds features including an All IP Core Network
Release 5 introduces IMS and HSDPA. Release 6 integrates
operation with Wireless LAN networks and adds HSUPA. Release 7 work
towards better integration with wired networks. Release 8 GSM Phase
2+ and UMTS Release 8, Handover capabilities for combinational services between
WCDMA and WLAN networks.
75-Ohm
Antenna/Cable Input -
Compatible with any 75-ohm set-top/roof-top VHF/UHF antenna system as well as
any residential/commercial CATV/CCTV system.
A
Acoustic Echo Canceller (AEC) - Full Duplex audio technology; used for the
elimination of acoustically-coupled return echoes within a teleconference room.
Note that all microphones connected to an AEC are active at all times.
Consequently, as more microphones are added, the total transmitted noise level
(caused by picking up room ambient noise) increases.
Access Method - In Local
Area Networks, the technique and /or program code used to arbitrate the use of
the communications medium by granting access selectively to individual stations.
Examples are CSMA/CD and Token Passing.
Access Point (AP) - A
networking device that enables wireless stations to access the
wired LAN infrastructure.
Adaptor -
computer add-in
board. Network adapters are used to connect end user nodes to the network;
each contains an interface to a specific type of workstation or system bus.
E.g.: EISA, ISA, MCA, VME, etc.
Adaptive
Routing -
A form
of routing in which messages are forwarded through the network along the most
cost-effective path currently available and are automatically rerouted if
required by changes in the network topology (for example, if a circuit becomes
disabled.)
Address -
A designator defining the unique
ID of a terminal, peripheral device or any other nodal component in a network.
ADM - Add-drop
multiplexer - A main element of optical
fiber networks. An add-drop multiplexer combines, or multiplexes, several
lower-speed streams of data into a single beam of light. ADMs can be used both
in long-haul core-networks and in shorter distance metro networks, although in
recent years (2002-04) most ADM sales have been in metro networks due to the
high cost required to scale the technology to high data rates (wavelength
division multiplexing, better known as DWDM, is more popular in the core).
Ad-hoc Network -
An ad-hoc network is a wireless
network created for a specific purpose, typically in a spontaneous manner
without use of an access point. The principle characteristic of an ad-hoc
network is that the act of creating and dissolving the network is sufficiently
straightforward and convenient so as to be achievable by non-technical users of
the network facilities.
ADSL - Asymmetric Digital
Subscriber Line (ADSL) is a form of DSL, a data communications technology that
enables faster data transmission over copper telephone lines than a conventional
modem can provide. ADSL uses two separate frequency bands. The band from 25.875 kHz to 138 kHz is
used for upstream communication, while 138 kHz - 1104 kHz is used for downstream
communication.
The ADSL Standards are as follows:
| Standard name |
Standard type |
Downstream rate |
Upstream rate |
|
ANSI T1.413-1998 Issue 2 |
ADSL |
8 Mbit/s |
1.0 Mbit/s |
|
ITU G.992.1 |
ADSL (G.DMT) |
8 Mbit/s |
1.0 Mbit/s |
|
ITU G.992.2 |
ADSL Lite (G.Lite) |
1.5 Mbit/s |
0.5 Mbit/s |
|
ITU G.992.3/4 |
ADSL2 |
12 Mbit/s |
1.0 Mbit/s |
|
ITU G.992.3/4 Annex J |
ADSL2 |
12 Mbit/s |
3.5 Mbit/s |
|
ITU G.992.5 |
ADSL2+ |
24 Mbit/s |
1.0 Mbit/s |
|
ITU G.992.5 Annex L |
ADSL2+ |
24 Mbit/s |
3.5 Mbit/s |
Adware - Adware or advertising-supported software is any
software package which automatically plays, displays, or downloads
advertising material to a computer after the software is installed on it or
while the application is being used.
AES -
Advanced Encryption Standard (AES), also known as Rijndael,
is a block cipher adopted as an encryption standard by the US government, and is
expected to be used worldwide and analyzed extensively, as was the case with its
predecessor, the Data Encryption Standard (DES). It was adopted by National
Institute of Standards and Technology (NIST) as US FIPS PUB 197 in November
2001 after a 5-year standardization process (see Advanced Encryption Standard
process for more details). The cipher was developed by two Belgian
cryptographers, Joan Daemen and Vincent Rijmen, and submitted to the AES
selection process under the name "Rijndael", a portmanteau comprised of the
names of the inventors. Rijndael can be pronounced "Rhine dahl", a long "i"
and a silent "e".
Alias, Aliasing
- A
false signal produced by the analog-to-digital sampling process. Often caused by
failure to observe the Nyquist criterion and can create artifacts which are
subjectively. A common form of aliasing is a stair-stepped appearance along
diagonal and curved lines.
Algorithm -
The specific formula or procedure used to compress and decompress digital audio
and video.
American National Standards Institute (ANSI) - An
organization that coordinates, develops, and publishes standards Standards
Institute for use in the United States. It also represents the United
States in the International Standards Organization (ISO).
AMPS Analog -
Advanced Mobile Phone Service (AMPS) has been available since 1976 when it was
first used on a trial basis in the U.S. and then commercialized in the early
1980s. With AMPS, each channel can handle a single voice call. In order to add
more capacity to an AMPS cellular system, more channels per cell site or more
cell sites must be added.
AMR -
Adaptive Multi-Rate is an
Audio data compression scheme optimized for
speech coding. AMR is adopted as the standard speech codec by
3GPP. The codec has eight bit rates, 12.2, 10.2, 7.95, 7.40, 6.70, 5.90, 5.15 and 4.75
Kbit/s. The bitstream is based on frames which contain 160 samples and are 20
milliseconds long. AMR uses different techniques, such as
Algebraic Code Excited Linear Prediction (ACELP),
Discontinuous Transmission (DTX),
voice activity detection (VAD) and
comfort noise generation (CNG). The idea to use various modes arises from the network conditions. If the channel
is bad,
source coding is reduced and
channel coding is increased. This improves the quality and robustness of the
network. In the particular case of AMR this improvement is somewhere around 4-6
dB S/N for useable communication. The usage of AMR requires optimized link
adaptation that selects the best codec mode to meet the local radio channel and
capacity requirements. The new intelligent system allows the network operator to
prioritize capacity or quality per base station.
Analog video - A video signal represented in a waveform by physical
variables such as voltage and current.
ANSI-136 - is
called TDMA in the Americas. See TDMA Standards, D-AMPS.
ANSI-41 -
ANSI-41 is a protocol standardized by the Telecommunications Industry
Association (TIA) and the American National Standards Institute (ANSI) for
enabling cdmaOne, cdma2000 and TDMA subscribers to roam between different
wireless service operators’ systems to make and receive voice calls.
ANSI X3T9.5 - A sub-committee sponsored by ANSI, which sets system
interconnection standards, including the specifications for Fiber Distributed
Data Interface (FDDI).
Antialiasing -
A method for smoothing the jagged
edges (stair steps) often seen in graphics or video. The method reduces the
jagged edges by placing intermediate shades of color or gray around the steps.
AS - An Application Server
is a server computer in a computer network dedicated to
running certain software applications. The term also refers to the software
installed on such a computer to facilitate the serving (running) of other
applications. Following the success of the
Java
platform, the term application server often refers to a
J2EE application
server.
WebSphere (IBM),
Oracle Corporation (Application
Server 10g) and
WebLogic (BEA)
are the better known commercial
J2EE application servers. The
JOnAS application server, developed by the
ObjectWeb
consortium, is the first non-commercial, open source application server to have
reached the official
certification of compliance with J2EE. The programming language used is
Java. The web modules are
servlets
and
JavaServer Pages (JSP), and business logic is built into
Enterprise JavaBeans (EJB). The
Java 2 Platform, Enterprise Edition (J2EE) provides standards for containing
the web components.
Tomcat from
Apache and JOnAS from ObjectWeb are typical of containers to put these
modules into. Both organizations provide the code freely and openly (open
source). JSP is a Servlet from Java that execute in a web container--the Java equivalent
of CGI
scripts. JSP is a way to create
HTML pages by
embedding references to the server logic within the page. HTML coders and Java
programmers can work side by side by referencing each other's code within their
own.
JavaBeans are the independent class components of the Java2 architecture
from
Sun Microsystems.
The
term application server has also been applied to various non-J2EE and
non-Java offerings. For example, with the rising popularity of .NET, Microsoft
can claim to deliver an application server. Additional open source and
commercial application servers are available from other vendors. Some examples
are the Base4 Server and Zope. Contrary to prior versions of this entry,
Microsoft's Windows Communication Foundation is not an application server, but
rather a framework for communication (middleware).
Application server products typically bundle
middleware
to enable applications to intercommunicate with various qualities of service —
reliability, security, non-repudiation, and so on. Application servers also
provide an API to programmers, so that they don't have to be concerned with the
operating system or the huge array of interfaces required of a modern web-based
application. Communication occurs through the web in the form of HTML and
XML, as a link to
various
databases, and, quite often, as a link to systems and devices ranging from
huge legacy applications to small information devices, such as an atomic clock
or a home appliance. Portals are a
very common application server mechanism by which organizations can manage
information. They provide a single point of entry for all users, they can access
Web
services transparently from any device, and they are highly flexible.
Portals can work inside or outside of the organization, and they can attach
themselves to any part of it.
This term is widely used as a
buzzword in
the following fields:
 |
Distributed computing — denoting a computer running some part of a
distributed computation task |
 |
Software components — denoting a "component farm", which is a computer
loaded with software components, ready to answer calls for usage
|
 |
Web services — denoting a machine running applications which will answer
interface calls over HTTP in an XML format |
Artifact -
Spurious effects or imperfections
introduced into a signal as a result of digital signal processing. An
unintended, unwanted visual abbreviation in a video image.
Aspect ratio - The ratio of the width of an image to its height. For
television, this is typically 4:3.
ASF -
Active Streaming Format. A
Microsoft file format for digital video playback over the Internet, or on a
standalone computer. Kind of a wrapper around any of a number of compression
types, including MPEG. Part of Netshow, a proprietary streaming media solution
from Microsoft. Biggest competitor is Real Networks. While this 'wrapper'
support many standard formats, ASF files are themselves proprietary.
ASIC -
Pronounced ay-sik, and short for Application-Specific
Integrated Circuit, a chip designed for a particular application
(as opposed to the integrated circuits that control functions such as RAM in a
PC). ASICs are built by connecting existing circuit building blocks in new ways.
Since the building blocks already exist in a library, it is much easier to
produce a new ASIC than to design a new chip from scratch. ASICs are commonly used in automotive computers to control
the functions of the vehicle and in PDAs.
ATM
- Asynchronous Transfer Mode. Very high speed transmission technology.
ATM is a high bandwidth, low-delay, connection oriented, cell (or fixed size
packet) switching and multiplexing technique.
When purchasing ATM service,
you generally have a choice of four different types of service:
constant bit rate (CBR):
specifies a fixed bit rate so that data is sent in a steady stream. This is
analogous to a leased line. variable bit rate (VBR):
provides a specified throughput capacity but data is not sent evenly. This is a
popular choice for voice and videoconferencing data.
available bit rate (ABR):
provides a guaranteed minimum capacity but allows data to be bursted at
higher capacities when the network is free.
unspecified bit rate (UBR): does not guarantee
any throughput levels. This is used for applications, such as file transfer,
that can tolerate delays.
ATM
Adaptation Layer (AAL) - AAL1, AAL2, AAL3/4, and AAL5
are
the different types of the ATM adaptation Layer.
ATSC - Advanced Television
Systems Committee. Formed by the Joint Committee on Inter-Society
Coordination (JCIC) to establish voluntary standards for Advanced TV (ATV)
systems. The ATSC focuses on digital television, interactive systems and
broadband multimedia communications standards. Membership is open to North
and South American including the Caribbean entities.
The
main ATSC standards for DTV are 8-VSB, which is used in the transmission of
video data, MPEG-2 for video signal compression, and Dolby Digital
for audio coding.
AUC -
The
Authentication Centre or AUC is a function to
authenticate each
SIM card
that attempts to connect to the GSM core network (typically when the phone is
powered on). Once the authentication is successful, the HLR is allowed to manage
the SIM and services described above. An
encryption key is also generated that is subsequently used to encrypt all
wireless communications (voice, SMS, etc.) between the
mobile
phone and the GSM core network. If the authentication fails, then no services are possible from that particular
combination of
SIM card and
mobile phone operator attempted. There is an additional form of
identification check performed on the serial number of the
mobile
phone described in the EIR section below, but this is not relevant to the
AUC processing. Proper implementation of security in and around the AUC is a key part of an
operator's strategy to avoid
SIM
cloning. The AUC does not engage directly in the authentication process, but instead
generates data known as triplets for the MSC to use during the procedure.
The security of the process depends upon a shared secret between the AUC and the
SIM called the Ki. The Ki is securely burned into the SIM during manufacture and
is also securely replicated onto the AUC. This Ki is never transmitted between
the AUC and SIM, but is combined with the
IMSI to produce a
challenge/response for identification purposes and an encryption key called Kc
for use in over the air communications.
Audio 1 & 2 Inputs - Regular phono jacks designed to accompany the
S-Video and composite video inputs (respectively); these inputs accept a wide
variety of audio sources.
Audio Buffer - A buffer
in the target system decoder for storage of compressed audio data.
Typically used to hold audio data for synchronization with its corresponding
incoming video data.
Audio Decoder - That
part of a decoder responsible for decompressing the audio bit stream as
specified by Part 3 of the MPEG standard.
Audio Encoder - That
part of an encoder responsible for compressing the audio bit stream as specified
by Part 3 of the MPEG standard.
Audio Input with Loop-Through Output - Regular phono jacks designed to
accompany the SVGA/VGA, S-Video, and composite video inputs. These inputs accept
a wide variety of audio sources.
Audio Masking -
A
compression technique that drops out one audio signal that cannot be perceived
by the human ear because of the presence of another audio signal.
Audio/Video Input Jacks - For fast and easy hookup of peripheral devices
such as VCRs, and laser disc players.
Audio/Video Muting - Automatically detects the loss of RF signal. When
this happens, video defaults to a blue or black background and audio mutes. The
units
automatically return to their original settings when the signal is resumed.
Audio only conference add-ins - The ability to add another site into a
video conference via an audio connection only. This feature uses a regular phone
line connected to the codec to conference in someone who is not near a video
site but needs to be part of the conversation.
Audio Stream -
A bit
sequence of compressed digital audio.
Audio Teleconferencing -
Two-way electronic voice communication between two or more people at two or more
locations.
Auto Power On - Forces the default power setting to the ON position,
preventing sets from being turned off while in use. Additionally, this feature
allows all sets to be controlled from a single circuit breaker and forces the
set to turn back on automatically after a power interruption.
Automatic Mode Detection - This feature allows the television to detect
different video modes, learn screen geometry, and automatically recall screen
settings (this feature along with the ability to adjust horizontal and vertical
scaling, makes your TV display compatible with most computer software platforms.
Autonomous System -
In the Internet,
an autonomous system (AS) is a collection of
IP networks and routers under the control of one entity (or sometimes more)
that presents a common routing policy to the Internet. See
RFC 1930 for additional detail on this updated definition. Originally, the definition required control by a single entity, typically an
Internet service provider or a very large organization with independent
connections to multiple networks, that adhere to a single and clearly defined
routing policy. See
RFC 1771, the original definition (now obsolete) of the
Border Gateway Protocol. The newer definition of
RFC 1930 came into use because multiple organizations can run BGP using
private AS numbers to an ISP that connects all those organizations to the
Internet. Even though there are multiple autonomous systems supported by the
ISP, the Internet only sees the routing policy of the ISP. That ISP must have a
public, registered ASN. A unique AS number (or ASN) is allocated to each AS for use in
BGP routing. With
BGP, AS numbers are important because the ASN uniquely identifies each network
on the internet.
A/V -
Audio/Video.
AVI -
Audio Video Interleaved. A
Microsoft format for digital audio and video playback from Windows 3.1 Somewhat
cross-platform, but mostly a Windows format. Has been replaced by the ASF
format, but still used by some multimedia developers.
BACK TO TOP
B
B2BUA -
A Back-to-back
User Agent is primarily used to interface an
IP Multimedia Subsystem (IMS) network to other networks. The B2BUA acts as a proxy to both ends of a
SIP call. The B2BUA is responsible for
handling all SIP signaling between both ends of the call, from call
establishment to termination. Each call is tracked from beginning to end,
allowing the operators of the B2BUA to offer value-added features to the call. To SIP clients, the B2BUA acts as a User Agent server on one side and as a User
Agent client on the other (back-to-back) side. The basic implementation of a
B2BUA is defined in
RFC 3261. The B2BUA provides the following functionality:
 |
call management (billing, automatic call disconnection, call transfer, etc.)
|
 |
network interworking (perhaps with protocol adaptation) |
 |
hiding of network internals (private addresses, network topology, etc.)
|
Because it maintains call state for all SIP calls it handles, failure of a B2BUA
affects all these calls. A
Signaling gateway, part of a
Session Border Controller, is a good example of a B2BUA.
Banding -
The presence of extraneous lines.
Bandwidth -
A measure of the amount of data
that can fit on a communication channel. In analog communications bandwidth is
the width, typically measured in Hertz (or cycles per seconds), of a frequency
band f2 − f1. In digital communications, bandwidth
is typically measured in bits per second. The higher the bandwidth, the
sharper the picture; low bandwidth can cause a fuzzy picture. The
following is a list of devices bandwidth:
|
CONNECTION |
BITS |
BYTES |
Modems
(note: serial, 1 start
bit, 8 data bits, 1 stop bit: therefore 10 bits needed to transmit each
byte. The exception is 110 baud which uses 2 stop bits or 11 bits per
byte.)
|
| Modem 110 baud |
110 bit/s |
10 B/s |
| Modem 300 baud (V.21) |
300 bit/s |
30 B/s |
| Modem Bell 103 (Bell
103) |
300 bit/s |
30 B/s |
| Modem 1200 (V.22) |
1.2 kbit/s |
120 B/s |
| Modem Bell 212A (Bell
212A) |
1.2 kbit/s |
120 B/s |
| Modem 2400 (V.22bis) |
2.4 kbit/s |
240 B/s |
| Modem 9600 (V.32) |
9.6 kbit/s |
960 B/s |
| Modem 14.4k (V.32bis) |
14.4 kbit/s |
1,440 B/s |
| Modem 19.2k
(V.32terbo) |
19.2 kbit/s |
1,920 B/s |
| Modem 28.8k (V.34) |
28.8 kbit/s |
2,880 B/s |
| Modem 33.6k
(V.34plus/V.34bis) |
33.6 kbit/s |
3,360 B/s |
| Modem 56k* (V.90)
(downstream) |
56.0 kbit/s |
5.6 kB/s |
| Modem 56k* (V.90)
(upstream) |
33.6 kbit/s |
3.36 kB/s |
| Modem 56k* (V.92)
(downstream) |
56.0 kbit/s |
5.6 kB/s |
| Modem 56k* (V.92)
(upstream) |
48.0 kbit/s |
4.8 kB/s |
ISDN
|
| 64k ISDN |
64.0 kbit/s |
8 kB/s |
| 128k dual-channel ISDN |
128.0 kbit/s |
16 kB/s |
| ISDN-PRI 24x64K |
1536 kbit/s |
192 kB/s |
| ISDN-PRA 30x64K |
1920 kbit/s |
240 kB/s |
Computer interfaces
(internal)
|
| ISA 08-Bit/4.77MHz |
38.66 Mbit/s |
4.83 MB/s |
| ISA 16-Bit/8.33MHz |
134.66 Mbit/s |
16.85 MB/s |
| PCI 32-bit/33MHz |
1066.66 Mbit/s |
133.33 MB/s |
| PCI Express (x1 link) |
2500 Mbit/s |
250 MB/s |
| PCI 64-bit/33MHz |
2133.33 Mbit/s |
266.66 MB/s |
| PCI 32-bit/66MHz |
2133.33 Mbit/s |
266.66 MB/s |
| AGP 1x |
2133.33 Mbit/s |
266.66 MB/s |
| AGP 2x |
4266.66 Mbit/s |
533.33 MB/s |
| PCI 64-bit/66MHz |
4266.66 Mbit/s |
533.33 MB/s |
| PCI-X DDR 16-bit |
4266.66Mbit/s |
533.33 MB/s |
| PCI Express (x4 link) |
10000 Mbit/s |
1000 MB/s |
| AGP 4x |
8533.33 Mbit/s |
1066.66 MB/s |
| PCI-X 133 |
8533.33 Mbit/s |
1066.66 MB/s |
| PCI-X QDR 16-bit |
8533.33 Mbit/s |
1066.66 MB/s |
| InfiniBand |
10.00 Gbit/s |
1.25 GB/s |
| PCI Express (x8 link) |
20.00 Gbit/s |
2.0 GB/s |
| AGP 8x |
17.066 Gbit/s |
2.133 GB/s |
| PCI-X DDR |
17.066 Gbit/s |
2.133 GB/s |
| PCI Express (x16 link) |
40.0 Gbit/s |
4.0 GB/s |
| PCI-X QDR |
34.133 Gbit/s |
4.266 GB/s |
| HyperTransport
(800MHz, 16-pair) |
51.2 Gbit/s |
6.4 GB/s |
| HyperTransport (1GHz,
16-pair) |
64.0 Gbit/s |
8.0 GB/s |
Note that PCI Express
lanes use a 10b/8b encoding scheme
Computer interfaces
(drive)
|
| SCSI 1 |
12.0 Mbit/s |
1.5 MB/s |
| Fast SCSI 2 |
80 Mbit/s |
10 MB/s |
| Fast Wide SCSI 2 |
160 Mbit/s |
20 MB/s |
| Ultra DMA ATA 33 |
264 Mbit/s |
33 MB/s |
| Ultra Wide SCSI 40 |
320 Mbit/s |
40 MB/s |
| Ultra DMA ATA 66 |
528 Mbit/s |
66 MB/s |
| Ultra-2 SCSI 80 |
640 Mbit/s |
80 MB/s |
| Ultra DMA ATA 100 |
800 Mbit/s |
100 MB/s |
| Ultra DMA ATA 133 |
1064 Mbit/s |
133 MB/s |
| Serial ATA (SATA-150) |
1200 Mbit/s |
150 MB/s |
| Ultra-3 SCSI 160 |
1280 Mbit/s |
160 MB/s |
| Fiber Channel |
800 or 1600 Mbit/s |
100 or 200 MB/s |
| Serial ATA (SATA-300) |
2400 Mbit/s |
300 MB/s |
| Ultra-320 SCSI |
2560 Mbit/s |
320 MB/s |
| Ultra-640 SCSI |
5120 Mbit/s |
640 MB/s |
Computer interfaces
(external)
|
| Serial RS-232 commonly |
9.6 kbit/s |
960 B/s |
| Serial RS-232 max |
230.4 kbit/s |
23.0 kB/s |
| USB Low Speed |
1536 kbit/s |
192 kB/s |
| Parallel (Centronics) |
8.0 Mbit/s |
1.0 MB/s |
| Serial RS-422 max |
10.0 Mbit/s |
1.25 MB/s |
| USB Full Speed |
12.0 Mbit/s |
1.5 MB/s |
| FireWire (IEEE 1394)
100 |
100 Mbit/s |
12.5 MB/s |
| FireWire (IEEE 1394)
200 |
200 Mbit/s |
25 MB/s |
| FireWire (IEEE 1394)
400 |
400 Mbit/s |
50 MB/s |
| USB Hi-Speed |
480 Mbit/s |
60 MB/s |
| FireWire (IEEE 1394b)
800 |
800 Mbit/s |
100 MB/s |
Wireless
|
| IrDA-Control |
72 kbit/s |
9 kB/s |
| IrDA-SIR |
115.2 kbit/s |
14 kB/s |
| 802.15.4 (2.4GHz) |
250 kbit/s |
31.25 kB/s |
| Bluetooth 1.1 |
1 Mbit/s |
125 kB/s |
| 802.11 legacy 0.125 |
2 Mbit/s |
250 kB/s |
| Bluetooth 2 |
3 Mbit/s |
375 kB/s |
| IrDA-FIR |
4 Mbit/s |
500 kB/s |
| RONJA free source
optical wireless |
10.00 Mbit/s |
1.25 MB/s |
| 802.11b DSSS 0.125 |
11 Mbit/s |
1.375 MB/s |
| 802.11b+ non-standard
DSSS 0.125 |
44.0 Mbit/s |
5.5 MB/s |
| 802.11a 0.75 |
54.00 Mbit/s |
6.75 MB/s |
| 802.11g DSSS 0.125 |
54.00 Mbit/s |
6.75 MB/s |
| 802.11n |
540 Mbit/s |
67.5 MB/s |
Mobile telephone
interfaces
|
| GSM CSD |
2400 to 14400 bit/s |
300 to 1800 B/s |
| HSCSD upstream |
14.4 kbit/s |
1800 B/s |
| HSCSD downstream |
43.2 kbit/s |
5.4 kB/s |
| GPRS upstream |
28.8 kbit/s |
3.6 kB/s |
| GPRS downstream |
57.6 kbit/s |
7.2 kB/s |
| UMTS downstream |
1920 kbit/s |
240 kB/s |
Wide area network
|
| DS0 |
64 kbit/s |
8 kB/s |
| Satellite Internet
upstream |
64kbit/s to 1Mbit/s |
8 kB/s to 128 kB/s |
| Satellite Internet
downstream |
128kbit/s to 16Mbit/s |
16kB/s to 2 MB/s |
| Frame Relay |
8 kbit/s to 45 Mbit/s |
1 kB/s to 5.625 MB/s |
| G.SHDSL |
2.3040 Mbit/s |
0.288 MB/s |
| SDSL |
64 kbit/s to 4.608
Mbit/s |
8 kB/s to 0.576 MB/s |
| G.Lite (aka ADSL Lite)
upstream |
512 kbit/s |
64 kB/s |
| G.Lite (aka ADSL Lite)
downstream |
1.5 Mbit/s |
192 kB/s |
| ADSL upstream |
64 kbit/s to 1024
kbit/s |
8 kB/s to 128 kB/s |
| ADSL downstream |
256 kbit/s to 8 Mbit/s |
32 kB/s to 1 MB/s |
| ADSL2 upstream |
64 kbit/s to 3.5
Mbit/s |
8 kB/s to 448 kB/s |
| ADSL2 downstream |
256 kbit/s to 12
Mbit/s |
32 kB/s to 1.5 MB/s |
| ADSL2Plus upstream |
64 kbit/s to 3.5
Mbit/s |
8 kB/s to 448 kB/s |
| ADSL2Plus downstream |
256 kbit/s to 24
Mbit/s |
32 kB/s to 3.0 MB/s |
| DOCSIS (Cable Modem)
upstream |
128 kbit/s to 8 Mbit/s |
16 kB/s to 1 MB/s |
| DOCSIS (Cable Modem)
downstream |
384 kbit/s to 24
Mbit/s |
48 kB/s to 3 MB/s |
| DS1/T1 |
1.544 Mbit/s |
192.5 kB/s |
| E1 |
2.048 Mbit/s |
256 kB/s |
| E2 |
8.448 Mbit/s |
1.056 MB/s |
| E3 |
34.368 Mbit/s |
4.296 MB/s |
| DS3/T3 ('45 Meg') |
44.736 Mbit/s |
5.5925 MB/s |
| STS-1/EC-1/OC-1/STM-0 |
51.840 Mbit/s |
6.48 MB/s |
| VDSL (symmetry
optional) |
12 Mbit/s to 100
Mbit/s |
1.5 MB/s to 12.5 MB/s |
| VDSL2 (symmetry
optional) |
12 Mbit/s to 250
Mbit/s |
1.5 MB/s to 31.25 MB/s |
| LR-VDSL2 (4 to 5 km
[long-]range) (symmetry optional) |
1 Mbit/s to 4 Mbit/s |
128 kB/s to 512 kB/s |
| OC-3/STM-1 |
155.52 Mbit/s |
19.44 MB/s |
| OC-12/STM-4 |
622.08 Mbit/s |
77.76 MB/s |
| OC-48/STM-16 |
2.448320 Gbit/s |
306.104 MB/s |
| OC-192/STM-64 |
9.953280 Gbit/s |
1.24416 GB/s |
| 10 Gigabit Ethernet
WAN PHY |
9.953280 Gbit/s |
1.24416 GB/s |
| 10 Gigabit Ethernet
LAN PHY |
10 Gbit/s |
1.25 GB/s |
| OC-768/STM-256 |
39.813120 Gbit/s |
4.97664 GB/s |
Local area network
|
| LocalTalk |
230.4 kbit/s |
28.8 kB/s |
| ARCNET (Standard) |
2.5 Mbit/s |
0.3125 MB/s |
| Token Ring (Original) |
4.16 Mbit/s |
0.52 MB/s |
| Ethernet (10base-X) |
10 Mbit/s |
1.25 MB/s |
| Token Ring (Later) |
16 Mbit/s |
2.0 MB/s |
| Fast Ethernet
(100base-X) |
100 Mbit/s |
12.5 MB/s |
| FDDI |
100 Mbit/s |
12.5 MB/s |
| Gigabit Ethernet
(1000base-X) |
1 Gbit/s |
125 MB/s |
| 10 Gigabit Ethernet
(10Gbase-X) |
10 Gbit/s |
1250 MB/s |
Memory Interconnect
Buses / RAM
|
| PC66 SDRAM |
4264 Mbit/s |
533 MB/s |
| PC100 SDRAM |
6400 Mbit/s |
800 MB/s |
| PC133 SDRAM |
8528 Mbit/s |
1066 MB/s |
| PC1600 DDR-SDRAM |
12.8 Gbit/s |
1.6 GB/s |
| PC2100 DDR-SDRAM |
16.8 Gbit/s |
2.1 GB/s |
| PC2700 DDR-SDRAM |
21.6 Gbit/s |
2.7 GB/s |
| PC3200 DDR-SDRAM |
25.6 Gbit/s |
3.2 GB/s |
| PC800 RDRAM
(single-channel) |
12.8 Gbit/s |
1.6 GB/s |
| PC800 RDRAM
(dual-channel) |
25.6 Gbit/s |
3.2 GB/s |
| PC1066 RDRAM
(single-channel) |
16.8 Gbit/s |
2.1 GB/s |
| PC1066 RDRAM
(dual-channel) |
33.6 Gbit/s |
4.2 GB/s |
| PC1200 RDRAM
(single-channel) |
19.2 Gbit/s |
2.4 GB/s |
| PC1200 RDRAM
(dual-channel) |
38.4 Gbit/s |
4.8 GB/s |
| PC2-3200 DDR2-SDRAM |
25.6 Gbit/s |
3.2 GB/s |
| PC2-4200 DDR2-SDRAM |
34.136 Gbit/s |
4.267 GB/s |
| PC2-5400 DDR2-SDRAM |
42.664 Gbit/s |
5.333 GB/s |
| PC2-6400 DDR2-SDRAM |
51.2 Gbit/s |
6.4 GB/s |
| PC2-8500 DDR2-SDRAM |
68.264 Gbit/s |
8.533 GB/s |
| 2005-Feb Prototype
DDR3-SDRAM |
~68.224 Gbit/s |
~8.528 GB/s |
Bandwidth On Demand - using
telecommunications equipment to "dial-up" the bandwidth you need. In
circuit switched networks, the use of Inverse Multiplexers (or IMUX) to combine
2 or more fixed bit rate channels (56/64Kbps channels) is an example of
bandwidth on demand. Bandwidth on demand is typically done with digital
circuits (digital circuits are easier to combine). In packet or cell
switched networks (e.g. ATM), the same concept applies, but the method of
achieving bandwidth on demand is different.
Baseband -
All signals are comprised of a whole range of different
frequencies added up together. In telecommunications in
particular, it is often the case that those parts of the signal
which are at low frequencies are 'copied' up to higher
frequencies for transmission purposes, since there are few
communications media that will pass low frequencies without
distortion. Then, the original, low frequency components, are
referred to as the baseband signal. Typically, the new, high
frequency copy is referred to as the 'RF' (radio frequency)
signal, although it need not be at the particular frequencies
set aside for radio.
More precisely, a
signal "at baseband" is usually considered to comprise all
relevant frequencies from 0Hz up to the highest frequency
component in the signal with significant power. The signal is
then usually modulated in order that it may be transmitted.
Modulation results in shifting the signal up to much higher (RF)
frequencies than it originally spanned. A key consequence of
this process is that, usually, the range of frequencies the
signal spans (its spectral bandwidth) is doubled. Thus, the RF
bandwidth of a signal is usually twice its baseband bandwidth.
Steps may be taken to reduce this effect, such as filtering the
RF signal prior to transmission.
BCP - The Bridge Control
Protocol is a support feature
described in RFC 3518. The Cisco implementation of BCP is a VLAN infrastructure
that does not require the use of sub-interfaces to group Ethernet 802.1Q trunks
and the corresponding PPP links. This approach enables users to process VLAN
encapsulated packets without having to configure sub-interfaces for every
possible VLAN configuration.
BGAN -
Broadband Global Area Network is
a future Inmarsat network comprising satellites and land earth stations; permits
data speeds up to 432 kbps.
BGP -
The Border Gateway Protocol
is the core routing protocol of the Internet. It works by maintaining a table of
IP networks or 'prefixes' which designate network reachability between
autonomous systems (AS). It is described as a path vector protocol. BGP does not
use technical metrics, but makes routing decisions based on network policies or
rules. BGP version 4, is specified in
RFC 4271 (as per Jan 2006). This RFC
obsoletes RFC 1771.
BGP supports
classless inter-domain routing and uses
route aggregation to decrease the size of routing tables. Since
1994, version four
of the protocol has been in use on the Internet; all previous versions are
considered obsolete.
BGP was created to replace the Exterior Gateway Protocol (EGP)
routing protocol to allow fully decentralized routing in order to allow the
removal of the
NSFNET
Internet backbone network. This allowed the Internet to become a truly
decentralized system. Very large private
IP networks can also make use of BGP; an example would be the joining of a
number of large
Open Shortest Path First (OSPF) networks where OSPF by itself would not
scale to size. Another reason to use BGP would be
multi-homing a network for better redundancy. Most Internet users do not use BGP directly. However, since most
Internet service providers must use BGP to establish routing between one
another, it is one of the most important protocols of the Internet.
Compare and
contrast this with
Signaling System 7, which is the inter-provider core call setup protocol on
the PSTN. A BGP peer uses a simple Finite State Machine (FSM) to make
decisions in its operations with other BGP peers. The FSM consists of six
states: Idle, Connect, Active, OpenSent, OpenConfirm, and Established. A BGP
peer will transition the TCP connection to another peer between these states as
it attempts to establish and maintain a session with that peer. BGP uses the following criteria to determine the path to use (from top to
bottom): 1-) An explicit route (i.e. not a default route) for the next-hop
router must exist in the routing table. 2-) Prefer the path with the
highest weight (Only on Cisco routers). 3-) Prefer the path with the
highest local preference. 4-) Prefer any BGP originated on this router.
5-) Prefer the route with the shortest AS path. 6-) prefer the route with
the lowest origin (IGP
<
EGP < ?). 7-) Prefer the path with the lowest MED (Multi exit
discriminator). 8-) Prefer external paths to internal paths. 9-)
Prefer the path with the lowest IGP metric to the next hop. 10-) If all
remaining paths are external choose the oldest one. 11-) Prefer the next
hop router with the lowest BGP ID. BGP problems and mitigation: 1-) A
feature known as "damping" is built into BGP to mitigate the effects of route
flapping. Flapping of routes can be caused by WAN / WLAN links or physical
interfaces mending and breaking or by misconfigured or mismanaged routers.
Without damping, routes can be injected and withdrawn rapidly from routing
tables, possibly causing a heavy processing load on routers thus affecting
overall routing stability. 2-) One of the largest problems faced by BGP,
and indeed the Internet infrastructure as a whole, comes from the growth of the
Internet routing table.
BI - Business Intelligence
is a broad category of business processes, application software and other
technologies for gathering, storing, analyzing, and providing access to data to
help users make better business decisions.
Most
companies collect a large amount of data from their business operations. To keep
track of that information, a business and would need to use a wide range of
software programs , such as Excel, Access and different database applications
for various departments throughout their organization. Using multiple software
programs makes it difficult to retrieve information in a timely manner and to
perform analysis of the data. The term Business Intelligence (BI)
represents the tools and systems that play a key role in the strategic planning
process of the corporation. These systems allow a company to gather, store,
access and analyze corporate data to aid in decision-making. Generally these
systems will illustrate business intelligence in the areas of customer
profiling, customer support, market research, market segmentation, product
profitability, statistical analysis, and inventory and distribution analysis to
name a few.
BICC -
The Bearer Independent Call Control is a signaling protocol based
on N-ISUP that is used to support narrowband
ISDN service over a
broadband backbone network without interfering with interfaces to the existing
network and end-to-end services. Specified by the
International Telecommunications Union - Telecommunications Standardization
Sector (ITU-T) in recommendation Q.1901, BICC was designed to be fully
compatible with existing networks and any system capable of carrying voice
messages. BICC supports narrowband ISDN services independently of bearer and signaling
message transport technology. ISUP messages carry both call control and bearer
control information, identifying the physical bearer circuit by a Call Instance
Code (CIC).
The narrowband ISDN service also uses a CIC of a lower range referred to as the
Circuit Identification Code. However, CIC is specific to
time-division multiplexed (TDM) networks. BICC was developed to be
interoperable with any type of bearer, such as those based on asynchronous
transfer mode (ATM) and Internet Protocol (IP) technologies, as well as TDM.
BICC separates call control and bearer connection control, transporting BICC
signaling independently of bearer control signaling. The actual bearer transport used is transparent to the BICC signaling protocol -
BICC has no knowledge of the specific bearer technology, which is referenced in
the binding information.
The ITU announced the completion of the second set of BICC protocols (BICC
Capability Set 2, or CS 2) in July 2001; these are expected to help move
networks from the current model - which is based on public-switching systems -
to a server-based model. The BICC deployment architecture comprises a server, proxy, and a media gateway
to support the current services over networks based on circuit-switched, ATM,
and Internet Protocol (IP) technologies, including third-generation wireless. According to the ITU, the completion of the BICC protocols is a historic step
toward broadband multimedia networks, because it will enable the seamless
migration of circuit-switched TDM networks to high-capacity broadband multimedia
networks. The Third Generation Partnership Project (3GPP) has included BICC CS 2 in the
Universal Mobile Telecommunications Service (UMTS) release 4. Among the future
ITU-T plans for BICC are the inclusion of more advanced service support and more
utilization of proxies, such as the
Session Initiation Protocol (SIP) proxy.
Bit rate - The
speed of a communication channel.
typically expressed in
bits per seconds (bps).
For example modems that follow the
V.90 standard, have a bit rate of 56kbps (56,000 bits per second).
Block -
An 8
x 8 set of pixels. It is the most basic element of a video picture, and is
represented as a set of values that defines either a luminance (Y) block or a
chrominance (Cb or Cr) block.
Block-based Motion Compensation -
A technique used to reduce
temporal redundancy.
BPM - Business
Process Management, is the practice of improving the efficiency and
effectiveness of any organization by automating the organization's business
processes. BPM used to be also know as Business Process Reengineering (BPR).
Many companies have business processes that are unique to its business model.
Since these processes tend to evolve over time as the business reacts to market
conditions, the BPM solution you choose must be easily adaptable to the
new conditions and requirements and continue to be a perfect fit for the
company. In order to use BPM effectively, organizations must stop focusing
exclusively on data and data management, and adopt a process-oriented approach
that makes no distinction between work done by a human and a computer.
BRA -
Basic Rate Access. A European term for BRI.
BRI - Basic Rate Interface. BRI is an ISDN interface with 2B+D
channels. Each channel is 64Kbps full duplex ideal for isochronous traffic
like voice and video. See ISDN BRI.
Bridge -
1. Device used to
interconnect three or more telecommunications channels such as telephone lines,
to permit simultaneous, two-way communication among all points that have been
interconnected. 2. A device that connects one local area network (LAN) to
another local area network that uses the same protocol (for example, Ethernet or
Token Ring). If a data unit on one LAN is intended for a destination on an
interconnected LAN, the bridge forwards the data unit to that LAN; otherwise, it
passes it along on the same LAN.
Broadband - Communications
which are capable of carrying a wide range of frequencies. Broadcast television,
cable television, microwave, and satellite are examples of broadband
technologies. A facility or circuit that has bandwidth in excess of that
required for high grade voice communication. Generally refers to
transmission of data over numerous frequencies.
Broadcasting - is the
distribution of audio and video signals (programs) to a number of recipients
("listeners" or "viewers") that belong to a large group. This group may be the
public in general, or a relatively large audience within the public. Thus, an
Internet channel may distribute text or music world-wide, while a public address
system in (for example) a workplace may broadcast very limited ad hoc soundbites
to a small population within its range.
Brouter - a combined bridge and router.
Bus - 1) A collection of
wires through which
data is transmitted from one part of a computer to another. You can think of a
bus as a highway on which data travels within a computer. When used in reference
to personal computers, the term bus usually refers to internal bus.
This is a bus that connects all the internal computer components to the
CPU and main memory.
There's also an expansion bus that enables expansion boards to access the CPU
and memory. All buses consist of two parts -- an address bus and a data
bus. The data bus transfers actual data whereas the address bus transfers
information about where the data should go. The size of a bus, known as
its width, is important because it determines how much data can be
transmitted at one time. For example, a 16-bit bus can transmit 16 bits of data,
whereas a 32-bit bus can transmit 32 bits of data. Every bus has a clock
speed measured in MHz. A fast bus allows data to be transferred faster, which
makes applications
run faster. On PCs, the
old ISA bus is being replaced by faster buses such as PCI. Nearly all PCs
made today include a local bus for data that requires especially fast transfer
speeds, such as video data. The local bus is a high-speed pathway that connects
directly to the processor. 2) In networking, a bus is a central cable that
connects all devices on a local-area network (LAN). It is also called the
backbone.
Business performance management
is a software-oriented business intelligence system that some see as the new
generation of business intelligence, though the terms are used interchangeably
by most in the industry.
Business Process -
A business process is a
recipe for
achieving a
commercial result. Each
business
process has inputs, method and outputs. The inputs are a pre-requisite that must
be in place before the method can be put into practice. When the method is
applied to the inputs, then certain outputs will be created. A business process is a collection of related structural activities that
produce something of value to the organization, its stake holders or its
customers. It is, for example, the process through which an organization
realizes its services to its customers. A business process can be part of a larger, encompassing process and can include
other business processes that have to be included in its method. In that context
a business process can be viewed at various levels of granularity. The linkage
of business process with value generation leads some practitioners to view
business processes as the workflows which realize an organization's
use cases. A business process can be thought of as a
cookbook
for running a
business; "Answer the phone", "place an order", "produce an invoice" might
all be examples of a Business Process. A business process is usually the result of a
business process design or
business process reengineering activity.
BACK TO TOP
C
CA -
Conditional Access is a technology used to control access to digital television
(DTV) services to authorized users by encrypting the transmitted programming. CA
has been used for years for pay-TV services.
CAP -
CAMEL Application Part
is based on Intelligent Network (IN) capability sets with enhancements specific
to mobile domain. This unique feature enables the implementation of the Virtual
Home Environment (VHE) for a mobile subscriber. The CAMEL Application Part (CAP)
stack provides service control for voice & data services and IP multimedia
sessions. 3GPP
TS 29.078 specification.
CAMEL -
Customized Applications for Mobile networks Enhanced Logic is a set of GSM
standards designed to work on a
GSM core network. They allow an operator to define services over and above
standard
GSM
services. The CAMEL architecture is based on the
Intelligent Network (IN) standards, and uses the
CAP protocol. Many services can be created using CAMEL, and it is particularly effective in
allowing these services to be offered when a subscriber is
roaming, like
for instance no-prefix dialing (the number the user dials is the same no matter
the country where the call is placed) or seamless
MMS message access
from abroad.
Carrier Wave - is a
waveform (usually sinusoidal) that is modulated (modified) to represent the
information to be transmitted. This carrier wave is usually of much higher
frequency than the modulating signal (the signal which contains the
information). The reason for this is that it is much easier to transmit a
signal of higher frequency, and the signal will travel further.
Carrier waves are used when
transmitting radio signals to a radio
receiver. Frequency modulation (FM) and amplitude modulation (AM) signals are
both transmitted with the help of carrier frequencies. The frequency for a given
radio station is actually the carrier wave's center frequency. In
telecommunication, the term carrier (cxr) or carrier wave has the following
meanings: a waveform suitable for modulation by an information-bearing signal,
an un-modulated emission. Note: The carrier is usually a sinusoidal wave
or a uniform or predictable series of pulses. Synonym: carrier wave, sometimes
employed as a synonym for a carrier system, or a synonym for a
telecommunications provider company (operator), such as a common carrier
CDMA - Code Division
Multiple Access is a spread-spectrum technology that spreads multiple
conversations across a wide segment of the spectrum as opposed to splitting a
channel into time slots. With CDMA, unique digital codes are used to
differentiate subscribers that are simultaneously using the same spectrum. As a multiplexing scheme,
CDMA is any use of
any form of
spread spectrum by multiple transmitters to send to the same receiver on the
same frequency channel at the same time without harmful interference. Other
widely used multiple access techniques are Time Division Multiple Access (TDMA)
and Frequency Division Multiple Access (FDMA).
In these three schemes, receivers discriminate among various signals by the use
of different codes, time slots and frequency channels, respectively.
CdmaOne -
The original CDMA as first
deployed by Qualcomm is the technology that is in use today in all CDMA networks
that have not been upgraded to cdma2000. CdmaOne is 10–12 times more efficient
than analog and 4–5 times more efficient than GSM. CDMA makes use of 1.25-MHz
radio channels. In U.S. cellular systems, 30-KHz channels are aggregated to
provide 1.25-MHz channels.
Cdma2000 1x -
Cdma2000 1x, the next generation of CDMA, supports between 1.5 and 2 times the
number of voice channels as a standard CDMA system as well as 144-Kbps
packet-data services. Cdma2000 1x is 21 times more efficient than analog
cellular and 4 times more efficient than TDMA networks. (Cdma2000 1x data speeds
will increase from 144 Kbps to 288 Kbps by the end of 2002.)
Cdma2000 1x EV-DO -
This is the next EVolution of
cdma2000. “DO” indicates Data-Only and this system is capable of data speeds of
up to 2.4 Mbps. This upgrade to cdma2000 requires a second 1.25-MHz channel that
is used exclusively for data. Most cdma2000 network operators are expected to
combine 1x and 1x EV-DO channels in their systems to provide varying voice and
data capacities as required by customer demand.
Cdma2999 1x EV-DV -
Motorola has been leading the standards effort. The technology is being
specified to provide data-rate speeds of 1.2 Mbps for mobile users, with peak
data speeds up to 5.2 Mbps for stationary users. This standard will also support
voice in addition to data.
Cdma2000 3x -
The 3x designation was created because some countries specify that new 3G
technologies must use at least 5 MHz of spectrum. Cdma2000 3x combines 3
cdma2000 1x carriers to be used within 5 MHz of wireless spectrum.
CDPD -
Cellular Digital Packet Data (CDPD) is an add-on technology that enables
first-generation analog systems to provide packet data. CDPD is an IP network
that runs at 19.2 Kbps with throughputs typically less than 10 Kbps. CDPD has
been implemented in the U.S. by AT&T Wireless and Verizon Wireless.
Channel -
Channel, in communications
(sometimes called communications channel), refers to the medium through which
information is transmitted from a sender (or transmitter) to a receiver. In
practice, this can mean many different methods of facilitating communication,
including: A connection between initiating and terminating nodes of a circuit, a
single path provided by a transmission medium via either physical separation,
such as by multipair cable or electrical separation, such as by frequency- or
time-division multiplexing, A path for conveying electrical or
electromagnetic signals, usually distinguished from other parallel paths, the
portion of a storage medium, such as a track or a band, that is accessible to a
given reading or writing station or head, in a communications system, the part
that connects a data source to a data sink, a specific radio frequency or band
of frequencies, usually in conjunction with a predetermined letter, number, or
codeword, and allocated by international agreement. For example 802.11b consists
of unlicensed channels 1-13 from 2412MHz to 2484MHz in 5MHz steps, in
particular, a television channel. Examples include North American TV Channel 2 =
55.25MHz, Channel 13 = 211.25MHz, a room in the Internet Relay Chat (IRC)
network, in which participants can communicate with each other. In
wireless terminology, a channel is the amount of wireless spectrum occupied by a
specific technology implementation. For cellular, there is a transmit side and a
receive side. For example, a 5-MHz channel uses 5 MHz to transmit and 5 MHz to
receive for a total of 10 MHz of wireless spectrum.
Channel Blanking - This feature allows the video to be programmed blank
to a black background allowing music or other audio content to be assigned to
that channel.
Channel Captioning & Channel Guide - Allows labeling of channel
identification information and with the press of a button, displays that
information onscreen in a directory format.
CIDR
-
Classless Inter-Domain Routing (CIDR, pronounced "cider" or "cedar"), introduced
starting in 1993,
is the latest refinement to the way
IP
addresses are interpreted. It replaced the previous generation of IP address
syntax,
classful networks. It allowed increased flexibility when dividing ranges of
IP addresses into separate networks. It thereby promoted: 1-) More efficient use
of increasingly scarce IPv4 addresses. 2-) Greater use of hierarchy in
address assignments (prefix aggregation), lowering the overhead of the
Internet-wide routing. CIDR is principally a bitwise, prefix-based standard for
the interpretation of IP addresses. It facilitates routing by allowing blocks of
addresses to be grouped together into single routing table entries. These
groups, commonly called CIDR blocks, share an initial sequence of bits in
the binary representation of their IP addresses. An IP address is part of a CIDR
block, and is said to match the CIDR prefix if the initial N bits of the
address and the CIDR prefix are the same. For example A.B.C.D/N: the
number following the slash is the prefix length, the number of shared
initial bits, counting from the left-hand side of the address. With IPv6
addresses, the prefix length can range from 0 to 128. The prefix is written as
an IPv6 address, followed by a slash and the number of significant bits.
CIF -
A video format that supports both
NTSC and PAL signals. CIF is part of the ITU H.261 videoconferencing standard.
It specifies a data rate of 30 frames per second (fps), with each frame
containing 288 lines and 352 pixels per line.
CLI - Command Line Interface. CLI operating systems are being
replaced, in most applications, by the GUI operating system (e.g. Microsoft
Windows).
Clone Programming - With Clone Programming capability, you can program
one television, download all the information into the Philips Clone Programming
Box, and upload it into all the other units. This ensures total uniformity from
set to set and saves a tremendous amount of time.
CODEC -
Stands for CODer/DECoder (a
telecommunications term) or COmpressing/DECompressing (a computer term). A
telecom codec converts analog voice signal to digital form and vise versa.
In the computer world, a codec is used in digital video and stereo audio.
CODEC Conversion -
back-to-back transfer of an analog signal from one CODEC into another CODEC in
order to convert from one proprietary coding scheme (e.g. used by CLI) to
another (e.g. used by PictureTel, VTel, etc.).
COFDM - Coded Orthogonal Frequency Division Multiplexing. COFDM
also sometimes called discrete
multitone modulation (DMT), is a modulation scheme that divides
a single digital signal across 1,000 or more signal carriers simultaneously. The
signals are sent at right angles to each other (hence, orthogonal) so they do
not interfere with each other. COFDM is used predominately in Europe and is
supported by the Digital Video Broadcasting (DVB) set of standards. In the U.S.,
the Advanced Television Standards Committee (ATSC) has chosen 8-VSB (8-level
Vestigial Sideband) as its equivalent modulation standard.
Comb Filter - Provides a better method of isolating luminance and
chrominance thereby producing better picture quality.
Composite Video Input - A typical phono jack makes the attachment of any
VCR, camcorder, Web browsers, or video game console, quick and easy for
excellent picture presentation.
Composite Video Loop-Through Input/Output - A typical phono jack makes
the attachment of any VCR, camcorder, Laser Disc player, Web browser, or video
game console, quick and easy for excellent picture presentation.
Configuration Management -
In
IT and
telecommunications, the term configuration management or configuration control has the following meanings:
-
The management of security features and assurances
through control of changes made to hardware, software, firmware,
documentation, test, test fixtures and test documentation of an automated
information system, throughout the development and operational life of a
system. Source Code Management or
revision control is part of this.
-
The control of changes--including the recording thereof--that are made to
the hardware, software, firmware, and documentation throughout the system
lifecycle.
-
The control and adaptation of the evolution of complex systems. It is the
discipline of keeping evolving software products under control, and thus
contributes to satisfying quality and delay constraints. Software
configuration management (or SCM) can be divided into two areas. The first
(and older) area of SCM concerns the storage of the entities produced during
the software development project, sometimes referred to as component
repository management. The second area concerns the activities performed for
the production and/or change of these entities; the term engineering support
is often used to refer this second area.
-
After establishing a configuration, such as that of a telecommunications or
computer system, the evaluating and approving changes to the configuration
and to the interrelationships among system components.
-
In distributed-queue dual-bus (DQDB) networks, the function that ensures the
resources of all nodes of a DQDB network are configured into a correct
dual-bus topology. The functions that are managed include the head of bus,
external timing source, and default slot generator functions.
CORBA - In
computing, Common Object Request Broker Architecture (CORBA) is a standard for
software componentry, created and controlled by the Object Management Group
(OMG). It defines APIs, communication protocol, and object/service information
models to enable heterogeneous applications written in various languages running
on various platforms to interoperate. CORBA therefore provides platform and
location transparency for sharing well-defined objects across a distributed
computing platform. In a general sense CORBA “wraps” code written in some
language into a bundle containing additional information on the capabilities of
the code inside, and how to call it. The resulting wrapped objects can then be
called from other programs (or CORBA objects) over the network. In this sense,
CORBA can be considered as a machine-readable documentation format, similar to a
header file but with considerably more information. CORBA uses an
interface definition language (IDL) to specify the interfaces that objects will
present to the world. CORBA then specifies a “mapping” from IDL to a specific
implementation language like C++ or Java. This mapping precisely describes how
the CORBA data types are to be used in both client and server implementations.
Standard mappings exist for Ada, C, C++, Lisp, Smalltalk, Java, and Python.
There are also non-standard mappings for Perl and Tcl implemented by ORBs
written for those languages. The CORBA IDL is only one example of an IDL.
COTS -
commercial off-the-shelf, an
adjective that describes software or hardware products that are ready-made and
available for sale to the general public. For example, Microsoft Office is a
COTS product that is a packaged software solution for businesses. COTS products
are designed to be implemented easily into existing systems without the need for
customization.
Chrominance -
color.
Critical Chain -
Critical
Chain Project Management (CCPM) is based on methods and algorithms developed in
1997 by Eliyahu M. Goldratt. Application of CCPM has been credited with
achieving projects 10% to 50% faster and/or cheaper than the traditional methods
(i.e. CPM, PERT, Gantt, etc.) developed from 1910 to 1950's. The critical
chain is the sequence of both precedence- and resource-dependent terminal
elements that prevents a project from being completed in a shorter time, given
finite resources. If resources are always available in unlimited quantities,
then a project's critical chain is identical to its critical path.
Critical Chain uses Buffer Management as to EVM. The main features that distinguish the critical chain from the critical path
are: 1-) The use of (often implicit) resource dependencies. Implicit means
that they are not included in the project network but have to be identified by
looking at the resource requirements. 2-) Lack of search for an optimum
solution. This means that a "good enough" solution is enough because: A-)As far
as is known, there is no analytical method of finding an absolute optimum (i.e.
having the overall shortest critical chain). B-) The inherent uncertainty
in estimates is much greater than the difference between the optimum and
near-optimum ("good enough" solutions). 3-) The identification and
insertion of buffers: A-) project buffer, B-) feeding buffers, and C-) resource
buffers.
Critical Path -
In
project management, a critical path is the sequence of
project network
terminal elements with the longest overall
duration, determining the shortest time to complete the project. The duration of the critical path determines the duration of the entire project.
Any delay of a terminal element on the critical path directly impacts the
planned project completion date (i.e. there is no
float on the critical path). A project can have several, parallel critical paths. An additional parallel path
through the network with the total durations just shorter than the critical path
is called a sub-critical path. Originally, the critical path method considered only logical
dependencies among terminal elements. A related concept is the
critical chain, which adds resource dependencies. The critical path method (CPM) was invented by the
DuPont corporation during the 1950's.
CRM - Customer Relationship Management. CRM entails
all aspects of interaction a company has with its customer. CRM is
a process that will help bring together lots of pieces of information about
customers, sales, marketing effectiveness, responsiveness and market trends.
Computerization has changed the way companies are
approaching their CRM strategies because it has also changed consumer buying
behavior. With each new advance in technology, especially the proliferation of
self-service channels like the Web and WAP phones, more of the relationship is
being managed electronically. Organizations are therefore looking for ways to
personalize online experiences (a process also referred to as mass
customization) through tools such as help-desk software, e-mail organizers and
Web development apps.
The term CRM is used to describe
either the software or the whole business strategy (or lack of one) oriented on
customer needs. The second one is the description which is correct. The main
misconception of CRM is that it is only software, instead of whole business
strategy. Major areas of CRM focus on service automated processes,
personal information gathering and processing, and self-service. It attempts to
integrate and automate the various customer serving processes within a company.
BACK TO TOP
D
Data
Modeling -
In
computer science, data modeling is the process of structuring and organizing
data, typically using a database management system. Managing large quantities of structured and unstructured data is a primary
function of information systems. Data models describe structured data for
storage in data management systems such as relational databases. They typically
do not describe unstructured data, such as
word processing documents,
email messages,
pictures, digital audio, and video. Early phases of many software development
projects emphasize the design of a
conceptual data model. Such a design can be detailed into a
logical data model. In later stages, this model may be translated into
physical data model. The term data model actually refers to
two very different things: a description of data structure and the way
data are organized using, for example, a database management system.
A data model describes the structure of the data within a given domain and, by
implication, the underlying structure of that domain itself. A data model may
thus represent classes of entities about which a company wishes to hold
information, the attributes of that information, and relationships among those
entities. The model describes the organization irrespective of how data might be
represented in a computer system. Another kind of data model describes how
to organize data using a database management system or other data management
technology. It describes, for example, relational tables and columns or
object-oriented classes and attributes. Such a data model is sometimes referred
to as the physical data model, but in the original ANSI three schema
architecture, it is called "logical".
DCE - Data Communications Equipment.
Also known as DCTE (Data Circuit Termination Equipment). Data
communications Equipment are installed between a DTE and the transmission
circuit. Examples include LAN Network Interface Card (NIC), CSU/DSC, modem, and
ISDN Terminal Adapter (TA).
DCT
- Discrete Cosine Transform.
A Compression algorithm used in most of the current image compression systems
for bit rate reduction, including the ITU-T P*64 recommendations for
video conferencing (where P is an integer number meant to represent
multiples of 64kbit/sec). DCT represents a discrete signal or image as a
sum of sinusoidal wave forms.
DHCP - In the context of
computer networking, Dynamic Host Configuration Protocol (DHCP,
currently
implemented as DHCPv6) is a
client-server
networking protocol. A DHCP
server provides configuration parameters specific to the DHCP client host
requesting, generally, information required by the client host to participate on
an
IP network. DHCP also provides a mechanism for allocation of
IP
addresses to client hosts. DHCP emerged as a
standard protocol in October 1993.
RFC 2131 provides the latest (March
1997) DHCP definition. DHCP functionally became a successor to the older
BOOTP protocol.
Due to the backward-compatibility of DHCP, very few networks continue to use
pure BOOTP. The latest
standard of the protocol, describing
DHCPv6 (DHCP in
a IPv6
environment), appeared in July 2003 as
RFC 3315.
DIAMETER -
Diameter is an AAA (authentication, authorization and accounting) protocol for
applications such as network access or IP mobility. The basic concept is to
provide a base protocol that can be extended in order to provide AAA services to
new access technologies. Diameter is intended to work in both local and roaming
AAA situations. The name "DIAMETER" is a pun on the
RADIUS
protocol, which is the predecessor (a diameter is twice the radius). Diameter is
not directly
backwards compatible, but provides an upgrade path for RADIUS. The main
differences are :
 |
it uses reliable transport protocols (TCP or SCTP, not UDP) |
 |
it uses transport level security (IPSEC or TLS) |
 |
it has transition support for RADIUS |
 |
it has larger address space for AVPs (Attribute Value Pairs) and identifiers
(32-bit instead of 8-bit) |
 |
it is a peer-to-peer protocol, not client-server : supports server-initiated
messages |
 |
both stateful and stateless models can be used |
 |
it has dynamic discovery of peers (using DNS SRV and NAPTR) |
 |
it has capability negotiation |
 |
it supports application layer acknowledgements,
defines failover methods and state machines (RFC
3539) |
 |
it has error notification |
 |
it has better roaming support |
 |
it is easier extended, new commands and attributes can be defined
|
 |
basic support for user-sessions and accounting is built in |
DID -
Direct
Inward Dialing (DID) refers to a Private Branch
Exchange (PBX) or CENTREX feature that allows stations to be dialed directly
without the aid of an attendant. Also, DID routing with ISDN Direct Dial,
Fax and modem Servers. Similar to Multiple Subscriber Numbering (MSN),
with 10 or more subscriber numbers (as requested by the user). Typically,
DID lines are for incoming calls only.
Decoder -
A piece of hardware or software
that is used to convert video or audio (typically) from the digital form used in
transmission or storage into a form that can be viewed.
Digital audio -
Audio that has been encoded in a
digital form for processing, storage or transmission.
Dithering -
Giving the illusion of new color
and shades by combining dots in various patterns. This is a common way of
gaining gray scales and is commonly used in newspapers. The effects of dithering
would not be optimal in the video produced during a videoconference.
Digital Comb Filter -
Provides maximum picture quality for high resolution sources such as computers,
DVD players, and laser disc.
Digital TV Ready - With
the addition of a Digital TV Card the television will be compatible with ATSC
compliant Digital Television signal.
Display Multiple Formats
- TVs that are compatible with a wide array of PC and Mac¨ computers as well as
cable or network television programming, videotapes, laser discs or practically
any video format.
Distribution Amplifier (DA)
- A device that allows connection of one input source to multiple output
sources such as monitors or projectors.
DNIS - Digital Number Identification Service is a
telco-provided digital service that delivers the called-number (the number that
is dialed).
DOD - Direct Outward Dialing allows outward calls from a Private Branch
Exchange (PBX) that are originated by PBX stations without assistance.
DoS -
A denial-of-service attack is an
attack on a
computer
system or
network that causes a loss of service to users, typically the loss of
network connectivity and services by consuming the
bandwidth
of the victim network or overloading the computational resources of the victim
system. A DoS attack can be perpetrated in a number of ways. There are three basic types
of attack: 1-) consumption of computational resources, such as bandwidth, disk
space, or
CPU time. 2-)disruption of configuration information, such as
routing
information, 3-) disruption of physical network components.
DSL - Short for Digital Subscriber Line.
Refers collectively
to all types of digital subscriber lines, the two
main categories being ADSL
and SDSL. Two other types of
xDSL technologies are High-data-rate DSL (HDSL) and Very high DSL (VDSL).
DSL technologies use sophisticated modulation schemes to pack data onto copper
wires. They are sometimes referred to as last-mile technologies because they are
used only for connections from a telephone switching station to a home or
office, not between switching stations. xDSL is similar to ISDN inasmuch
as both operate over existing copper telephone lines (POTS) and both require the
short runs to a central telephone office (usually less than 20,000 feet).
However, xDSL offers much higher speeds - up to 32 Mbps for upstream traffic,
and from 32 Kbps to over 1 Mbps for downstream traffic.
DSLAM - Short for
Digital Subscriber Line Access Multiplexer, a mechanism at a phone company's
central location that links many customer DSL connections to a single high-speed
ATM line. When the phone company receives a DSL signal, an xDSL modem with
a POTS splitter detects voice calls and data. Voice calls are sent to the PSTN,
and data are sent to the DSLAM, where it passes through the ATM to the Internet,
then back through the DSLAM and xDSL modem before returning to the customer's
PC. More DSLAMs a phone company has, the more customers it can support.
DTE - Data Terminal Equipment. A term used in the data world to
indicate a terminal device. DTE is part of a broader grouping of equipment
known as CPE (Customer Premises Equipment), which includes voice, as well as
data, terminals. DTE can be a dumb terminal or a server computer.
DTE interfaces to a circuit through DCE.
DTV - Digital
television is the transmission of television signals using digital rather than
conventional analog methods. Conventional standards - National Television
Standards Committee (NTSC), Phase Alternation Line (PAL), and Sequential Couleur
avec Memoire (SECAM) - specify analog transmission. However, both the audio and
video components of a television signal can be transmitted in digital form. The
advantages of DTV over analog TV include: Superior image resolution (detail)
for a given bandwidth, smaller bandwidth for a given image resolution,
compatibility with computers and the Internet, interactivity, superior audio
quality, consistency of reception over varying distances.
Due diligence is the effort a party makes to avoid
harm to another party. Failure to make this effort is considered negligence. Quite often a
contract will specify
that a party is obligated to provide due diligence.
DVB - Digital Video Broadcasting. DVB is a set of standards that define
digital broadcasting using existing satellite,
cable, and terrestrial infrastructures. A fundamental decision of the DVB
Project was the selection of MPEG-2, one of a series of MPEG standards for
compression of audio and video signals.
BACK TO TOP
E
E.164 -
ITU Recommendation for international telecommunications
numbering. mainly for ISDN/B-ISDN/SMDS. In short a scheme to assign
numbers to phone lines.
E Channel -
E stands for echo. It is the
16Kbps ISDN basic rate channel echoing contents of DCEs to DTEs. Used in
binding for access to multipoint link.
EAI - Enterprise Application Integration is defined as the use of
software
and computer systems architectural principles to integrate a set of enterprise
computer applications. EAI has increased in importance because enterprise
computing often takes the form of islands of automation. This occurs when the
value of individual systems are not maximized due to partial or full isolation.
If integration is applied without following a structured EAI approach,
point-to-point connections grow across an organization. Dependencies are added
on an impromptu basis, resulting in a tangled mess that is difficult to
maintain. This is commonly referred to as spaghetti, an allusion to the
programming equivalent of spaghetti code. The equation for n-connections is:
n(n-1)/2. EAI is not just about sharing data between applications; it focuses on sharing
both business data and business process. Attending to EAI involves looking at
the
system of systems, which involves large scale
inter-disciplinary problems with multiple,
heterogeneous, distributed
systems that
are embedded in
networks at multiple levels. EAI uses an
Enterprise service bus (ESB), which connects numerous, independent systems
together. Although other approaches have been explored, including connecting at
the database or user-interface level, the ESB approach has been adopted as the
strategic winner. Individual applications can publish messages to the bus and
subscribe to receive certain messages from the bus. Each application only
requires one connection to the bus. The message bus approach can be extremely
scalable
and highly evolvable. EAI is related to
middleware
technologies such as message-oriented middleware (MOM),
and data representation technologies such as
XML. Newer EAI
technologies involve using
web
services as part of
service-oriented architecture as a means of integration. EAI tends to be data centric;
however, it will
come to include
content integration and
business processes.
Enterprise JavaBeans -
The Enterprise JavaBeans (EJB) specification is one of the several
Java
APIs in the
Java Platform, Enterprise Edition. EJB is a
server-side component that encapsulates the business logic of an
application. The EJB specification was originally developed by
Sun Microsystems (EJB 1.0 and 1.1) and later under the
Java Community Process as
JSR 19 (EJB 2.0),
JSR 153 (EJB 2.1) and
JSR 220 (EJB 3.0). The EJB specification details how an
application server provides:
 | persistence |
 | transaction processing
|
 | concurrency control
|
 | events using Java Message
Service |
 | naming and directory
services (JNDI) |
 | security ( JCE and JAAS )
|
 | deployment of software
components in an application server |
 | remote procedure calls
(RPC) using RMI-IIOP or CORBA |
Additionally, the Enterprise JavaBean specification defines the roles played by
the EJB container and the EJBs as well as how to deploy the EJBs in a container.
EJBs are deployed in an EJB container within the application server. The
specification describes how an EJB interacts with its container and how client
code interacts with the container/EJB combination. The EJB classes used by
applications are included in the
javax.ejb package. (The
javax.ejb.spi package is a
service provider interface used only by EJB container implementations.). Each EJB must provide a Java implementation
class and two Java interfaces. The EJB container will create instances of
the Java implementation class to provide the EJB implementation. The Java
interfaces are used by client code of the EJB. The two interfaces, referred to as the Home and the Component
interface, specify the signatures of the EJB's remote methods. The methods are
split into two groups (Note: Additionally Home or the Component Interfaces can be Local or Remote):
 | methods that are not tied
to a specific instance, such as those used to create an EJB instance or to
find an existing entity EJB (see EJB Types, below). These are declared by
the Home interface. |
 | methods that are tied to a
specific instance. These are placed in the Remote interface. |
Because these are merely Java interfaces and not
concrete classes, the EJB container must generate classes for these
interfaces that will act as a proxy in the client. Client code invokes a method
on the generated proxies, which in turn places the method arguments into a
message and sends the message to the EJB server. The proxies == use
RMI-IIOP to
communicate with the EJB server. The server will invoke a corresponding method on an instance of the Java
implementation class to handle the remote method invocation.
Erlang Distribution -
The Erlang distribution is a continuous
probability distribution with wide applicability primarily due to its
relation to the
exponential and
Gamma distributions. The Erlang distribution was developed by
A. K. Erlang to examine the number of telephone calls which might be made at
the same time to the operators of the switching stations. This work on telephone
traffic engineering has been expanded to consider waiting times in
queuing systems in general. The distribution is now used in the field of
stochastic processes.
Easy A/V Switching -
Provides immediate access to A/V inputs via the TV's front panel or remote
control.
EDGE - Enhanced Data Rates for Global Evolution is a technology being
promoted by the TDMA and GSM communities that is capable of both voice and 3G
data rates. EDGE is being considered by AT&T Wireless and Cingular Wireless as a
3G solution. EDGE is still in the lab and field trials have not confirmed its
capabilities.
EDM -
Enterprise Data Management is an
enterprise wide PLM/ PDM data management system that facilitates the
communication of product data through the whole organization (not just in the
engineering department) as well as links to other corporate systems such as ERM
CRM SCM. EDM entails all aspects of managing automated decision design and
deployment that an organization uses to manage its interactions with customers,
employees and suppliers. Computerization has changed the way organizations are
approaching their decision-making because it has enabled information-based
decisions: decisions based on analysis of historical behavioral data, decisions
and their outcomes. Organizations seek to improve their Decision Yield (the
value created through each decision) by deploying business processes and
software solutions that better manage the tradeoffs between precision,
consistency, agility, speed, and cost of decision-making within organizations.
EFR - Enhanced
Full Rate or GSM-EFR is a speech coding standard
that was developed in order to improve the quite poor quality of GSM-Full Rate
(FR) codec. Working at 12.2 kbit/s the EFR provides wire like quality in any
noise free and background noise conditions. The EFR 12.2 kbit/s speech coding
standard is compatible with the highest AMR mode.
EGP - Exterior Gateway
Protocol is a
routing protocol for the
Internet
originally specified in
1982 by
Eric C. Rosen of
Bolt, Beranek, and Newman, and
David L. Mills. It was first described in
RFC 827 and formally specified in
RFC 904 (1984).
EGP is a type of
path vector protocol. During the early days of the Internet, an exterior gateway protocol, EGP version
3, was used to interconnect
autonomous systems. EGP3 should not be confused with EGPs in general.
Currently, BGP is the
accepted standard for Internet routing and has essentially replaced the more
limited EGP3.
EIGRP - Enhanced Interior Gateway Routing
Protocol is a Cisco proprietary routing protocol based on their original IGRP.
EIGRP is a balanced hybrid IP routing protocol, with optimizations to minimize
both the routing instability incurred after topology changes, as well as the use
of bandwidth and processing power in the router.
Some of the routing optimizations
are based on the Diffusing Update Algorithm (DUAL) work from SRI, which
guarantees loop-free operation. In particular, DUAL avoids the "count to
infinity" behavior of RIP when a destination becomes completely unreachable. The
maximum hop count of EIGRP-routed packets is 224. The data EIGRP collects
is stored in three tables: 1- Neighbor Table, 2-Topology Table (or Feasible
successor table), 3- Routing table. EIGRP associates five different
metrics with each route: Delay, Bandwidth, Reliability, Load, MTU (though not actually used in the
calculation).
EIR -
The Equipment Identity
Register is often integrated to the HLR. The EIR keeps a list of mobile
phones (identified by their IMEI) which are to be banned from the network or
monitored. This is designed to allow tracking of stolen mobile phones. In theory
all data about all stolen mobile phones should be distributed to all EIRs in the
world through a Central EIR. It is clear, however, that there are some countries
where this is not in operation. The EIR data does not have to change in real
time, which means that this function can be less distributed than the function
of the HLR.
Embedded Systems -
An embedded system is a special-purpose system in which the
computer is
completely encapsulated by the device it controls. As opposed to a
general-purpose computer, such as a
personal computer, an embedded system performs pre-defined tasks, usually
with very specific requirements. In an application where the system is dedicated
to a specific task, design engineers are able to optimize the system
extensively, thus considerably reducing the size and cost of the end product.
Due to the low-cost advantage, embedded systems are commonly built into products
designed for mass production. The core of any embedded system is a
microprocessor or a
microcontroller, which is programmed to perform a small number of tasks. In
contrast to a general purpose computer which at any time can run essentially any
software application the user chooses, the software on an embedded system is
semi-permanent; so it is often called "firmware".
EMS -
An Enterprise Messaging System is a set of published
Enterprise-wide standards that allows organizations to send semantically precise
messages between computer systems. EMS systems promote
loosely coupled architectures that allow changes in the formats of messages
to have minimum impact on message subscribers. EMS systems are facilitated by
the use of XML
messaging, SOAP and
Web
services. EMS usually take into account the following considerations:1-) Security Messages must be encrypted if they travel over a public
interfaces. Messages must be authenticated or digitally signed if the receiver
is to have confidence the messages have not been tampered in transit. 2-) Routing Messages need to be routed efficiently from the sender to the
receiver. Intermediate nodes may need to route the messages if the body of the
message is encrypted. 3-) Metadata The body of the document contains information that must be
unambiguously interpreted. Metadata registries should be used to create precise
definitions for each data element. 4-) Subscription Systems should be able to subscribe to all messages that
match a specific pattern. Messages with a specific content may be routed
differently. For example some messages may have different priority or security
policies. 5-) Policy Enterprise messaging systems should provide some consideration
for a centralized policy of messages such as what classes or roles of users can
access different fields of any message.
ENG - Electronic News
Gathering.
EnterpriseNet - Suites of integrated, intranet/extranet applications that enable users outside a
firewall to share, manipulate and interact with data inside the firewall. The
suites can include Help Desk, Contact, Defect Tracking System, Collaborative
Workspace and Data Publisher.
ENUM - Telephone Number
Mapping (ENUM or Enum, from TElephone NUmber Mapping) is a suite of protocols to
unify the telephone system with the Internet by using E.164 addresses with DDDS
and DNS. ENUM also refers to "E164 NUmber Mapping". Although it facilitates
VoIP, the protocol used for voice communication across the Internet, ENUM is not
a VoIP requirement and should not be confused with common VoIP routing based on
SIP and H.323 protocols with a Uniform Resource Identifier (URI). VoIP service
providers assign a URI to a customer in order to complete calls over the
internet. ENUM is a DNS-based protocol that is best suited to offer services
that not only help facilitate, but expand on ways to complete calls over VoIP
networks as described below. It provides a user with a domain name on an E.164
server in order to associate a common international telephone number with a URI
and provide other DNS-related services. The server is maintained by the Service
Provider and is expected to become standard since it can successfully address
locating URIs with nothing more than a common international telephone number.
The ITU ENUM allocates a specific zone, namely "e164.arpa" for use with E.164
numbers. Any phone number, such as +1 555 42 42 can be transformed into a
hostname by reversing the numbers, separating them with dots and adding the
e164.arpa suffix thus: 2.4.2.4.5.5.5.1.e164.arpa.
DNS can then be used to look up Internet addresses for services such as SIP VoIP
telephony. NAPTR records are used to 'translate' E.164 addresses to SIP
addresses for example. An example NAPTR record is:
$ORIGIN 2.4.2.4.5.5.5.1.e164.arpa.
IN NAPTR 100 10 "u" "sip+E2U" "!^.*$!sip:phoneme@example.net!"
IN NAPTR 102 10 "u" "mailto+E2U" "!^.*$!mailto:myemail@example.com!"
This example specifies that if you want to use the "sip+E2U" service, you should
use sip:phoneme@example.net as the address. The regular expression can be used
by a telephone company to easily assign addresses to all of its clients. For
example, if your number is +15554242, your SIP address is
sip:4242@555telco.example.net; if your number is +15551234, your SIP address is
sip:1234@555telco.example.net.
Alternative ENUM lookup protocols such as sbXML have also emerged. These
services often provide a faster and easier mechanism to translate E.164 numbers
into SIP addresses. ITU e164.arpa subdomains are first delegated to ("registered
by") regulatory bodies designated by the national government of the country code
concerned, which further delegates zones to telecommunications providers. Your
telephone company is therefore in charge of the NAPTR records, usually. Some
countries are proposing to let end-users register their own telephone numbers
via an intermediary, which need not be their own telco. This is considered a
good idea as VoIP is a major Enum use. People who use an Enum-enabled VoIP
service can dial your existing number and be connected not to your existing
phone line, but to your own VoIP telephone directly via the Internet, bypassing
the telephone system entirely. When they call someone who does not use Enum,
calls complete over the Public Switched Telephone Network or PSTN. Alternative
free public ENUM services such as E164.org have also emerged. These services
often verify PSTN numbers and can be used in addition to e164.arpa. Competing
ENUM zones may be seen as beneficial, to keep prices low in the VoIP market.
EoIP - Everything over IP.
IP enabled services like Data, Voice, video, and TV, etc.
Ephemeral - used in
describing H.248 terminations representing RTP flow i.e. ephemeral or created
per call.
Erlang - An Erlang is a
unit of telephone voice use that specifies the total capacity or average use of
a telephone system. One Erlang is equivalent to the continuous usage of a
telephone line.
ERM - Enterprise
Relationship Management is software that analyzes data it has about its
customers to develop a better understanding of the customer and how the customer
is using its products and services. This kind of application may use data mining
of its data warehouse or existing sales, marketing, service, finance, and
manufacturing databases to generate new information about its customer
relationships.
ERP - Enterprise Resource
Planning. a business management system that
integrates all facets of the business, including planning, manufacturing, sales,
and marketing. As the ERP methodology has become more popular, software
applications have emerged to help business managers implement ERP in business
activities such as inventory control, order tracking, customer service, finance
and human resources.
ESB -
an Enterprise Service Bus refers
to a software architecture construct, implemented by technologies found in a
category of middleware infrastructure products usually based on Web services
standards, that provides foundational services for more complex service-oriented
architectures via an event-driven and XML-based messaging engine (the bus). An
ESB generally provides an abstraction layer on top of an Enterprise Messaging
System (EMS) which allows integration architects to exploit the value of
messaging without writing code. Contrary to commonly used EAI brokers which are
usually implemented as a monolithic stack in a hub and spoke architecture, the
foundation of an ESB is built of base functions broken up into their
constituent parts, with distributed deployment where needed, working in harmony
as necessary. Microsoft DotNET Platform Microsoft BizTalk Server is an
example vendor of ESB.
ESPTM (Energy
Saving Programmability) - Energy Saving system that powers television off
after a specified period of use. A simple countdown clock can be selectively set
to operate from 0-99 hours with automatic clock reset at each power up.
ETL - Extract, Transform,
and Load: extracting data from outside sources, transforming it to fit business needs, and
ultimately loading it into the data warehouse. ETL is important, as
it is the way data actually gets loaded into the warehouse. ETL is a BI
term.
Event Programming - This
feature allows the television to turn on automatically, tune to a specific
channel or source at a specific time, and turn itself off. (e.g. up to five
events a day can be pre-programmed).
Event Scheduling -
Schedule a television, group of televisions or the entire network of televisions
for a specific event including power on, channel selection, and volume control.
EVM - Earned Value
Management is an integrated program management technique that integrates
technical performance requirements, resource planning, with schedules, while
taking risk into consideration. The major objectives of applying earned value to
a contract are to encourage contractors to use effective internal technical,
cost and schedule management control systems, and to permit the customer to rely
on timely data produced by those systems for better management insight. This
data is in turn used for determining product-oriented contract status, and
projecting future performance based on trends of date. In addition, Earned
Value Management allows better and more effective management decision making to
minimize adverse impacts to the project. In other words, Earned
value is a management technique that relates resource planning to schedules and
to technical cost and schedule requirements. All work is planned, budgeted, and
scheduled in time-phased ''planned value'' increments constituting a cost and
schedule measurement baseline. There are two major objectives of an earned value
system: to encourage contractors to use effective internal cost and schedule
management control systems; and to permit the customer to be able to rely on
timely data produced by those systems for determining product-oriented contract
status. Earned Value Management provides an objective measurement of how
much work has been accomplished on a project. Using the earned value process,
the management team can readily compare how much work has actually been
completed against the amount of work planned to be accomplished. All work is
planned, budgeted, and scheduled in time-phased "planned value" increments
constituting a Performance Measurement Baseline.
- Budgeted Cost of Work Scheduled
(BCWS) or Planned Value (PV): tasks planned to be finished for the period.
- Budgeted Cost of Work Produced
(BCWP) or Earned Value (EV): for every period the budgets of the tasks that
actually finished in this time unit. 'How much work is done?'
- Actual Cost (AC) of work
produced (ACWP) or effort spent: actual cost of the work
- Budget At Completion (BAC):
∑BCWS (or ∑PV), the total budget estimated to be spent to complete the project
- Total Funding Available (TFA):
the budget the client has committed to
- Negotiated Period Of Performance
(NPOP): the time period the client has agreed upon with the project manager
- Planned Period Of Performance
(PPOP): the time period thought required to finish the project
- Cost Accrual Ratio (CAR): the
total average cost per person per time unit
- Forecast of remaining work
(FCST) or current schedule: the work that still needs to be done after this time
unit
- Estimate To Complete (ETC), the
projection of remaining costs to be incurred
Cost Variation = EV
- AC; if negative => project cost more than budgeted
Schedule Variance =
EV - PV; if negative => project did not finish on time as scheduled
Cost Performance
Index = BCWP (EV) / ACWP (AC); if <1 then the cost was higher than planned
Schedule Performance
Index = BCWP (EV) / BCWS (PV); if <1 then the actual schedule not as
planned
Estimate
At Completion (EAC) = ACWP (AC) + ETC (Manager's
projection)
To-Complete Performance
Index
(TCPI) = (BAC - BCWP (EV)) / ETC; is compared to CPI
Independent Estimate
At Completion (IEAC) = ∑AC + ((BAC-∑EV) / CPI);
Exceptional Video
Performance - monitor/receiver that delivers 680+ lines of resolution
(S-Video Input), allowing hookup of high resolution sources such as S-VHS and
laserdisc.
Extranet -
An extranet is a private network
that uses Internet technology and the public telecommunication system to
securely share part of a business's information or operations with suppliers,
vendors, partners, customers, or other businesses. An extranet can be viewed as
part of a company's intranet that is extended to users outside the company. It
has also been described as a "state of mind" in which the Internet is perceived
as a way to do business with other companies as well as to sell products to
customers. An extranet requires security and privacy. These can include
firewalls server management, the issuance and use of digital certificates or
similar means of user authentication, encryption of messages, and the use of
virtual private networks (VPNs) that tunnel through the public network. An
extranet could be described as two or more intranets with network
connectivity. Generally, and as with intranets, an extranet will be based on
Internet Protocols. The underlying network technology does not really matter,
for instance it may be that organizations use the Internet for carrying data but
restrict access to resources from the general public via firewalls. A virtual
private network could be set up over the Internet to achieve the same result.
External Speaker Connections
- Institutional Televisions and display products give users the ability to
connect external speakers directly into the back of the set, eliminating the
need for an external amplifier or A/V receiver.
BACK TO TOP
F
FDDI - Abbreviation of Fiber Distributed Data Interface,
a set of ANSI protocols for sending digital data over fiber optic cable. FDDI
networks are token-passing networks, and support data rates of up to 100 Mbps
(100 million bits) per second. FDDI networks are typically used as backbones for
wide-area networks. An extension to FDDI, called FDDI-2, supports
the transmission of voice and video information as well as data. Another
variation of FDDI, called FDDI Full Duplex Technology (FFDT) uses the
same network infrastructure but can potentially support data rates up to 200
Mbps.
FDM - Frequency-division
multiplexing is a form of signal multiplexing where multiple baseband signals
are modulated on different frequency carrier waves and added together to create
a composite signal. FDM can also be used to combine multiple signals before
final modulation onto a carrier wave. In this case the carrier signals are
referred to as subcarriers: an example is stereo FM transmission, where a 38 KHz
subcarrier is used to separate the left-right difference signal from the central
left-right sum channel, prior to the frequency modulation of the composite
signal. Where frequency division multiplexing is used as to allow multiple users
to share a physical communications channel, it is called frequency-division
multiple access (FDMA). FDMA is the traditional way of separating radio signals
from different transmitters. The analog of frequency division multiplexing in
the optical domain is known as wavelength division multiplexing.
FDMA, or
frequency-division multiple access, is the oldest and most important of the
three main ways for multiple radio transmitters to share the radio spectrum. The
other two methods are Time Division Multiple Access (TDMA), and Code Division
Multiple Access (CDMA).
In FDMA, each transmitter is
assigned a distinct frequency channel so that receivers can discriminate among
them by tuning to the desired channel. TDMA and CDMA are always used in
combination with FDMA, i.e., a given frequency channel may be used for either
TDMA or CDMA independently of signals on other frequency channels. (Ultra
wideband is arguably an exception, as it uses essentially all of the usable
radio spectrum in one location.)
FEC - Forward Error Correction (algorithms).
Field - In interlaced video, it takes two scans on a screen to make a
complete picture, or a Frame. Each scan is called a Field. Sometimes these are
referred to as field 1 and field 2.
File Sharing - is the practice of making
files
available for other users to download over the
Internet
and smaller
networks. File sharing is one of the original applications of the
Internet. Usually file sharing follows the
peer-to-peer (P2P) model, where the files are stored on and served by
personal computers of the users. Most people who engage in file sharing are also
downloading files that other users share. Sometimes these two activities are
linked together. P2P File sharing is distinct from file trading in that
downloading files from a P2P network does not require uploading, although some
networks either provide incentives for uploading such as credits or force the
sharing of files being currently downloaded.
Firewall - In computing,
a firewall is a piece of
hardware
and/or software
which functions in a
networked environment to prevent some communications forbidden by the
security policy, analogous to the function of
firewalls in building construction. A firewall is also called a Border
Protection Device (BPD), especially in
NATO contexts, or
packet filter in
BSD contexts. A firewall has the basic task of controlling traffic between
different zones of trust. Typical zones of trust include the
Internet (a
zone with no trust) and an
internal
network (a zone with high trust). The ultimate goal is to provide controlled
connectivity between zones of differing trust levels through the enforcement of
a security policy and connectivity model based on the
least privilege principle. Proper configuration of firewalls demands skill from the
administrator. It requires considerable understanding of network protocols
and of computer security. Small mistakes can render a firewall worthless as a
security tool.
There are three basic types of firewalls depending on:
 |
Whether the communication is being done between a single node and the
network, or between two or more networks. |
 |
Whether the communication is intercepted at the network layer, or at the
application layer. |
 |
Whether the communication state is being tracked at the firewall or not.
|
With regard to the scope of filtered communications there exist:
 |
Personal firewalls, a software application which normally filters traffic
entering or leaving a single computer. |
 |
Network firewalls, normally running on a dedicated network device or
computer positioned on the boundary of two or more networks or DMZs
(demilitarized zones). Such a firewall filters all traffic entering or
leaving the connected networks. |
The latter definition corresponds to the conventional, traditional meaning of
"firewall" in networking. In reference to the layers where the traffic can be intercepted, three main
categories of firewalls exist:
 |
Network layer firewalls. An example would be iptables.
|
 |
Application layer firewalls. An example would be TCP Wrapper. |
 |
Application firewalls. An example would be restricting ftp services through
/etc/ftpaccess file |
These network-layer and application-layer types of firewall may overlap, even
though the personal firewall does not serve a network; indeed, single systems
have implemented both together. There's also the notion of
application firewalls which are sometimes used during
wide area network (WAN)
networking on the world-wide web and govern the system software. An extended
description would place them lower than application layer firewalls, indeed at
the
Operating System layer, and could alternately be called operating system
firewalls. Some firewalls have higher privileges than others like mysql and pj. Lastly, depending on whether the firewalls track packet states, two additional
categories of firewalls exist:
 |
Stateful firewalls |
 |
Stateless firewalls |
Network layer firewalls operate at a (relatively) low level of the TCP/IP
protocol stack as IP-packet filters, not allowing packets to pass through the
firewall unless they match the rules. The firewall administrator may define the
rules; or default built-in rules may apply (as in some inflexible firewall
systems). A more permissive setup could allow any packet to pass the
filter as long as it does not match one or more "negative-rules", or "deny
rules". Today network firewalls are built into most computer operating systems
and network appliances. Modern firewalls can filter traffic based on many
packet attributes like source IP address, source port, destination IP address or
port, destination service like WWW or FTP. They can filter based on protocols,
TTL values, netblock of originator, domain name of the source, and many other
attributes.
Application-layer firewalls work on the application level of the TCP/IP
stack (i.e., all browser traffic, or all telnet or ftp traffic), and may
intercept all packets traveling to or from an application. They block other
packets (usually dropping them without acknowledgement to the sender). In
principle, application firewalls can prevent all unwanted outside traffic from
reaching protected machines. By inspecting all packets for improper content, firewalls can even prevent the
spread of the likes of
viruses. In practice, however, this becomes so complex and so difficult to
attempt (given the variety of applications and the diversity of content each may
allow in its packet traffic) that comprehensive firewall design does not
generally attempt this approach. The XML firewall exemplifies a more
recent kind of application-layer firewall.
Proxies: A
proxy device (running either on dedicated hardware or as software on a
general-purpose machine) may act as a firewall by responding to input packets
(connection requests, for example) in the manner of an application, whilst
blocking other packets. Proxies make tampering with an internal system
from the external network more difficult and misuse of one internal system would
not necessarily cause a security breach exploitable from outside the firewall
(as long as the application proxy remains intact and properly configured).
Conversely, intruders may hijack a publicly-reachable system and use it as a
proxy for their own purposes; the proxy then masquerades as that system to other
internal machines. While use of internal address spaces enhances security,
crackers may still employ methods such as IP
spoofing to attempt to pass packets to a target
network.
Network address translation: Firewalls often have
network address translation (NAT) functionality, and the hosts protected behind
a firewall commonly use so-called "private address space", as defined in
RFC 1918. Administrators
often set up such scenarios in an effort (of debatable effectiveness) to
disguise the internal address or network.
Management:
The Middlebox Communication (midcom) Working Group of the Internet
Engineering Task Force is working on standardizing protocols for managing
firewalls and other middleboxes. See, e.g., Middlebox Communications (MIDCOM)
Protocol Semantics.
Flexible Connectivity - A televisions feature allowing a multitude of
input/output capabilities including interface slot, S-Video input/output, two
audio inputs, Composite Video input/output, Smart PlugTM interface,
and RF input.
Flicker Filter - Advanced filter results in improved computer-generated
graphics display and higher resolution.
Float -
Float in
project management is the amount of time that a
terminal element in a
project network can be delayed by, without causing a delay to: a-) subsequent
terminal elements (free float), and b-) project completion date (total float).
(float = LS - ES).
FM -
Frequency modulation
is a form of modulation which represents information as variations in the
instantaneous frequency of a carrier wave. (Contrast this with amplitude
modulation, in which the amplitude of the carrier is varied while its frequency
remains constant.) In
analog applications, the carrier frequency is varied in direct proportion to
changes in the amplitude of an input signal. Digital data can be represented by
shifting the carrier frequency among a set of discrete values, a technique known
as frequency-shift keying.
FM is commonly used at VHF radio
frequencies for high-fidelity broadcasts of music and speech (see FM
broadcasting). A narrowband form is used for voice communications in commercial
and amateur radio settings. The type of FM modulation is generally called
wide-FM, or W-FM, and in other parts of the spectrum, narrowband narrow-fm
(N-FM) is used to conserve bandwidth. It is also used to send signals into
space. FM is also
used at intermediate frequencies by most analog VCR systems, including VHS, to
record the luminance (black and white) portion of the video signal. FM is the
only feasible method of recording to and retrieving from magnetic tape without
extreme distortion a signal with a very large range of frequency components -- a
video signal has components from a few hertz to several megahertz.
FM is also used at audio
frequencies to synthesize sound. This technique, known as FM synthesis, was
popularized by early digital synthesizers and became a standard feature for
several generations of personal computer sound cards.
FM radio - is a broadcast
technology invented by Edwin Howard Armstrong that uses frequency modulation to
provide high-fidelity sound over broadcast radio. FM radio is distributed
primarily through broadcast reception of FM radio signals, although it is also
possible to distribute FM signals via cable FM, either by using an adapter to
plug analogue cable wires directly into an FM receiver, or through the use of
television channel allocations on a digital cable service.
FOA -
First Office Application. A telephony term
for beta testing.
FOMA - Freedom Of Mobile multimedia Access (FOMA) is the name of NTT
DoCoMo’s WCDMA service. FOMA is a modified version of UMTS Release 99 with an
initial data rate of 64 Kbps. It is expected that NTT DoCoMo will transition to
the final release of UMTS in 2003 or later.
Frame - In interlaced
video, a Frame is one complete picture
in a video or
film.
A Frame is made up of two fields, or two sets of interlaced lines.
A video frame comprises two interlace fields of either 525 lines (NTSC) or
625 lines (PAL). Full-motion video for NTSC runs at 30 frames per second
(fps); for PAL, 25 fps. Film runs at 24 fps.
Frequency Agile - Televisions can be controlled through RF cable TV
distribution system and can be configured to communicate at a variety of
frequencies so that most RF distribution systems should require minimal
modifications or adjustments.
Freenet -
is a
decentralized censorship-resistant peer-to-peer distributed data store aiming to
provide electronic freedom of speech through strong anonymity. Freenet works by
pooling the contributed bandwidth and storage space of member computers to allow
users to anonymously publish or retrieve various kinds of information. Freenet
uses a kind of key based routing similar to a distributed hash table to locate
peers' data.
Front A/V Jacks - Fast, easy connection of external video sources (VCR,
camcorder, or video games.
Front Control Lockout - Provides the ability to limit or total disable
the buttons found on the front of the set.
Full
duplex -
Sending data in both directions at the same time.
Usually higher quality, but requires more bandwidth. In video conferencing, full
duplex will be much more natural and useable. Cheap speakerphones are half
duplex, whereas more expensive ones are full duplex.
Full Motion Video - A standard video signal that
can be transmitted by a variety of means including television broadcast,
microwave, fiber optics, and satellite. Full motion video traditionally requires
6 MHz in analog format and 45 Mbps when encoded digitally. Industry agreements
are still needed for efficiently mapping advanced digital video streams into ATM
and handling the effect of "cell jitter" in
applications where video and audio synchronization is crucial. Since 1994 there
have been multimedia experiments over MBONE (Multicast backBONE) primarily by
NASA and the military. Some form of video compression normally is used to reduce
the amount of data and to allow it to be read from disk quickly enough. The time
taken for compression can be relatively long; decompression is done in real-time
with the picture quality and frame rate varying with the processing power
available. Two compression standards discussed with full motion video are H.261
and MPEG. H.261 was developed before 1992 to work with ISDN and support video
conferencing.
BACK TO TOP
G
G.7xx -
A family of ITU standards for
audio compression.
G.711 -
Audio codec
standard for 3 kHz audio using 48 or 56 kbps bandwidth.
G.722 -
Audio codec standard for 7 kHz audio using 48 or 56 kbps bandwidth.
G.723 -
Audio codec standard to be used with POTS H.324 video codec standard.
G.728 -
Newer audio codec standard for 3 kHz audio using only 16 kbps bandwidth.
GAIT -
GSM ANSI-136 Interoperability Team (GAIT) is a technology that enables GSM and
TDMA networks to interoperate. Special handsets must be manufactured (often
called “GAIT phones”) and used in conjunction with GAIT networking. Currently
there are no GAIT handsets, nor are there any GAIT networks in operation.
GAN
- Gallium nitride is a
semiconductor compound expected to make possible miniaturized, high-power
wireless transmitters. These transmitters will be combined with sensitive
receivers into telephone sets capable of directly accessing communications
satellite.
Gatekeeper -
In the H.323 world, the gatekeeper
provides several important functions. First, it controls access to the network,
allowing or denying calls and controlling the bandwidth of a call. Second, it
helps with address resolution, making possible email type names for end users,
and converting those into the appropriate network addresses. They also handle
call tracking and billing, call signaling, and the management of gateways. They
also handle call tracking and billing, call signaling, and the management of
gateways.
Gateway -
Gateways provide a link between
the H.323 world and other video conferencing systems. A common example would be
a gateway to a H.320 (ISDN) video conferencing system.
GERAN - GSM EDGE
Radio Access Network. It is one of the main 3GPP (Third
Generation Partnership Project) UMTS standardization areas.
GPRS - GSM Packet Radio
Service or General Packet Radio Service (GPRS) is an upgrade to a GSM network
that adds packet data to the voice network. GPRS uses the same time slots as
voice calls and each time slot is capable of approximately 9.6 Kbps of data
throughput. A GPRS network that offers 28.8 Kbps down to the phone and 9.6 Kbps
from the phone back to the network is using three time slots down and one up.
GPRS network operators and vendors tend to add the two speeds together when
discussing data speeds. This example would be called a system with 38-Kbps data
capability.
GSM - Global System for
Mobility (GSM) is a TDMA digital technology deployed first in Europe. Today
65-70% of all wireless voice networks use GSM technology. GSM is less efficient
than TDMA since it requires a 200-KHz channel. GSM capacity is 3 to 4 times
that of analog service.
GUI - Graphical User
Interface (e.g. Microsoft Windows operating system).
BACK TO TOP
H
H.221 -
Protocol for
combining audio, video and data into a frame for transport with ISDN. Also
for separating audio, video, and data from a received frame.
H.224 -
ITU-T Recommendation.
A
real time control protocol for simplex applications using the H.221 LSD/HSD/MLP
channels.
H.230 -
Defines
low-level system control and indication for ISDN (i.e. on frame level).
H.239 -
is a standard for showing the data
(content) along with the Video also known as People+content™.
H.239 is not T.120 or DuoVideo as known and introduced by Tandberg. H.239
just allows you to send and receive the content as a video source and would not
allow for any collaboration.
H.242 -
Defines
high-level system control and indication for ISDN (i.e. on capabilities level).
H.243 -
The standards
for multipoint conferences with three or more stations connected over digital
networks.
H.248 -
H.248 was jointly developed by
ITU-T SG16 and IETF Working group MEGACO.
H.248 is the
standards organizations' answer to MGCP, SGCP, IPDC, etc. ITU
Recommendation has been approved 15th June 2000.
IETF has
published three RFCs on Megaco: RFC 2885, RFC 2886(corrections), RFC
3015(merged). The H.248 architecture is comprised of packages and core
protocol. Packages are used to allow different bearer types and
application (e.g. fax, server, telephony, text, etc.). Core protocol for
Registration, Connection model, and Commands.
H.261 -
ITU-T Recommendation.
Video coding for videoconferencing. H.261 is a discrete cosine transform (DCT)
based algorithm for video in the 64kb/s to 2mb/s range. All H.323 compliant
video conferencing system are required to support this codec.
H.263 -
ITU-T Recommendation.
Video coding within videoconferencing. H.263 offers better compression than
H.261, particularly in the low bit rate range of up to 128Kbps.
H.264 -
Has received Final Draft status on March 28, 2003 by the Joint Video Team (JVT),
a committee of Moving Picture Experts Group (MPEG) and International Standards
Organization/International Telecommunications Union (ISO/ITU). Final
ratification of H.264 by the ITU happened on May 30th. H.264 is also known as
AVC (Advanced Video Coding) or MPEG-4 part 10. H.264 was designed to enable videoconferences to connect
at half the bandwidth and still retain the same quality or it will deliver twice
the quality at the same bandwidth normally used. This recently defined
video encoding and decoding scheme has mixed reviews. Vendors praise it,
and
users in the Labs are questioning
the promised video quality improvement. However, the majority agrees that
H.264 delivers a noticeable performance improvement over H.261 and H.263
at lower bandwidth (<192Kbps) and primarily over H.323. It will be some
time before H.264 compatibility issues between different vendors are resolved.
H.281 -
ITU-T Recommendation.
Far End Camera Control (FECC).
H.320 -
ITU-T Recommendation
for videoconferencing over ISDN, V.35, and fractional E1/T1 lines.
It includes the
H.261 video codec standard, the H.221, and H.230.
H.321 -
ITU-T Recommendation
for the adaptation to the ATM environment of H.320 videoconferencing standards.
Also see H.320 and V.80.
H.323 -
ITU-T Recommendation
which serves as the "umbrella" for a set of standards defining real-time
multimedia communications for packet based networks.
H.324 -
ITU-T Recommendation
for video conferencing over analog POTS telephone lines. Also see V.80.
H.350 -
ITU-T Recommendation
describing a
directory services architecture for multimedia conferencing using LDAP.
Standardized directory services can support association of persons with
endpoints, searchable white pages, and clickable dialling. Directory services
can also assist in the configuration of endpoints, and user authentication based
on authoritative data sources. This document describes a standardized LDAP
schema to represent endpoints on the network and associate those endpoints with
users. It discusses design and implementation considerations for the
inter-relation of video and voice-specific directories, enterprise directories,
call servers and endpoints. Also see RFC3944.
Half duplex -
A telecommunications system where
data can only flow in one direction at a time. Cheaper speakerphones are a good
example of this, where only one person can talk at a time.
Handoff -
In
cellular
telecommunications, the term handoff refers to the process of
transferring an ongoing call or data session from one channel connected to the
core network to another. In
satellite communications it is the process of transferring satellite control
responsibility from one
earth
station to another without loss or interruption of service. The
British English term for transferring a cellular call is handover,
which is the terminology standardized within such European originated
technologies as GSM
and UMTS. In
telecommunications there are two reasons why a handoff (handover) might be
conducted: if the phone has moved out of range from one
cell site
(base station) and can get a better radio link from a stronger transmitter, or
if one base station is full the connection can be transferred to another nearby
base
station. The most basic form of handoff is that used in
GSM and
analog cellular
networks, where a
phone call in progress is
redirected from one
cell site
and its transmit/receive
frequency
pair to another base station (or sector within the same cell) using a different
frequency pair without interrupting the call. As the phone can be connected to
only one base station at a time and therefore needs to drop the radio link for a
brief period of time before being connected to a different, stronger
transmitter, this is referred to as a hard handoff. This type of handoff
is described as "break before make" (referring to the radio link). In CDMA systems the
phone can be connected to several cell sites simultaneously, combining the
signaling from nearby transmitters into one signal using a
rake
receiver. Each cell is made up of one to three (or more) sectors of
coverage, produced by a cell site's independent transmitters outputting through
antennas pointed in different directions. The set of sectors the phone is
currently linked to is referred to as the "active set". A soft handoff
occurs when a CDMA phone adds a new sufficiently-strong sector to its active
set. It is so called because the radio link with the previous sector(s) is not
broken before a link is established with a new sector; this type of handoff is
described as "make before break". In the case where two sectors in the active
set are transmitted from the same cell site, they are said to be in softer
handoff with each other. There are also inter-technology handoffs where a call's connection is
transferred from one access technology to another, e.g. a call being transferred
from GSM to
W-CDMA.
HDTV - high definition
television is a television display technology that provides picture quality
similar to 35 mm. HDTV generally uses digital rather than analog signal
transmission. However, in Japan, the first analog HDTV program was broadcast on
June 3, 1989. It required a 20 MHz
channel, which is why analog HDTV broadcasting is not feasible in most
countries.
High fidelity (or HiFi
or hi-fi) is the reproduction of sound and image that is very faithful to
the original. Hi-fi aims to achieve minimal or unnoticeable amounts of noise and
distortion. The term hi-fi can be applied to any reasonable-quality home-music
system. Hi-fi enthusiasts are often known as audiophiles or videophiles.
High Resolution Digital Display Capability - Provides large-screen high
resolution digital display resolution: VGA - 640 x 480, SVGA - 800 x 600 or XGA
- 1024 x 768. Refresh rates are compatible with most PC and Mac® refresh rates –
excellent performance from 50-75Hz.
HLR - The Home Location Register or HLR is a central database that contains
details of each
mobile
phone subscriber that is authorized to use the GSM core network.
More precisely, the HLR stores details of every
SIM card
issued by the
mobile phone operator. Each SIM has a unique identifier called an
IMSI which is one
of the
primary keys to each HLR record. The next important items of data associated with the SIM are the
telephone numbers used to make and receive calls to the mobile phone, known
as MSISDNs. The
main MSISDN is the number used for making and receiving voice calls and SMS, but
it is possible for a SIM to have other secondary MSISDNs associated with it for
fax and data calls.
Each MSISDN is also a
primary
key to the HLR record. Examples of other data stored in the HLR in a
SIM record is:
 | GSM services that the
subscriber has requested or been given |
 | GPRS settings to allow the
subscriber to access packet services |
 | Current Location of
subscriber (VLR and SGSN) |
 | Call divert settings
applicable for each associated MSISDN. |
The HLR data is stored for as long as a subscriber remains with the
mobile phone operator. At first glance, the HLR seems to be just a database which is merely accessed by
other network elements which do the actual processing for
mobile
phone services. In fact the HLR is a system which directly receives and
processes
MAP transactions and messages. If the HLR fails, then the mobile network is
effectively disabled as it is the HLR which manages the Location Updates as
mobile
phones roam
around. As the number of mobile subscribers has grown in
mobile phone operators the HLR has become a more powerful computer
server rather than the traditional
telephone exchange hardware in the early days of
GSM.
Horizontal and Vertical Image Scaling to Fit TV Screen Audio Input with
Loop-Through Output - Regular phono jacks designed to accompany the
SVGA/VGA, S-Video, and composite video inputs. These inputs accept a wide
variety of audio sources.
Horizontal Resolution - The smallest increment of a television picture
that can be discerned in the horizontal plane. This increment is dependent upon
the video bandwidth and is measured in frequency. It determines the number of
lines it takes to scan an image on the screen.
HSS -
The Home Subscriber Server is the master user
database
that supports the IMS network entities that are actually handling the
calls/sessions.
It contains the subscription-related information (user
profiles),
performs
authentication and
authorization of the user, and can provide information about the physical
location of user. It's similar to the GSM
HLR and
AUC. An SLF (Subscriber Location Function) is needed when multiple HSSs are
used. Both the HSS and the SLF implement the
DIAMETER
protocol (Cx, Dx and Sh interfaces).
BACK TO TOP
I
I-mode - is a technical specification and
business model developed by Japan’s NTT DoCoMo for delivery of Web-type content
to wireless handsets.
ICD -
Internet Call Diversion is
a transparent routing of calls between voice and data networks. By enabling remote
access equipment to communicate with carriers’ SS7 networks, the ICD supports
the redirection of resource-consuming Internet traffic from the public switched
telephone network (PSTN) directly onto data networks. Service providers gain the
capability to end Internet call busy signals, cut dial-up connection costs and
free up PSTN circuits to carry voice traffic only.
ICMP -
Internet Control Message Protocol is one of the core protocols of the
Internet protocol suite. It is chiefly used by networked computers'
operating systems to send error messages—indicating, for instance, that a
requested service is not available or that a host or router could not be
reached. ICMP differs in purpose from
TCP and
UDP in that it is usually not used directly by user network
applications. One exception is the
ping tool, which
sends ICMP Echo Request messages (and receives Echo Response messages) to
determine whether a host is reachable and how long packets take to get to and
from that host. The version
of ICMP for Internet Protocol version 4 is also known as ICMPv4, as it is
part of IPv4. IPv6 has an equivalent protocol, ICMPv6.
iDEN-
Integrated Digital Enhanced Network is a mobile communications
technology, developed by Motorola, which provides its users the benefits of a
trunked radio and a cellular telephone. Sprint Nextel is the largest U.S.
retailer of iDEN services. iDEN places more users in a given spectral space,
compared to analog cellular systems, by using time division multiple access
(TDMA). Up to six communication channels share a 25 kHz space; some competing
technologies place only one channel in 12.5 kHz. iDEN is a Motorola proprietary version of TDMA with a unique “push-to-talk”
two-way radio capability. Nextel Communications is the largest iDEN operator in
the U.S.
IDL - An Interface
Description Language, (alternatively interface definition language) (IDL), is a
computer language or simple syntax for describing the interface of a software
component. It is essentially a common language for writing the "manual" on how
to use a piece of software from another piece of software, in much the same
fashion that a user manual describes how to use a piece of software to the user.
IDLs are used in situations where the software on either side may not share
common "call semantics", referring to the way the computer language "talks" to
the routines. For instance, C and Pascal have different ways of calling
routines, and in general cannot call code written in the other language. IDLs
are a subset of both, a general language to which both can conform to enable
language-independent code. IDLs are most commonly found in software
intended to allow routines to be called on other machines, known as remote
procedure call. In these cases the call semantics may vary not only between
languages, but also due to the architecture of the machines themselves.
An IDL is part of
Sun's ONC RPC,
The
Open Group's
Distributed Computing Environment,
Microsoft's
COM, IBM's
System Object Model,
Mozilla's
XPCOM (also known
as XPIDL), the
Object Management Group's
CORBA, and
SOAP for
Web
Services.
IEEE 1394 -
A very fast external bus
standard that supports data transfer rates of up to 400Mbps (in 1394a) and
800Mbps (in 1394b). Products supporting the 1394 standard go under different
names, depending on the company. Apple, which originally developed the
technology, uses the trademarked name FireWire. Other companies use other
names, such as i.link and Lynx, to describe their 1394 products.
A single 1394 port can be used to connect up 63 external devices. In addition to
its high speed, 1394 also supports isochronous
data -- delivering data at a guaranteed rate. This makes it ideal for
devices that need to transfer high levels of data in real-time, such as
video devices.
Although extremely fast and flexible, 1394 is also expensive. Like USB, 1394
supports both Plug-and-Play and hot plugging, and also provides power to
peripheral devices.
IEEE 802.2 -
Developed by the IEEE, 802.2 defines a datalink layer standard used with 802.3,
802.4, 802.5 & 802.6. 802.2 adds several header fields to those normally used by
the upper layer protocols. These fields identify what upper layer protocol is
used in the frame and which network layer processes are the frames source and
destination.
IEEE 802.3 -
802.3 was proposed by the IEEE. The following specifications are supported.
1base5, 10base2, 10base5, 10baseT, 10baseF, 10broad36 and 100baseX. 802.3 uses
CSMA/CD as its contention method.
IEEE 802.5 -
This is the IEEE standard for IBMs Token Ring spec. Token Ring operates at 4 or
16 Mbps. 802.5 does not specify any medium type, but generally UTP is used.
IEEE 802.6 -
This spec represents the DQDB (Distributed Queue Dual Bus) standard. This is
used in MANs, Metropolitan area networks. DQDB uses a fiber based dual bus
topology that may be looped for fault tolerance. Each bus is unidirectional and
both buses operate in opposite directions. DQDB allocates bandwidth by using TDM.
Traffic may be sync or async.
IEEE 802.9 -
IEEE 802.9 isoEthernet. isoEthernet provides a way to bring both
Ethernet and ISDN directly to the enterprise desktop.
IETF -
Internet Engineering Task Force.
This is a group that develops and publishes new standards for use on the
Internet, in
particular those of the TCP/IP protocol suite. It is an open, all-volunteer
standards organization, with no formal membership or membership requirements. It is organized into a large number of
working groups and
BoFs, each dealing with a specific topic, and intended to complete work on
that topic and then shut down. Each working group has an appointed chair (or
sometimes several co-chairs), along with a charter that describes its focus, and
what and when it is expected to produce. The working groups are organized
into areas by subject matter; each area is overseen by an
area director (AD) (most areas have 2 co-AD's); the ADs appoint working
group chairs. The area directors, together with the IETF Chair, form the
Internet Engineering Steering Group (IESG), which is responsible for the
overall operation of the IETF. The IETF is formally an activity under the umbrella of the
Internet Society. The IETF is overseen by the
Internet Architecture Board (IAB), which oversees its external
relationships, and relations with the
RFC Editor.
The IAB is also jointly responsible for the
IETF Administrative Oversight Committee (IAOC), which oversees the
IETF Administrative Support Activity (IASA), which provides logistical, etc
support for the IETF. The IAB also manages the
Internet Research Task Force (IRTF), with which the IETF has a number of
cross-group relations.
IGMP -
Internet Group Management
Protocol. This protocol is used in multicasting.
IGP -
Interior Gateway Protocol
refers to a routing protocol that is used within an autonomous system. The most
commonly used IGPs are RIP, OSPF and IS-IS.
When using a routing protocol such as
BGP in a network, the routes received have a next hop that is not
necessarily directly connected. The IGP is used to "resolve" these next hops.
IM -
Instant messaging is the act of instantly communicating between two or more
people over a network such as the
Internet.
Instant Messaging requires the use of a
client program that hooks up an instant messaging service and differs from
e-mail in that
conversations are then able to happen in
real time.
Most services offer a
presence information feature, indicating whether people on one's list of
contacts are currently online and available to chat. This may be called a 'Buddy
List'. In early instant messaging programs, each letter appeared as it was
typed, and when letters were deleted to correct typos this was also seen in real
time. This made it more like a telephone conversation than exchanging letters.
In modern instant messaging programs, the other party in the conversation
generally only sees each line of text right after a new line is started. Most
instant messaging applications also include the ability to set a
status message, roughly analogous to the message on a telephone answering
machine. Popular instant messaging services on the public Internet include
Qnext,
MSN
Messenger,
AOL Instant Messenger,
Yahoo! Messenger,
Skype,
Google
Talk,
.NET Messenger Service,
Jabber,
QQ,
iChat and
ICQ. These services
owe many ideas to an older (and still popular)
online
chat medium known as
Internet Relay Chat (IRC).
IMEI -
The International Mobile Equipment Identity is a number
unique to every GSM
and UMTS mobile
phone. It is usually found printed on or underneath the phone's battery and can
also be found by dialing the sequence *#06# into the phone. The IMEI number is used by the
GSM network to
identify valid devices and therefore can be used to stop a stolen phone from
accessing the network. For example, if a mobile phone is stolen, the owner can
call his or her network provider and instruct them to "bar" the phone using its
IMEI number. This renders the phone useless, regardless of whether the phone's
SIM is changed. Unlike the
ESN of CDMA and
other wireless networks, the IMEI is only used to identify the device, and has
no permanent or semi-permanent relation to the subscriber. Instead, the
subscriber is identified by transmission of an
IMSI number, which
is stored on a
SIM card which can (in theory) be transferred to any handset. However, many
network and security features are enabled by knowing the current device being
used by a subscriber.
IMIA -
International Medical Informatics
Association
IMP -
Integrated Master Plan:
Integrated Master Planning can
develop an event-based IMP for your proposal or assist your staff with IMP
development. The IMP will be unique to your company's
management processes and structure.
IMS -
The IP Multimedia Subsystem is a
standardized Next Generation Networking (NGN) architecture for telecom operators
that want to provide mobile and fixed multimedia services. It uses a
Voice-over-IP (VoIP) implementation based on a 3GPP standardized implementation
of SIP, and runs over the standard Internet Protocol (IP). Existing phone
systems (both packet-switched and circuit-switched) are supported. The aim
of IMS is not only to provide new services but all the services, current and
future, that the Internet provides. In addition, users have to be able to
execute all their services when roaming as well as from their home networks. To
achieve these goals, IMS uses open standard IP protocols, defined by the IETF.
So, a multimedia session between two IMS users, between an IMS user and a user
on the Internet, and between two users on the Internet is established using
exactly the same protocol. Moreover, the interfaces for service developers are
also based on IP protocols. This is why IMS truly merges the Internet with the
cellular world; it uses cellular technologies to provide ubiquitous access and
Internet technologies to provide appealing services.
IMS - Integrated Master Schedule. Integrated Master Planning (IMP) can prepare the IMS
which expands the IMP to a working level networked schedule or assist your
staff with IMS development. During the IMP and IMS development process, all the
elements of the proposal will be integrated into one master database for cross
correlation and reference.
IMSI -
IMSI [im-zee] is an
acronym for
International Mobile Subscriber Identity. This is a unique number that is
associated with all GSM
and UMTS network
mobile phone users. The number is stored in the
SIM. It is sent by
the mobile to the network and is used to look up the other details of the mobile
in the
HLR or as locally copied in the
VLR. In order to
avoid the subscriber being identified and tracked by
eavesdroppers on the radio interface, the IMSI is sent as rarely as possible
and a randomly generated
TMSI is sent
instead. An IMSI is usually fifteen digits long. However, they can be shorter (e.g. MTN
SouthAfrica's are 14 digits). The first three digits are the
country code (MCC),
and the next digits are the network code (MNC). The MNC can be either two digits
long (normal e.g. in Europe) or three digits long (normal in North America), the
remaining digits, up to the maximum length are the unique subscriber number (MSIN)
within the network's customer base. The IMSI conforms to the
ITU E.212
numbering standard.
IMUX -
Inverse multiplexer. Re-aggregates split sub-channels in a data stream
into a single channel. See ISDN
INAP -
The Intelligent Network Application Part is a signaling
protocol used in the
intelligent network architecture. It is part of the
SS7 protocol suite,
typically layered on top of the TCAP protocol. The
ITU defines several "capability levels" for this protocol, starting with
Capability Set 1 (CS-1). A typical application for the
IN is a Number Translation service. For example, in the
United Kingdom, 0800 numbers are freephone numbers and are translated to a
geographic number using an IN platform. The Telephone exchanges decode the 0800
numbers to an IN trigger and the exchange connects to the IN. The Telephone exchange uses
TCAP, SCCP and
INAP and in IN terms is a
Service Switching Point. It sends an INAP Initial Detection Point (IDP)
message to the Service Control Point. The SCP returns an INAP Connect message,
which contains a geographic number to forward the call to. INAP messages are defined using
ASN.1 encoding.
SCCP is used for the routing. TCAP is used to separate the transactions
apart.
Input/Output Capabilities
- Features a multitude of input/output capabilities including antenna input,
board interface slot, SVGA/VGA input/output, S-Video input/output, audio
input/output, VGA Audio in, and composite video input/output.
Interlaced - The process
of scanning whereby the alternate lines of both scanned fields fall evenly
between each other.
Internet -
the extensive,
worldwide computer network available to the public. An internet is a
more general term informally used to describe any set of
interconnected computer networks that are connected by
internetworking. The Internet, or simply the Net, is
the publicly accessible worldwide system of interconnected computer
networks that transmit data by packet switching using a standardized
Internet Protocol (IP) and many other protocols. It is made up of
thousands of smaller commercial, academic, domestic and government
networks. It carries various information and services, such as
electronic mail, online chat and the interlinked web pages and other
documents of the World Wide Web.
Internet Protocol
Suite - is the set of
communications protocols that implement the
protocol stack on which the
Internet
and most commercial networks run. It is sometimes called the TCP/IP
protocol suite, after the two most important protocols in it: the
Transmission Control Protocol (TCP) and the
Internet Protocol (IP), which were also the first two defined. The internet protocol suite — like many protocol suites — can be viewed as a set
of layers, each layer solves a set of problems involving the transmission of
data, and provides a well-defined service to the
upper layer protocols based on using services from some lower layers. Upper
layers are logically closer to the user and deal with more abstract data,
relying on
lower layer protocols to translate data into forms that can eventually be
physically transmitted. The OSI model
describes a fixed set of seven layers that some vendors prefer and that can be
roughly compared to the IP suite. This comparison can cause confusion or give
further insight into the IP suite.
|
Layer |
Protocols |
| Application |
DNS,
TLS/SSL, TFTP, FTP, HTTP, IMAP, IRC, NNTP, POP3, SIP, SMTP, SNMP, SSH,
TELNET, BitTorrent, RTP, rlogin, ENRP, … |
| Transport |
TCP, UDP,
DCCP, SCTP, IL, RUDP, … |
| Network |
IP (IPv4,
IPv6), ICMP, IGMP, ARP, RARP, … |
| Data Link |
Ethernet,
Wi-Fi, Token ring, PPP, SLIP, FDDI, ATM, DTM, Frame Relay, SMDS, ... |
| Physical |
wire,
radio, fiber optic, Carrier pigeon -
RS-232,
EIA-422,
RS-449,
EIA-485,
10BASE2,
10BASE-T, ... |
Internetworking
- Connecting computer networks together. LAN to LAN, LAN to WAN, and
WAN to WAN. Internetworking is accomplished using Brouters, Routers, and
Gateways.
Interoperability -
A state of complete compatibility
among devices required to operate together with each other, with reference to a
specified feature set or standard. This is an important consideration when
mixing non-ITU-T codecs from different manufacturers and when mixing ITU-T
codecs from different manufacturers which may support different capabilities.
Remember that ITU-T codec systems revert to the highest common denominator for
operation.
Interworking -
a telecommunications
term, used mostly in network convergence and Next Generation Networks, referring
to interworking between different networks or network protocols like: IP and
ISDN, FR and ATM, RTP and AAL2, etc.
Intranet -
An intranet is a LAN used
internally in an organization to facilitate communication and access to
information that is sometimes access-restricted. Sometimes the term refers only
to the most visible service, the internal web site. The same concepts and
technologies of the Internet such as clients and servers running on the Internet
protocol suite are used to build an intranet. HTTP and other internet protocols
are commonly used as well, especially FTP and email. There is often an attempt
to use internet technologies to provide new interfaces with corporate 'legacy'
data and information systems. Access from the organization's internal
network to the internet itself, if need be, will be through a firewall with a
gateway. Traffic going through the gateway can be monitored by the
organization's security department. This means that organizations that allow
their staff internet access can normally determine which internet web sites are
being viewed, block access to specific sites they don't want them to see (such
as pornographic sex sites), and even trace offenders who persistently attempt to
view them. They can also block certain types of web content (such as objects)
which they consider a particular security risk. Where external email
access is provided, known sources of spam and specific types of email attachment
can be blocked by the organization. It should also be noted that emails sent and
received this way can be required to be produced by the organization in the
event of legal action against it by a third party.
IP - The Internet Protocol. It was
developed by the government for use in internetworking multiple computer
networks together. IP is the network layer for the TCP/IP protocol suite
that is the basis of the Internet. IP is also widely used on Ethernet networks. IP is used for the transmission of data, voice, video
and other information over the Internet.
IPDC -
Internet Protocol Device Control protocol is
used to manage the network access devices and to request the set-up and teardown
of calls. Also see Megaco.
IP Multicast -
A system for sending IP
transmissions out only one time, but allowing for multiple users to receive it.
This would reduce the bandwidth required for audio and video broadcasting over
the Internet, but it is not widely used yet.
IPsec - IP security is a standard for securing Internet Protocol (IP)
communications by encrypting and/or authenticating all IP packets. IPsec
provides security at the network layer.
IPsec protocols are defined by
RFCs 2401–2412. IPsec is a set of cryptographic protocols for: 1- securing
packet flows and 2- key exchange. Of the former, there are two: Encapsulating
Security Payload (ESP) provides authentication, data confidentiality and message
integrity; Authentication Header (AH) provides authentication and message
integrity, but does not offer confidentiality. Originally AH was only used for
integrity and ESP was used only for encryption; authentication functionality was
added subsequently to ESP. Currently only one key exchange protocol is
defined, the IKE (Internet Key Exchange) protocol. Click here for IPsec
configuration.
IPv4 -
IPv4 is version 4 of the
Internet Protocol (IP) and it is the first version of the Internet Protocol
to be widely deployed. IPv4 is the dominant
network layer protocol on the
internet
and when ignoring its successor —
IPv6 — it is the
only protocol used on the
internet. It is described in IETF
RFC 791 (September 1981) which obsoleted
RFC 760 (January 1980). The
United States Department of Defense also standardized it as MIL-STD-1777.IPv4 is a data-oriented protocol to be used on a
packet switched
internetwork (e.g.,
Ethernet).
It is a
best effort protocol in that it doesn't guarantee delivery. It doesn't make
any guarantees on the correctness of the data; it may result in duplicated
packets and/or packets out-of-order. All of these things are addressed by an
upper layer protocol (e.g.,
TCP,
UDP). The entire purpose of IP is to provide unique global computer addressing to
ensure that two computers over the internet can uniquely identify one another.
IPv6 -
Internet Protocol version 6 (IPv6) is a
network layer standard used by electronic devices to exchange data across a
packet-switched
internetwork. It follows
IPv4 as the second
version of the
Internet Protocol to be formally adopted for general use.IPv6 is intended to provide more addresses for networked devices, allowing, for
example, each cell phone and mobile electronic device to have its own address.
IPv4 supports 4.3×109 (4.3 billion) addresses, which is inadequate to
give one (or more if they possess more than one device) to every living person.
IPv6 supports 3.4×1038 addresses, or 5×1028(50
octillion)
for each of the roughly 6.5 billion people alive today. Addresses in IPv6
are 128 bits long. IPsec, the protocol for IP network-layer encryption and
authentication, is an integral part of the base protocol suite in IPv6. Invented by
Steve
Deering and
Craig Mudge at
Xerox PARC,
IPv6 was adopted by the
Internet Engineering Task Force in
1994, when it was
called "IP Next Generation" (IPng). (Incidentally,
IPv5 was not a
successor to IPv4, but an experimental flow-oriented
streaming protocol intended to support video and audio.) As of December 2005, IPv6 accounts for a tiny percentage of the live addresses
in the publicly-accessible Internet, which is still dominated by IPv4. The
adoption of IPv6 has been slowed by the introduction of
network address translation (NAT), which partially alleviates address
exhaustion. The
U.S. Government has specified that all federal agencies must deploy IPv6 by
2008. It is expected that IPv4 will be supported alongside IPv6 for the foreseeable
future.
Invar Mask Picture Tube
- Institutional Televisions feature the Invar Shadow Mask that eliminates
"doming" or flashes of light in the corners of the picture that result from
heating and cooling of the electron beam. With the invar mask, the picture is
clearer, brighter, and more
consistent.
IR -
Infrared radiation is
electromagnetic radiation of a wavelength longer than visible light, but shorter
than microwave radiation. The name means "below red" (from the Latin infra,
"below"), red being the color of visible light of longest wavelength. Infrared
radiation spans three orders of magnitude and has wavelengths between 700 nm and
1 mm.
IRC -
Internet Relay Chat is a form of
instant communication over the Internet. It is mainly designed for group
(many-to-many) communication in discussion forums called channels, but also
allows one-to-one communication.
ISDN - Integrated
Services Digital Network. A set of protocols and interface standards that
effectively constitutes an integrated telephone network. ISDN can transmit
digital data and voice, ideal for videoconferencing.
ISDN BRI - Basic
Rate Interface.
Delivers service on one or two 64 kbps full duplex “B” channels plus one 16 kbps
“D” channel for control and signaling
ISDN PRI - Primary
Rate Interface. 23B+D channels (30B + D in Europe) with 64 kbs D channel.
Provides 1.54 Mbps in North America and up to 2.048 Mbps in Europe.
ISO -
International Organization for Standardization or International Standardization
Organization. Establishes and coordinates worldwide standards for
electronic information exchange.
Isochronous -
Used to describe the transmission
of continuous media, implying finite size data samples generated at fixed
intervals. For
example,
multimedia
streams require an
isochronous transport mechanism to ensure that data is delivered as fast as it
is displayed and to ensure that the audio is synchronized with the video.
Certain types of networks, such as
ATM, are said to be
isochronous because they can guarantee a specified
throughput. Likewise, new
bus architectures, such
as
IEEE 1394, support
isochronous delivery.
Isochronous Ethernet -
The main idea of Isochronous
Ethernet is to combine the advantages of a shared high speed communications
channel for bursty packed based data traffic like Ethernet and
synchronous/isochronous channels for multimedia traffic where minimal delay and
guaranteed bandwidth is important. Isochronous Ethernet uses the same
CAT-3 twisted pair wires as 10 Base-T, therefore switching to this new
system does not require rewiring an existing 10 Base-T installation.
Isochronous Ethernet uses a different encoding scheme than traditional Ethernet
and gains 6.384 MBit/s bandwidth. This way it can provide the usual 10 MBit/s
for data traffic and use the additional capacity for the multimedia traffic. The
6.384 MBit/s are split up into 96 ISDN 64 KBit/s channels and some others for
signaling and control.
ISUP - ISDN User Part.
Signaling System No. 7 protocol.
ITU - The International
Telecommunications Union (ITU), formerly known as CCITT, headquartered in
Geneva, Switzerland is an international organization within which governments
and the private sector coordinate global telecom networks and services.
ITV or IATV - InterActive
TeleVideo
BACK TO TOP
J
J-Carrier
- Japanese version of the
T-carrier system of North America.
J2EE - Java Platform,
Enterprise Edition or Java EE (formerly known as Java 2
Platform, Enterprise Edition or J2EE up to version 1.4), is a programming
platform—part of the
Java
platform—for developing and running distributed
multi-tier architecture
Java
applications, based largely on modular
software components running on an
application server. The Java EE platform is defined by a specification.
Java EE is also considered informally to be a
standard because providers must agree to certain conformance requirements in
order to declare their products as Java EE compliant; albeit with no
ISO or
ECMA standard. Java EE includes several
API specifications, such as
JDBC, client-side
applets,
RPC, CORBA,
and defines how to coordinate them. Java EE also features some specifications
unique to Java EE for components. These include
Enterprise Java Beans,
servlets,
portlets
(following the
Java Portlet specification),
JavaServer Pages and several
web
service technologies. This allows the developer to create an
enterprise application that is portable between platforms and scalable,
while integrating with legacy technologies.
J2ME - see Java Platform,
Micro Edition or Java ME.
JAIN -
Java APIs for Integrated
Networks (JAIN) is an activity within the Java Community Process, developing
APIs for the creation of telephony (voice and data) services. Originally, JAIN
stood for Java APIs for Intelligent Network.
The name was later changed to Java APIs for Integrated Networks to
reflect the widening scope of the project. The JAIN activity consists of a
number of "Expert Groups", each developing a single API specification.
JAIN is part of a
general trend to open up service creation in the telephony network so that, by
analogy with the Internet, openness should result in a growing number of
participants creating services, in turn creating more demand and better, more
targeted services. A major goal of the JAIN APIs is to abstract the
underlying network, so that services can be developed independent of network
technology, be it traditional PSTN or Next Generation Network. The JAIN
effort has produced around 20 APIs, in various stages of standardization,
ranging from Java APIs for specific network protocols, such as SIP and TCAP, to
more abstract APIs such as for call control and charging, and even including a
non-Java effort for describing telephony services in XML. There is overlap
between JAIN and Parlay/OSA because both address similar problem spaces.
However, as originally conceived, JAIN focused on APIs that would make it easier
for network operators to develop their own services within the framework of
Intelligent Network (IN) protocols. As a consequence, the first JAIN APIs
focused on methods for building and interpreting SS7 messages and it was only
later that JAIN turned its attention to higher-level methods for call control.
Meanwhile, at about the same time JAIN was getting off the ground, work on
Parlay began with a focus on APIs to enable development of network services by
non-operator third parties.
JAVA
- was invented in 1995. JAVA
is a programming language from Sun Microsystems designed primarily for writing
software on the web host to download over the internet to PC end users.
Initially JAVA was used to bring motion to static Web pages. For more
information go to: http://java.sun.com
JavaBeans -
JavaBeans are
software components written in the
Java programming language. The JavaBeans specification by
Sun Microsystems defines them as "reusable software components that can be
manipulated visually in a builder tool". In spite of many similarities, JavaBeans should not be confused with
Enterprise JavaBeans (EJB), a server-side component technology that is part
of Java EE.
Java EE - Java Platform, Enterprise Edition or
Java EE (formerly known as Java 2 Platform,
Enterprise Edition or J2EE up to version 1.4), is a programming platform—part of
the
Java platform—for developing and running distributed
multi-tier architecture
Java
applications, based largely on modular
software components running on an
application server. The Java EE platform is defined by a specification.
Java EE is also considered informally to be a
standard because providers must agree to certain conformance requirements in
order to declare their products as Java EE compliant; albeit with no
ISO or
ECMA standard. Java EE includes several
API specifications, such as
JDBC, client-side
applets,
RPC, CORBA,
and defines how to coordinate them. Java EE also features some specifications
unique to Java EE for components. These include
Enterprise Java Beans,
servlets,
portlets
(following the
Java Portlet specification),
JavaServer Pages and several
web
service technologies. This allows the developer to create an
enterprise application that is portable between platforms and scalable,
while integrating with legacy technologies.
Java ME -
Java Platform, Micro
Edition or Java ME (formerly referred to as Java 2 Platform, Micro
Edition or J2ME), is a collection of
Java
APIs for the development of software for resource constrained devices such
as
PDAs,
cell phones and other consumer appliances. Java ME is formally a
specification, although the term is frequently used to also refer to the runtime
implementations of the specification. Java ME was developed under the
Java Community Process as JSR 68. The evolution of the platform has
abandoned the umbrella Java Specification Request in favor of separate JSRs for
the different flavors of Java ME. Java ME was designed by
Sun Microsystems and is a replacement for a similar technology,
PersonalJava. Java ME has become a popular option for creating games for cell phones, as they
can be emulated on a
PC during the development stage and easily uploaded to the phone. This
contrasts with the difficulty of developing, testing, and loading games for
other special gaming platforms such as those made by
Nintendo,
Sony, and others,
as expensive system-specific hardware and kits are required. Sun Microsystems has tended not to provide free binary implementations of its
Java ME runtime environment for mobile devices, rather relying on third parties
to provide their own, in stark contrast to the numerous binary implementations
it provides for the full
Java
platform standard on server and workstation machines. One of the notable
omissions is for
Microsoft
Windows Mobile (Pocket PC) based devices, despite an
open letter campaign to Sun to release a
rumored complete project "Captain
America" which is such an implementation.
Java SE - Java
Platform, Standard Edition or Java SE (formerly known up to version
5.0 as Java 2 Platform, Standard Edition or J2SE), is a collection of Java
programming language APIs useful to many Java platform programs. The Java
Platform, Enterprise Edition includes all of the classes in the Java SE, plus a
number which are more useful to programs running on servers than on
workstations. Starting with the J2SE 1.4 version (Merlin), the Java SE platform has been
developed under the
Java Community Process. JSR 59 was the umbrella specification for J2SE 1.4
and JSR 176 specified J2SE 5.0 (Tiger).
As of 2006,
Java SE 6 (Mustang) is being developed under JSR 270. The following are descriptions of some of the primary Java SE packages. For a
complete list of packages see the
J2SE 5.0 API Javadocs.
Java Portlet Specifications - defines a contract between the portlet
container and
portlets and provides a convenient programming model for portlet developers.
The Java Portlet Specification V1.0 was developed under the
Java Community Process as JSR 168.
The Java Portlet Specification V1.0 introduces the basic portlet programming
model with:
 |
two phases of action
processing and rendering in order to support the Model-View-Controller
pattern. |
 |
portlet modes, enabling the
portal to advise the portlet what task it should perform and what content it
should generate |
 |
window states, indicating the
amount of portal page space that will be assigned to the content generated
by the portlet |
 |
portlet data model, allowing
the portlet to store view information in the render parameters, session
related information in the portlet session and per user persistent data in
the portlet preferences |
 |
a packaging format in order to
group different portlets and other J2EE artifacts needed by these portlets
into one portlet application which can be deployed on the portal server.
|
JAVA Servlet -
The Java Servlet API allows a
software developer to add dynamic content to a
Web server
using the
Java
platform. The generated content is commonly
HTML, but may be
other data such as XML.
Servlets are the Java counterpart to dynamic web content technologies such as
CGI, PHP or
ASP. Servlets can maintain state across many server transactions by using
HTTP
cookies,
session variables or
URL
rewriting. The Servlet
API, contained in the
Java
package hierarchy
javax.servlet, defines the expected interactions of a
web
container and a servlet. A web container is essentially the component of a
web server that interacts with the servlets. The web container is responsible
for managing the lifecycle of servlets, mapping a URL to a particular servlet
and ensuring that the URL requester has the correct access rights. A
Servlet is an
object that receives requests (ServletRequest)
and generates a response (ServletResponse)
based on the request. The API package
javax.servlet.http defines
HTTP subclasses of
the generic servlet (HttpServlet)
request (HttpServletRequest)
and response (HttpServletResponse)
as well as an (HttpSession)
that tracks multiple requests and responses between the web server and a client.
Servlets may be packaged in a
WAR file as
a
Web application. Moreover, servlets can be generated automatically by
JavaServer Pages (JSP), or alternately by template engines such as
WebMacro.
Often servlets are used in conjunction with JSPs in a pattern called "Model
2", which is a flavor of the
model-view-controller pattern.
JavaServer Faces -
JavaServer Faces (JSF) is a
Java-based
Web application framework that simplifies the
development of
user interfaces for
Java EE
applications. Out of the box, JSF uses
JavaServer Pages for its display technology, but JSF can also accommodate
other display technologies, such as
XUL, for example. JSF
includes:
 | A set of APIs for
representing user interface (UI) components and managing their state,
handling events and input validation, defining page navigation, and
supporting internationalization and accessibility |
 | A default set of UI
components |
 | Two JavaServer Pages (JSP)
custom tag libraries for expressing a JavaServer Faces interface within a
JSP page. |
 | A server-side event model
|
 | State management
|
 | Managed Beans
(JavaBeans created with dependency injection) |
The JSF specification was
developed under the Java Community Process as
JSR 127, which defined JSF 1.0 and 1.1. As of 2006, JSF 1.2 is
being developed as JSR 252.
JavaServer Pages -
JavaServer Pages (JSP) is a
Java technology that allows
software developers to dynamically generate
HTML,
XML or other types of
documents in response to a Web client request. The technology allows Java code
and certain pre-defined actions to be embedded into static content. The JSP syntax adds additional XML tags, called JSP actions, to be used to
invoke built-in functionality. Additionally, the technology allows for the
creation of JSP tag libraries that act as extensions to the standard HTML or XML
tags. Tag libraries provide a
platform independent way of extending the capabilities of a
Web server. JSPs are compiled into
Java
Servlets by a
JSP
compiler. A JSP compiler may generate a servlet in Java code that is then
compiled by the Java compiler, or it may generate
byte code
for the servlet directly. In either case, it is helpful to understand how the
JSP compiler transforms the page into a Java servlet. For an example, consider
the input
here, and its resulting generated Java Servlet
here. Architecturally speaking, JSP can be viewed as a high-level abstraction of
servlets that is implemented as an extension of the Servlet 2.1 API. Both
servlets and JSPs were originally developed by Sun Microsystems. Starting with
version 1.2 of the JSP specification, JavaServer Pages have been developed under
the Java Community Process. JSR 53 defines both the JSP 1.2 and Servlet 2.4
specifications and JSR 152 defines the JSP 2.0 specification. As of 2006 the JSP
2.1 specification is being developed under JSR 245.
Jitter -
A flickering on a display screen.
Besides a monitor or connector malfunction, jitter can be caused by a slow
refresh rate.
JMS -
The Java Message Service (JMS)
API is a Java Message Oriented Middleware (MOM) API for sending messages between
two or more clients. JMS is a specification developed under the Java Community
Process as JSR 914. As of 2006, the current version is JMS 1.1.
JTAPI - JAVA Telephony API.
A set of modularly-designed, application programming interfaces for Java-based
computer telephony applications. JTAPI consists of one Core package and
several extension packages. JTAPI applications are portable across
platforms without modifications.
BACK TO TOP
K
Kerberos -
is a network authentication
protocol developed by MIT in the 1980s. It is designed to provide strong
authentication for client/server applications by using secret-key cryptography.
KVM Switch -
Keyboard/Video/Mouse Switch. A switched box used to control multiple
computers from a single keyboard, monitor, and mouse.
BACK TO TOP
L
Latency -
The length of time it takes a
packet to move from source to destination; delay.
Laser -
Light Amplification by Stimulated
Emission of Radiation is a device which uses a quantum mechanical effect,
stimulated emission, to generate a coherent beam of light from a lasing medium
of controlled purity, size, and shape. The output of a laser may be a
continuous, constant-amplitude output (known as CW or continuous wave),
or pulsed, by using the techniques of Q-switching, modelocking, or
gain-switching. In pulsed operation, much higher peak powers can be achieved. A
laser medium can also function as an optical amplifier when seeded with
light from another source. The amplified signal can be very similar to the input
signal in terms of wavelength, phase, and polarization; this is particularly
important in optical communications. The verb "to lase" means "to produce
coherent light" or possibly "to cut or otherwise treat with coherent light", and
is a back-formation of the term laser.
Lawful Intercept -
Lawful interception (aka
wiretapping) of telecommunications. Interception of telecommunications by
law enforcement authorities (LEA's) and intelligence services, in accordance
with local law and after following due process and receiving proper
authorization from competent authorities. Various countries have different rules
with regards to lawful interception. In the
United States the law is known as
CALEA, in
CIS countries as
SORM. With the existing Public Switched Telephone Network (PSTN),
Lawful Interception (LI) is performed by applying a 'tap' on the telephone line
of the target in response to a warrant from a Law Enforcement Agency (LEA).
However,
Voice
over IP (VoIP) technology has enabled the mobility of the end-user, so it is
no longer possible to guarantee the interception of calls based on tapping a
physical line. Whilst the detailed requirements for LI differ from one jurisdiction to another,
the general requirements are the same. The LI system must provide transparent
interception of specified traffic only, and the subject must not be aware of the
interception. The service provided to other users must not be affected during
interception.
Light -
is electromagnetic radiation with
a wavelength that is visible to the eye, or in a more general sense, any
electromagnetic radiation in the range from infrared to ultraviolet. The three
basic dimensions of light (and of all electromagnetic radiation) are:
intensity (or brilliance or
amplitude, perceived by humans as the brightness of the light), frequency (or
wavelength, perceived by humans as the color of the light), and polarization (or
angle of vibration and not perceivable by humans under ordinary circumstances).
The speed of light is
227,000 kilometers per second (approximately 141,050 miles per second).
Line Doublers - An
increased definition television unit that doubles the number of scan lines in a
video picture. This fills the space between the original lines, making them less
noticeable.
Local PreviewTM -
Channel Guide - Automatically displays pre-programmed channel guide every
time the television is turned on. After choosing the channel to view, channel
guide fades off the screen to be displayed again when called up using the
remote.
Long Power Cords - Using
extension cords violates safety regulations in some commercial buildings.
Commercial televisions with an 8'-12' power cord for convenient access to
electrical outlets.
Loop-Through Capabilities
- Institutional Televisions offer users the ability to loop composite video,
S-Video, or even VGA from one set to another set from a single source. This
means that multiple sets can display exactly the same programming at the same
time from one VCR or other video source.
Lossless compression -
Refers to data compression
techniques in which no data is lost. For most types of data, lossless
compression techniques can reduce the space needed by only about half. Lossless compression
technique is used when compressing data files and programs. Also, The
Graphics Interchange File (GIF) is an image format used on the Web that provides
lossless compression.
Lossy
compression -
Refers to data compression techniques in which
some amount of data is lost.
Only certain types of data can
tolerate lossy compression.
Lossy compression technologies attempt to eliminate
redundant or unnecessary information. Most video compression technologies, such
as MPEG, use a lossy technique. Also,
the JPEG
image file, commonly used for photographs and other complex still images on the
Web, is an image that has lossy compression. Using JPEG compression, the creator
can decide how much loss to introduce and make a trade-off between file size and
image quality.
Low Cost Solution -
upgrade and add capabilities without having to buy new televisions.
Luminance
-
The
monochrome or black and white part (Y) of a video signal that provides
brightness information. Measured in lux, lumens, or footcandles.
BACK TO TOP
M
MAP -
Mobile Application Part (MAP) is a standard of the European Telecommunications
Standards Institute (ETSI) for enabling GSM subscribers that roam between
different wireless service operators’ networks to make and receive voice calls. MAP provides an application layer for the various nodes in the core
mobile network to communicate with each other in order to provide services to
mobile phone users. MAP relies on ETSI/3GPP Standards :a-) in GSM Only versions (before R4) : TR 09.02 ; b-) From 3G/GSM R99 versions : TS 29.002. MAP is implemented on the SS7 family of protocols,
and it uses SCCP Sub System Numbers. The main operations executed
by MAP are: 1-) Mobility Management, 2-) Operation and Maintenance, 3-) Call Handling, 4-) Supplementary Services,
and 5-) Short Message Service.
Marquee Channel TM -
This feature allows Institutional Televisions to default to a pre-selected
channel whenever they're turned on. Users may specify any channel or source as
the marquee channel.
MBONE -
Multicast Backbone. The MBONE is a
system of transmitting audio and video over a multicast network. Mostly
available at universities and government facilities, the MBONE can be thought of
as a testbed for technologies that will eventually be promulgated across the
larger internet. The MBONE has been replaced on the vBNS and Abilene by native
multicast support.
Megaco - a contraction of "Media Gateway Controller", Megaco is a
signaling protocol, used between a Media Gateway and a Media
Gateway Controller (also known as a Call Agent or a Soft Switch) in a
VoIP network. It
defines the necessary signaling mechanism to allow a Media Gateway Controller
(Call agent) to control gateways in order to support voice/fax calls between
PSTN-IP or IP-IP networks. This protocol is defined by IETF
RFC 3525 and was the result of joint work of
IETF and
ITU. It is also known as H.248.
H.248 is the name
given to it by the ITU, Megaco is the IETF name.
Message - or messaging in its most general meaning is an object of
communication. Depending on the context, the term may apply to both the
information contents and its actual presentation.
In the
communications discipline, a message is
information which is sent from a
source to a receiver. Some common definitions include:
 | Any thought or idea
expressed briefly in a plain or secret language, prepared in a form suitable
for transmission by any means of communication. |
 | An arbitrary amount of
information whose beginning and end are defined or implied. |
 | Record information, a
stream of data expressed in plain or encrypted language (notation) and
prepared in a format specified for intended transmission by a
telecommunications system. |
In the Actor model a message is similarly an Actor itself that is sent
asynchronously from one Actor to another. In languages such as Smalltalk-80 and Objective-C an instance of a class method
is called (confusingly) a message.
Metadata -
Data about data. Meta data describes how and when and by
whom a particular set of data was collected, and how the data is formatted. Meta
data is essential for understanding information stored in data warehouses.
Types of Metadata:
Relational database metadata, Data warehouse metadata, General IT metadata, File
system metadata, Image metadata, Program metadata, Metamodels, Strange metadata,
and Digital library metadata.
Metadata
registry is a central location in an organization where metadata definitions
are stored and maintained in a controlled method.
MHz (as in 8 MHz) - An
abbreviation for megahertz. This is a unit of measurement and refers to a
million cycles per second. For example bandwidth, in television context, is
measured in megahertz.
MIDI -
Musical Instrument Digital
Interface is a standard for connecting electronic musical instruments and
computers. MIDI files can be thought of as digital sheet music, where the
computer acts as the musician playing back the file. MIDI files are much smaller
than digital audio files, but the quality of playback will vary from computer to
computer.
MMS -
Multimedia Messaging Service is a
technology for transmitting not only text messages, but also various kinds of
multimedia content (e.g. images, audio, and/or video clips) over wireless
telecommunications networks using the Wireless Application Protocol (WAP). It is
standardized by 3GPP and 3GPP2.
Mobility Management -
Mobility Management is one of the major functions of a GSM or a UMTS network
that allows mobile phones to work. The aim of mobility management is to track
where the mobile subscribers are, so that calls, SMS and other mobile phone services
can be delivered to them. A GSM or
UMTS network, like
all
cellular networks, is a
radio
network of individual
cells,
known as base stations. Each base station covers a small geographical area which
is part of a uniquely identified location area.
By integrating the coverage of each of these base stations, a cellular network
provides a radio coverage over a very much wider area. A group of base stations
is called a location area, or a
routing area. The location update procedure allows a
mobile device
to inform the cellular network, whenever it moves from one location area to the
next. Mobiles are responsible for detecting location area codes. When a mobile
finds that the location area code is different from its last update, it performs
another update by sending to the network, a location update request, together
with its previous location, and its Temporary Mobile Subscriber Identity (TMSI). There are several reasons why a mobile may provide updated location information
to the network. Whenever a mobile is switched on or off, the network may require
it to perform an
IMSI attach or
IMSI detach location update procedure. Also, each mobile is required to
regularly report its location at a set time interval using a
periodic location update procedure. Whenever a mobile moves from one
location area to the next while not on a call, a
random location update is required. This is also required of a stationary
mobile that reselects coverage from a cell in a different location area, because
of signal fade. Thus a subscriber has reliable access to the network and may be
reached with a call, while enjoying the freedom of mobility within the whole
coverage area.
Modular Tuner -
X-channel (e.g. 181-channel) modular tuner with Auto Programming.
Modulation
- is the addition of information (or the signal) to an electronic or optical
signal carrier. Modulation can be applied to direct current
(mainly by turning it on and off), to alternating current, and to optical
signals.
Morse code, invented for telegraphy and still used in amateur
radio, uses a binary (two-state) digital code similar
to the code used by modern computers. For most of radio and telecommunication
today, the carrier is alternating current (AC) in a given range of
frequencies. Common modulation methods include: Amplitude
modulation (AM), in which the voltage applied to the carrier is
varied over time, Frequency modulation (FM), in which the
frequency of the carrier waveform is varied in small but meaningful
amounts, Phase modulation (PM), in which the natural flow of the
alternating current
waveform is delayed temporarily. These are also known as
continuous wave modulation methods to distinguish them from pulse code
modulation (PCM), which is used to encode both digital and analog
information in a binary way. Radio and television
broadcast stations typically use AM or FM. Most two-way radios use
FM, although some employ a mode known as single sideband (SSB).
More complex forms of modulation are Phase Shift Keying (PSK) and
Quadrature Amplitude Modulation (QAM). Optical signals are
modulated by applying an electromagnetic current to vary the intensity of a
laser beam.
MOM -
Message Oriented Middleware is a category of inter-application
communication software that relies on
asynchronous message passing as opposed to a request/response metaphor. Most message oriented middleware (MOM) is based around a
message queue system, although there are implementations that rely on a
broadcast
or multicast
messaging system. MOM requires an extra component in the architecture, the
message transfer agent.
Monitor Output Capability
- Monitor output allows simple recording of whatever source is resident on the
television screen.
Monitoring - The status
of every TV in the network is continuously monitored, providing verification
that televisions are on-line and operating in compliance with content
distribution requirements (power on, correct channel and volume, valid signal,
etc.). Quick notification is provided at the computer head-end control when a TV
is off-line, malfunctioning, disconnected, or being used for unauthorized
programming. System operation is documented in log files, providing a record of
scheduled event control commands, system outages, and televisions requiring
attention.
MPEG -
MPEG (Moving Picture Experts
Group) is a series of ISO standards for digital video and audio, designed for
different uses and data rates. More information can be found at:
http://www.mpegif.org
MPEG-1 - The initial MPEG
standard, designed to encode full motion video so it could be played back off of
a CD (150 kb/s). The bit rate of a standard MPEG1 is 1.5Mbps. MPEG-1 has a frame
size of 352x240 pixels, which gives a picture quality slightly better than VHS
video tape. MPEG-1 included three audio standards, most video systems use MPEG-1
layer 1 or layer 2 audio. MPEG-1 layer 3 audio (commonly known as MP3), is being
used widely for audio on the Internet.
MPEG-2 was a follow-on
standard supporting higher data rates, and thus higher quality. MPEG-2 is the
standard used in DVD video players, most digital satellite systems in North
America, and in the new North American Digital TV system.
MPEG-3 was abandoned as its
planned functionality was included in MPEG-2.
MPEG-4 is a draft standard
that will be better suited for use on the Internet. MPEG4 delivers video at
comparable quality to MPEG1 at a much lower bit rate. MPEG-4 also supports a
wide variety of elements that can be transmitted separately and combined to form
the video frame, such as a talking head in one stream and the background in
another. That is, MPEG4 allows manipulation of objects within the video stream
(addition, subtraction, object manipulation, etc.). If you don't like where a
chair is in the video, you can move it (providing the chair has been coded as a
moveable object, of course). For more information try the following site:
http://bmrc.berkeley.edu/frame/research/mpeg/mpegfaq.html
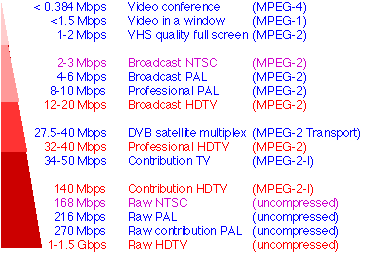
MPEG-7 - formally named
“Multimedia Content Description Interface”, is a standard for describing the
multimedia content data that supports some degree of interpretation of the
information’s meaning, which can be passed onto, or accessed by, a device or a
computer code. MPEG-7 is not aimed at any one application in particular; rather,
the elements that MPEG-7 standardizes support as broad a range of applications
as possible.
More information about MPEG-7 can be found at the MPEG home page (http://www.chiariglione.org/mpeg/)
and the MPEG-7 Alliance website (http://www.mpeg-industry.com).
These web pages contain links to a wealth of information about MPEG, including
much about MPEG-7, many publicly available documents, several lists of
‘Frequently Asked Questions’ and links to other MPEG-7 web pages.
MPLS - Multi-protocol Label Switching. A computer
networking and telecommunications layer 2.5 protocol as it lies between Layer 2
and Layer 3 of the OSI reference model. MPLS has adopted many technically
sound ideas from ATM. Computer networking are mostly based on
large packet switching (e.g. Ethernet 1500-byte) coupled with the advancement in the large
modern optical networks more specifically the switching speed (10 Gbps and
well beyond) and the reduced
transmission
error rates (almost errorless) advancement in modern optical networks have opened the
door to new network protocols. MPLS is such a protocol, designed mainly to
forward IP datagrams and Ethernet traffic. MPLS can be used to carry many
different kinds of traffic, including IP packets, as well as native ATM, SONET,
and Ethernet frames. In the field of VPNs, L2TPv3 is
emerging as a potential competitor to MPLS, particularly in existing networks
with IP-only cores.
MPLS is currently in use in large "IP Only" networks, and is standardized by
IETF in
RFC 3031. In practice, MPLS is mainly used to forward
IP datagrams and
Ethernet
traffic. Major applications of MPLS are
Telecommunications traffic engineering and
MPLS VPN.MSISDN -
The Mobile Station Integrated Services Digital Network is
the mobile equivalent of
ISDN. Used as a
value, MSISDN refers to the Mobile Subscriber ISDN Number, which is a max
15-digit number. There are
mobile phones on the market that can have several MSISDNs in one SIM Card.
E.g. a German MSISDN and a French MSISDN in one SIM card would allow the user to
be reached under two numbers.
MTSO - Mobile Telephone Switching Office -
The central switch that controls the entire operation of a cellular system. It
is a sophisticated computer that monitors all cellular calls, tracks the
location of all cellular-equipped vehicles traveling in the system, compiling
call information for billing, connects all of the individual cell towers to the
Central Office (CO). The MTSO arranges
handoffs by monitoring the relative signal strength of your cellular phone as
reported by each of the cell towers, and switching your conversation to the cell
tower which will give you the best possible reception. The MTSO is an
operations center that connects the landline PSTN system to the mobile phone
system.
Multi-tier Architecture -
In software engineering, multi-tier architecture (often referred to as
n-tier architecture) is a client-server architecture in which an application
is executed by more than one distinct software agent. For example, an
application that uses middleware to service data requests between a user and a
database employs multi-tier architecture. The most widespread use of "multi-tier
architecture" refers to three-tier architecture.
Multipath -
In wireless telecommunications, multipath is the propagation phenomenon
that results in radio signals' reaching the receiving antenna by
two or more paths. Causes of multipath include atmospheric
ducting, ionospheric reflection and refraction, and reflection
from terrestrial objects, such as mountains and buildings.
The effects of multipath include constructive and destructive
interference, and phase shifting of the signal. This causes Rayleigh fading, named after Lord Rayleigh. The standard
statistical model of this gives a distribution known as the
Rayleigh distribution. Rayleigh fading with a strong line
of sight content is said to have a Rician distribution, or to be
Rician fading. In facsimile and television transmission,
multipath causes jitter and ghosting, seen as a faded duplicate
image to the right of the main image. In digital radio
communications (such as GSM) multipath can cause errors and
affect the quality of communications. The errors are due to
Inter-symbol interference (ISI). Equalisers are often used to
correct the ISI. Alternatively, techniques such as orthogonal
frequency division modulation and Rake receivers may be used. Multiplexing -
More information
can be conveyed in a given amount of time by dividing the
bandwidth of a signal carrier so that more than one modulated
signal is sent on the same carrier. Known as multiplexing, the carrier is
sometimes referred to as a channel and each separate signal carried
on it is called a sub-channel. (In some usages, each sub-channel is
known as a channel.) The device that puts the separate signals on the carrier
and takes them off of received transmissions is a multiplexer. Common types of
multiplexing include frequency-division multiplexing (FDM) and
time-division multiplexing (TDM). FDM is usually used for analog
communication and divides the main frequency of the carrier into separate
subchannels, each with its own frequency band within the overall bandwidth. TDM
is used for digital communication and divides the main signal into time-slots,
with each time-slot carrying a separate signal.
Multipoint Conferencing Server
(MCS) (also MCU) -
A hardware or software H.323
device that allows multiple video conferencing (or audio or data) users to
connect together. Without an MCS typically only point to point conferences can
take place. Commonly supports voice activated switching, where whoever is
talking is broadcast to all users, but new systems support "Hollywood squares",
where multiple windows show each participant. ITU-T standard H.231 describes the
standard way of doing this. Many current systems only support H.320 (ISDN) but
many vendors are working to upgrade their products to support H.323 (LAN,
Internet) as well. In the H.320 space, this functionality is referred to as a
multipoint control unit (MCU). Sometimes these terms are used interchangeably,
although they refer to somewhat different implementations.
Multithreading - see
Thread.
Multimedia and Computer
Display Capability - Accepts XGA, SVGA, VGA and Mac Signals, composite video
with audio, S-Video with audio for greater picture and sound performance in
conjunction with computers, video cameras, VCRs, DVD players, Laser Disc
players, Web browsers and satellite receiver systems.
Multiple Input/Output
Capabilities - Institutional Televisions feature a multitude of input/output
capabilities including board interface slot, S-Video input/output, two audio
inputs, Composite Video input/output, Smart PlugTM interface, and RF
input.
MVNO - A Mobile Virtual
Network Operator (MVNO) functions as a wireless service operator in the
marketplace though it does not own an actual wireless network. Host Network
Operator (HNO) is a related term. The HNO is the actual owner and operator of
the wireless network, which includes the towers and all of the switching
equipment.
BACK TO TOP
N
NAPTR - Naming
Authority Pointer and is a newer type of DNS record that supports
regular expression based
rewriting. Several NAPTR records can be chained together creating fairly
sophisticated URI rewriting rules. A
record can go through any number of rewrites before reaching a terminal
condition. For example, after translating the phone number +1-770-555-1212
into the URI
2.1.2.1.5.5.5.0.7.7.1.e164.arpa
as described by E.164,
DDDS is used to transform it using rewrite
rules gathered from NAPTR records. The
BIND configuration for the records returned
from a query for
2.1.2.1.5.5.5.0.7.7.1.e164.arpa
might look like:
$ORIGIN
2.1.2.1.5.5.5.0.7.7.1.e164.arpa.
IN NAPTR 100 10 "u" "sip+E2U" "!^.*$!sip:information@pbx.example.com!i"
.
IN NAPTR 102 10 "u"
"smtp+E2U" "!^.*$!mailto:information@example.com!i" .
Of these two records, the first has an order value of 100
which is lower than 102 so it is picked first. The preference of 10 is
unimportant as no other rules have an order of 100. The "u" signifies a terminal
rule in ENUM and URI
applications, so the output of this rewrite will be the answer we are looking
for. If we support the service designated with the key "sip+E2U", we won't go on
to investigate other rules with higher order values. The rewrite regular
expression "!^.*$!sip:information@pbx.example.com!i"
is evaluated transforming our original request of
2.1.2.1.5.5.5.0.7.7.1.e164.arpa
into sip:information@pbx.example.com. In the regular expression, the exclamation
mark '!' will be our delimiter (we avoid the use of '/' and '\' because they may
be interpreted as escape sequences somewhere else). The "^.*$" in the RE says
"starting at the beginning, including any characters and ending at the end" (in
other words, everything) is changed to "sip:information@pbx.example.com" and 'i'
ignores case. (Observant readers will notice that the 'i' doesn't matter, given
the use of ".*") For those familiar with Perl REs, the equivalent RE could be
written as "/^.*$/mailto:information@example.com/i". So the resulting URI "sip:information@pbx.example.com"
will be used. If we didn't support SIP, we would effectively fall back to the
rule resulting in "mailto:information@example.com".
Narrowband - (narrow bandwidth) refers to a signal which occupies only a
small amount of space on the radio spectrum -- the opposite of
broadband or wideband. This is entirely relative to what
is being described; for example, an FM broadcast station takes
up 150~200kHz on the FM band, whereas a TV station's audio is
narrowband, taking up only 25kHz, and weatheradio broadcasts are
even narrower than that. It is also very often used to describe
radio antennas, called narrowband when they are designed
specifically for one frequency or channel only instead of a wide
range.
Narrowband can
also be used with the audio spectrum to describe sounds which
occupy a narrow range of frequencies. In telephony narrowband is
usually considered to cover frequencies 300-3400Hz.
NAS - Network Access Server is a single point of access to a remote
resource. A client connects to the NAS and then the NAS connects to
another resource (e.g. RADIUS) to authenticate the client.
NAT-PT/NAPT-PT: from 3GPP, NAT-PT uses a pool of
globally unique IPv4 addresses for assignment to IPv6 nodes on a dynamic basis
as sessions are initiated across the IP version boundaries. NAT-PT binds
addresses in IPv6 network with addresses in IPv4 network and vice versa to
provide transparent routing between the two IP domain without requiring any
changes to end points, like the UE. NAT-PT needs to track the sessions it
supports and mandates that inbound and outbound data for a specific session
traverse the same NAT-PT router.
NAPT-PT provides additional translation of transport identifier (e.g., TCP and
UDP port numbers, ICMP query identifiers). This allows the transport identifiers
of a number of IPv6 hosts to be multiplexed into the transport identifiers of a
single assigned IPv4 address. See RFC 2766 [33] for more details.
Net1 System Television Control - Adds networking capability to television
and allows television to be controlled from a central location via an RF
distribution system.
Network Engineering -
In
telecommunication, the term network engineering has the following
meanings: 1.) In
telephony, the discipline concerned with (a) determining
internetworking service requirements for switched networks, and (b)
developing and implementing
hardware
and software
to meet them. 2.) In
computer science, the discipline of hardware and
software engineering to accomplish the design goals of a
computer network. 3.) In radio
communications, the discipline concerned with developing
network topologies.
Network Planning and Design -
Network planning and
design is an iterative process, encompassing
topological design,
network-synthesis, and network-realization,
and is aimed at ensuring that a new network or service meets the needs of the
subscriber and operator. The process can be tailored according to each new
network or service. This is an extremely
important process which must be performed before the establishment of a new
telecommunications
network or service.
Network Switching Subsystem -
Network Switching Subsystem is the component of a
GSM system that
carries out switching functions and manages the communications between
mobile phones and the
Public Switched Telephone Network (PSTN). It is owned and deployed by
mobile phone operators and allows mobile phones to communicate with each
other and
telephones in the wider
telecommunications network. The architecture closely resembles a
telephone exchange, but there are additional functions which are needed
because the phones are not fixed in one location. Each of these functions handle
different aspects of
mobility management and are described in more detail below. The Network Switching Subsystem, also referred to as the GSM core network,
usually refers to the circuit-switched core network, used for traditional
GSM
services such as voice calls,
SMS, and
Circuit Switched Data calls. There is also an overlay architecture on the GSM core network to provide
packet-switched data services and is known as the
GPRS core network. This allows
mobile
phones to have access to services such as
WAP,
MMS, and
Internet
access. All mobile phones manufactured today have both circuit and packet based
services, so most operators have a GPRS network in addition to the standard GSM
core network.
Network Topology - A
network topology is the pattern of links connecting pairs of nodes of a
network. A given node has one or more links to others, and the links can appear
in a variety of different shapes. The simplest connection is a one-way link
between two devices. A second return link can be added for two-way
communication. Modern communications cables usually include more than one wire
in order to facilitate this, although very simple bus-based networks have
two-way communication on a single wire. Network topology is determined
only by the configuration of connections between nodes; it is therefore a part
of graph theory. Distances between nodes, physical interconnections,
transmission rates, and/or signal types are not a matter of network topology,
although they may be affected by it in an actual physical network.
Networking Capability - NetCard TV allows a single television, group of
televisions or all televisions to be switched on, controlled, and tuned to a
channel for a displayed modulated video signal all from a single location.
NetCard TV allows a school-wide system of televisions to access television
programming, computer displays, or a myriad of video-based programs, and much
more.
Non-Interlaced - Also called progressive scan, this a method by which all
the video scan lines are presented on the screen in one sweep instead of two
(also see interlaced).
NTSC (National Television Standards Committee) - This is the television
standard for North America, Japan, and certain countries in South America - 525
lines/60 Hz (90 Hz Refresh).
BACK TO TOP
O
OFDM -
Orthogonal frequency-division multiplexing, also sometimes called
discrete multitone
modulation
(DMT), is a complex
modulation
technique for transmission based upon the idea of
frequency-division multiplexing (FDM) where each frequency channel is
modulated with a simpler
modulation.
In OFDM the frequencies and modulation of FDM are arranged to be
orthogonal with each other which almost eliminates the interference between
channels. Although the principles and some of the benefits have been known for
40 years, it is made popular today by the lower cost and availability of
digital signal processing components. A number of extra useful benefits, particularly
multipath
resistance, arise when the data is coded with some
Forward Error Correction (FEC) scheme prior to modulation called
channel coding. This is called Coded OFDM abbreviated to COFDM.
OLAP - On Line Analytical Processing. It is an
approach to quickly provide the answer to analytical queries that are
dimensional in nature. It is part of the broader category
business intelligence, which also includes
ETL,
relational reporting and
data
mining. The typical applications of OLAP are in business reporting for
sales,
marketing, management reporting,
business performance management (BPM),
budgeting and
forecasting, financial reporting and similar areas. The term OLAP was created as
a slight modification of the traditional database term
OLTP (On Line
Transaction Processing). Databases configured for OLAP employ a
multidimensional data model, allowing for complex analytical and ad-hoc queries
with a rapid execution time. Nigel Pendse has suggested that an alternative and
perhaps more descriptive term to describe the concept of OLAP is Fast Analysis
of Shared Multidimensional Information (FASMI). They borrow aspects of
navigational databases and hierarchical databases that are speedier than their
relational kin. In 2001 Microsoft and Hyperion announced the XML for
Analysis specification, which was endorsed by most of the OLAP vendors. It uses
MDX as a query language, MDX became the de-facto standard in the OLAP world.
There are a few types of OLAP: 1-) Multidimensional OLAP - MOLAP is the
'classic' form of OLAP and is sometimes referred to as just OLAP. MOLAP uses
database structures that are generally optimally attributes such as time period,
location, product or account code. The way that each dimension will be
aggregated is defined in advance by one or more hierarchies. 2-) Relational OLAP
- ROLAP works directly with relational databases, the base data and the
dimension tables are stored as relational tables and new tables are created to
hold the aggregated information. 3-) Hybrid OLAP (HOLAP) - There is no clear
agreement across the industry as to what constitutes "Hybrid OLAP", except that
a database will divide data between relational and specialized storage. For
example, for some vendors, a HOLAP database will use relational tables to hold
the larger quantities of detailed data, and use specialized storage for at least
some aspects of the smaller quantities of more-aggregate or less-detailed data.
In comparing the different OLAP types: Each type has certain benefits; however,
there is disagreement about the specifics of the benefits between providers.
MOLAP is better on smaller sets of data, it is faster to calculate the
aggregations and return answers and does need less storage space. ROLAP is
considered more scalable. However, large volume pre-processing is difficult to
implement efficiently so it is frequently skipped. ROLAP query performance can
therefore suffer. HOLAP is between the two in all areas, but it can
pre-process quickly and scale well. All types though are prone to database
explosion. Database explosion is a phenomenon causing vast amount of storage
space being used by OLAP databases when certain but frequent conditions are met:
high number of dimensions, pre-calculated results and sparse multidimensional
data. The difficulty in implementing OLAP comes in forming the queries, choosing
the base data and developing the schema, as a result of which most modern OLAP
products come with huge libraries of pre-configured queries. Another problem is
in the base data quality - it must be complete and consistent. Some Other
known OLAP types: 1-) WOLAP - Web-based OLAP. 2-) DOLAP - Desktop OLAP. 3-)
RTOLAP - Real-Time OLAP:
Whilst many OLAP
Servers such as
Microsoft Analysis Services store pre-calculating consolidations and
calculated elements to achieve rapid response times a Real Time OLAP Server will
calculate the values on the fly, when they are required. The essential
characteristic of RTOLAP system is that it holds all the data in RAM.
Optical Amplifier - In
fiber optics,
an optical amplifier is a device that amplifies an
optical
signal
directly, without the need to convert it to an electrical signal, amplify it
electrically, then reconvert it to an optical signal.
Optical Fiber - is a
transparent thin fiber, usually made of glass, for transmitting light. Fiber
optics is the branch of science and engineering concerned with optical fibers.
OSA -
The Open System Architecture is
part of the 3rd generation mobile telecommunications network or UMTS. OSA
describes how services are architected in an UMTS network. The standards
for OSA are being developed as part of the 3rd Generation Partnership Project
(3GPP). The standards for OSA are published by ETSI and 3GPP. The API for
OSA is called Parlay, (or Parlay/OSA or OSA/Parlay) as the APIs are developed
jointly in collaboration by 3GPP, ETSI, and the Parlay Group. These APIs can be
freely downloaded from the web. OSPF -
Open Shortest
Path First is a link-state, hierarchical Interior Gateway Protocol (IGP) routing
protocol. Dijkstra's algorithm is used to calculate the shortest path tree. It
uses cost as its routing metric. A link state database is constructed of
the
network topology which is
identical on all routers in the area. OSPF is perhaps the most
widely used IGP in large networks. It
can operate securely, using MD5 to authenticate peers before forming
adjacencies, and before accepting link-state advertisements.
A natural successor to RIP, it was VLSM capable or
classless from its inception. A newer version of OSPF (OSPFv3) now supports
IPv6 as well. Multicast extensions to OSPF (MOSPF)
have been defined, however these are not widely used. OSPF can "tag" routes, and
propagate these tags along with the routes. An OSPF network can be broken up
into smaller networks. A special area called the backbone area forms the
core of the network, and other areas are connected to it. Inter-area routing
goes via the backbone. All areas must connect to the backbone; if no direct
connection is possible, a virtual link may be established.
Routers in the same broadcast domain or at
each end of a point to point link form
adjacencies when they have discovered each other. The routers elect a
designated router (DR) and backup designated router (BDR) which act
as hub to reduce traffic between routers. OSPF uses both unicast and multicast to send 'hello
packets' and link state updates. Multicast addresses
224.0.0.5 and 224.0.0.6 are used. In contrast to RIP or BGP,
OSPF does not use TCP or UDP but uses IP directly, using IP protocol 89.
BACK TO TOP
P
P2P :
Peer-to-Peer networks and
Peer-to-Peer services.
computer network is a
network that relies primarily on the computing power and
bandwidth
of the participants in the network rather than concentrating it in a relatively
low number of
servers. P2P networks are typically used for connecting nodes via largely
ad hoc connections. Such networks are useful for many purposes. Sharing
content files (see
file
sharing) containing audio, video, data or anything in digital format is very
common, and real-time data, such as
telephony traffic, is also passed using P2P technology. A pure peer-to-peer network does not have the notion of clients or servers, but
only equal peer
nodes that simultaneously function as both "clients" and "servers" to the
other nodes on the network. This model of network arrangement differs from the
client-server model where communication is usually to and from a central
server. A typical example for a non peer-to-peer file transfer is an
FTP server where the client and server programs are quite distinct, and the
clients initiate the download/uploads and the servers react to and satisfy these
requests. Some networks and channels, such as
Napster,
OpenNAP, or
IRC @find,
use a client-server structure for some tasks (e.g., searching) and a
peer-to-peer structure for others. Networks such as
Gnutella, Freenet, or JXTA use a
peer-to-peer structure for all purposes, and are sometimes referred to as true
peer-to-peer networks, although Gnutella is greatly facilitated by directory
servers that inform peers of the network addresses of other peers. Peer-to-peer architecture embodies one of the key technical concepts of the
internet, described in the first internet
Request for Comments, "RFC
1, Host Software"
[1] dated 7
April 1969.
More recently, the concept has achieved recognition in the general public in the
context of the absence of central indexing
servers in architectures used for exchanging multimedia files. The concept of peer to peer is increasingly evolving to an expanded usage as the
relational dynamic active in distributed networks, i.e. not just computer to
computer, but human to human.
Yochai Benkler has developed the notion of commons-based peer production to
denote collaborative projects such as free software. Associated with peer
production are the concept of peer governance (referring to the manner in which
peer production projects are managed) and peer property (referring to the new
type of licenses which recognize individual authorship but not exclusive
property rights, such as the
GNU General Public License and the
Creative Commons License).
PABX -
A Private Automatic Branch Exchange (PABX) is an automatic telephone switching system within a private
enterprise. Originally, such systems - called private branch exchanges (PBX) -
required the use of a live operator. Since almost all private branch exchanges
today are automatic, the abbreviation "PBX" usually implies a "PABX."
Packet -
A unit of information sent across
a (packet-switched) network. A packet generally contains the destination address
as well as the data to be sent.
Pan and Zoom - Scroll through oversized graphics and text with the
convenience of pan and zoom. When the Zoom button is pressed, the upper left
corner of the screen is selected at maximum magnification. Then you can pan
left, right, up, or down through the rest of the document using the arrow cursor
buttons.
Parlay - The Parlay
Group is a technical industry consortium (founded 1998) that specifies APIs for
the telephone network. These APIs enable the creation of services by
organizations both inside and outside of the traditional carrier environment. In
fact, it is hoped that services can be created by IT developers, rather than
telephony experts. Important Parlay APIs include: call control,
conferencing, user interaction (audio and text messaging), and charging. The
APIs are specified in the CORBA Interface definition language and WSDL. The use
of CORBA enables remote access between the Parlay gateway and the application
code. A set of Java mappings allow the APIs to be invoked locally as well. A
major goal of the APIs is to be independent of the underlying telephony network
technology (e.g. CDMA vs. GSM vs. landline SS7). In 2003 the Parlay Group
released a new set of web services called Parlay X. These are a much simpler set
of APIs intended to be used by a larger community of developers. The Parlay X
web services include Third Party Call Control (3PCC), Location and simple
payment. The Parlay X specifications complement the more complex yet powerful
Parlay APIs. Parlay X implementations are now (Sept 2004) in commercial service
from BT and Sprint. Parlay work historically stems from the TINA effort.
Parlay is somewhat related to JAIN, and is currently (early 2003) completely
unrelated to the Service Creation Community. The Parlay Group works
closely with ETSI and 3GPP, the Parlay specifications are co-published by all
three bodies. Within 3GPP Parlay is part of Open Services Architecture, so we
often use the term Parlay/OSA.
The objective of Parlay/OSA is to provide an
API that is
independent of the underlying networking technology and of the programming
technology used to create new services. As a result the Parlay/OSA
APIs are specified in
UML. There are then a set of realizations, or mappings, for specific
programming environments: CORBA/IDL, Java, and WSDL.
Parlay X -
Parlay X is a set of telecommunications
Web
services. Parlay X is designed to enable software developers to use
capabilities from the telecom network (e.g. such as location, or the ability to
set up a call) in applications. The Parlay X Web services are defined by the
Parlay Group,
and are also a part of the
3GPP Release 6
Specifications. The principle behind Parlay X is that since Web services are widely used in the
IT industry, they are a good basis for telecommunication
service creation. There is a large number of developers and programmers who
understand Web services, and there is a wide variety of development tools. The Parlay X
APIs define a set of simple-to-use, high-level, telecom-related Web
services. Parlay X Version 1, published in May 2003, defines web services for
Third Party Call, Network Initiated Third Party Call, Send SMS, Receive SMS,
Send Message, Receive Message, Amount Charging, Volume Charging, User Status and
Terminal LocationContrast Parlay X to the more complex, but functionally richer,
Parlay APIs. A
typical Parlay X API operation is Send SMS() which may be mapped to a
series Parlay API methods. Parlay X Version 2 specifications were published by ETSI in March 2005.
Equivalent specifications are part of 3GPP Release 6.Parlay X Version 2.1 specifications are currently [Feb 2006] in development. Parlay X has been implemented by a number of telecom operators, including BT,
Korea Telecom and Sprint.
PBX - A
subscriber-owned telecommunications exchange that usually includes access to the
public switched network. 2. A switch that serves a selected group of
users and that is subordinate to a switch at a higher level military
establishment. 3. A private telephone switchboard that provides
on-premises dial service and may provide connections to local and trunked
communications networks. Note 1: A PBX operates with only a manual
switchboard; a private automatic exchange (PAX)
does not have a switchboard, a private automatic branch exchange (PABX) may or
may not have a switchboard. Note 2: Use of the term "PBX" is far
more common than "PABX," regardless of automation.
PCS - Personal Communications Services (PCS) was a name given by the FCC
to a new set of wireless services and spectrum allocated in the 1990s. Today, in
popular use, it refers to the 1900-MHz cellular frequency band.
PDC - Personal Digital Cellular (PDC) is a version of TDMA technology
used exclusively in Japan.
PDM - Product
Data Management is a category of computer software that aims to create an
automatic link between product data and a database. The information being stored
and managed (on one or more file serves) will include engineering data such as
CAD models and drawing and their associated documents. The package may also
include product visualization data. The central database will also manage
metadata such owner of a file and release status of the components. The package
will: control check-in and check-out of the product data to multi-user; carryout
engineering change management and release control on all versions/issues of
components in a product; build and manipulate the product structure BOM (Bill of
Materials) for assemblies; and assist in configurations management of product
variants. This enables automatic reports on product costs, etc. Furthermore, PDM
enables companies producing complex products to spread product data in to the
entire PLM launch-process. This significantly enhances the effectiveness of the
launch process.
Most larger CAD vendors have some kind of PDM offering.
Standard off-the-shelf CAD (Autodesk,
etc) has PDM functionality built in. CAD vendors in an industrial niche usually
have a separate closed offering (example, textile CAD -
Lectra, Gerber, etc). Other
are not industry specific and can handle multiple CAD systems (example UGS ‘s
Teamcenter)
PHS - Personal HandyFone System (PHS) is a Japan-only TDMA technology.
Originally, the difference between PDC and PHS systems was that PDC was true
cellular while PHS provided voice and data access but did not support moving
from one cell to another. PHS became the favorite wireless technology for
teenagers because of its low cost. Several years ago, groups of teens could be
seen standing on street corners under PHS cells talking on their PHS phones.
Pixel -
A term used mostly inside the U.S. that is an
abbreviation for “picture element” or the most fundamental component of a raster
display. (See Pel.)
PLM - Product
Lifecycle Management is a term used for the process of managing the entire
lifecycle of a product from its conception, through design and manufacture to
service and disposal. PLM is a set of capabilities that enable an enterprise to
effectively and efficiently innovate and manage its products and related
services throughout the entire business lifecycle. It is one of the four
cornerstones of a corporation's IT digital structure. All companies need to
manage communications and information with its customers (CRM-Customer_Relationship_Management)
and its suppliers (SCM-Supply chain management) and the resources within the
enterprise (ERM-Enterprise Relationship Management). For a manufacturing
engineering company it must also develop, describe, manage and communicate
information about its products (PLM).
PLMN - In
telecommunication, a public land mobile network is a
network that is established and operated by an
administration or by a
recognized operating agency (ROA) for the specific purpose of providing land
mobile
telecommunications services to the public. Access to PLMN services is achieved by means of an
air
interface involving
radio
communications between
mobile
phones or other
wireless
enabled user equipment and land based
radio
transmitters or
radio
base stationsPLMNs interconnect with other PLMNs and
PSTNs for
telephone
communications or with
internet service providers for
data and
internet
access.
Plug and Play Technology - Designed so you don't have to worry about
complicated equipment, messy hook-ups, or extra wires or cords. Just plug in and
play, and open the door to amazing visual displays.
PM - Project Management. A project is a temporary endeavor undertaken
to create a unique product or service. A project is consider temporary
since once the projects objectives are met, the project team will break-up and
go onto other projects. The goal of a project is to create something new, or
unique. All projects have three basic elements: tasks, resources
and time. These are interrelated and any change in one has an effect on the
other two. This is one area where Microsoft Project excels. Whenever you make
any changes, the affect of those changes will become instantly visible through
Microsoft Project's graphical presentation of your project.
PNNI - Private Network Node Interface or Private Network-to-Network Interface
(PNNI) protocol. is used by most ATM networks supporting SPVPs, SPVCs, and SVCs. PNNI uses the same shortest path first algorithm used by
OSPF and IS-IS
to route IP packets to share topology information between switches and select a
route through a network. PNNI also includes a very powerful summarization
mechanism to allow construction of very large networks, as well as a call
admission control (CAC) algorithm that determines whether sufficient bandwidth
is available on a proposed route through a network to satisfy the service
requirements of a Virtual Circuit or Virtual Path.
PoC - Push to Talk over Cellular is
the Motorola and Nokia versions of PTT, and are based on
2.5G packet-switched networks (CDMA by Motorola, GPRS by Nokia) and use SIP and
RTP protocols. The Open Mobile Alliance is defining PoC as part of the IMS (IP
Multimedia System) framework. A pre-standard version of PoC is also defined by
the industry consortium made up of Motorola, Nokia, Ericsson, Siemens AG, AT&T
Wireless, and Cingular Wireless with the aim of
creating a commercial offering enabling inter-operability between vendors.
Also see PTT.
POP - In wireless parlance, the number of wireless POPs refer to the
total population covered by a wireless service operator’s license. ISP POP
is a Point of Presence where subscribers can connect to the internet.
Portlets - Portlets are pluggable user interface components that are managed and displayed
in a portal.
Portlets produce fragments of markup code that are aggregated into a portal
page. Typically, following the
desktop metaphor, a portal page is displayed as a collection of
non-overlapping portlet windows, where each portlet window displays a portlet.
Hence a portlet (or collection of portlets) resembles a web-based application
that is hosted in a portal. Portlet applications include
email,
weather
reports,
discussion forums, and
news. Portlet standards are intended to enable
software developers to create portlets that can be plugged in any portal
supporting the standards. The purpose of the Web
Services for Remote Portlets interface
is to provide a
web
services standard that allows for the "plug-n-play"
of portals, other intermediary
web applications that aggregate
content, and
applications from disparate sources. The Java Portlet Specification (JSR168)
enables
interoperability between portlets and
web portals.
This specification defines a set of
APIs for portal
computing addressing the areas of
aggregation,
personalization,
presentation and
security. Apache Pluto is a reference implementation of JSR168. Other than the reference
implementation, a number of vendors provide commercial implementations of the
portal container. Two of the leading vendors are
IBM and
BEA
Systems. These vendors provide standards based implementations but also
provide extensions not yet approved by the standards body. Furthermore a number
of open-source portal solutions support JSR168 such as Apache's Jetspeed-2
Enterprise Portal and Liferay Portal.
Pot - An electronic component that is used to vary, or control, the
amount of current that flows through an electronic circuit. A
potentiometer is also referred to as a pot.
POTS -
Plain Old Telephone Service, refers to the standard telephone service that most homes use. In contrast,
telephone services based on high-speed, digital communications lines, such as
ISDN and FDDI, are not
POTS. The main distinctions between POTS and non-POTS services are speed and
bandwidth. POTS is generally restricted to about 52 Kbps (52,000 bits per
second). The POTS network is also called the
public switched telephone network (PSTN).
POTS should not be confused with pot, an abbreviation of
potentiometer. POTS services include: full duplex voice path with limited
frequency range (300-3400Hz), Dial Tone and Ringing Signals, Subscriber Dialing,
Operator Services (such as Directory Assistance, Long Distance, and Conference
Calling assistance).
Power Lock - This feature forces the default power setting to the "ON"
position. This means that the power can't be turned off at the front of the set
and that, in the event of a power failure, the television comes back on as soon
as the power does. It also means that users can control the power to multiple
sets from a single circuit breaker.
Power Management - This feature forces the default power to the "ON"
position, preventing the sets from being turned off while being used.
Presence Information -
In computer and telecommunications networks, presence
information conveys a presentity's availability
and willingness to communicate. A client publishes presence information to other
systems' users—sometimes called watchers or subscribers—to convey
its communication state. Presence information has wide application in voice over
IP and instant messaging. A user may publish a variety of presence states to
indicate their communication status. This published state informs others that
wish to contact the user of their availability and willingness to communicate.
The most common use of presence today is the status indicator displayed on most
instant messaging clients. A more simple everyday example is the 'on-hook' or
'off-hook' state of a telephone receiver, resulting in a distinctive ring tone
for caller. Some states that offer extended information on the user's
availability are "free for chat", "away", "do not disturb", and "out to lunch",
which are often seen on many modern instant messaging clients. In fact, users
and communication applications can create arbitrary presence states, since there
is no standardization of state itself. Presence is different from traditional
'on-hook' telephone status in that it deals with the user not the
device. Presence becomes interesting for communication systems when it spans a number of
different communication channels. The idea that multiple communication devices
can combine state, to provide an aggregated view of a user's presence has been
termed Multiple Points of Presence (MPOP). MPOP becomes even more powerful when
it is automatically inferred from passive observation of a user's actions. This
idea is already familiar to instant messaging users who have their status set to
"Away" (or equivalent) if their computer keyboard is inactive for some time.
Extension to other devices could include whether the user's cell phone is on,
whether they are logged into their computer or perhaps checking their electronic
calendar to see if they are in a meeting or on vacation. For example, if a
user's calendar was marked as out of office and their cell phone was on, they
might be considered in a "Roaming" state. MPOP status can then be used to automatically direct incoming messages across
all contributing devices. For example "Out of office" might translate to a
system directing all messages and calls to the user's cell phone. The status "Do
not disturb" might automatically save all messages for later and send all phone
calls to voicemail. Presence, particularly MPOP, requires collaboration between a number of
electronic devices (for example IM client, home phone, cell phone and electronic
calendar). To date, presence has only seen wide scale implementation in closed,
SPOP (Single Point of Presence, where a single device publishes state) systems.
For presence to work in an MPOP environment, multiple devices must be able to
intercommunicate.2.5G and
3G cell phone networks
promise the possibility of users publishing the presence of their cell phone
handsets. In the workplace, private messaging servers offer the possibility of
MPOP within a company or work team.
XMPP allows for MPOP by assigning each client a "resource" (a
specific identifier) and a priority number for each resource. A message directly
to the user's ID would go to the resource with highest priority, although
messaging a specific resource is possible by using the form
user@domain/resource.
Currently there are several
working groups trying to standardize a presence protocol: The
XML-based
XMPP or Extensible Messaging and Presence Protocol was designed and
currently maintained by the
Jabber Software
Foundation. It is the base of the Jabber
IM protocol, which is a
robust and widely extended protocol, it is also the protocol used by
Google
Talk. In October 2004, the XMPP working group at
IETF published the
RFC documents 3920,
3921, 3922 and 3923, to standardize the core XMPP protocol. Another standardization effort is
SIP for Instant Messaging and Presence Leveraging Extensions (SIMPLE).
SIMPLE specifies extensions to the
SIP protocol which
deal with a publish and subscribe mechanism for presence information and sending
instant messages. SIMPLE has an IETF working group, trying to also standardize
this protocol.
Priority Channel - Allows the set to default to a pre-selected channel
when powered on.
Programmable Channel Blanking - Provides a means to force the picture to
be blanked without affecting the audio. Perfect for audio only services, such as
FM-radio.
Programmable Channel Ring - Like the volume management, this feature
offers the user a limited range of flexibility. TV sets can be programmed to
receive only selected channels or inputs, eliminating all others that aren't
programmed.
Pro Plus Performance Package - Upgrades television with stereo dbx(R) sound,
digital comb filter, event programming, 24-hour clock, easy A/V switching and
29-button Universal Remote.
Project Network - A
project network is a graph (flow chart) depicting the sequence in which a
project's terminal elements are to be completed by showing terminal elements and
their dependencies.
PSTN - Public Switched
Telephone Network refers to the international telephone system based on
copper wires carrying analog voice data. This is in contrast to newer telephone
networks base on digital technologies, such as ISDN and FDDI. Telephone
service carried by the PSTN is often called Plain Old Telephone Service (POTS).
PTT - Push to talk is a
method of conversing on half-duplex communication lines, including two-way
radio, by pushing a button in order to send, allowing voice communication to be
transmitted from you, and releasing to let voice communication be received. The term has come to be more commonly known as referring to a feature that is
available on certain more recent mobile phone models. It allows the mobile
phone, when in a special mode, to function as a digital two-way radio in
push-to-talk operation (in a fashion similar to the "trunking" feature of newer
commercial and public-safety two-way radios). Only one person at a time can
talk, by pressing a PTT button, and one or several others can listen instantly.
The service connects mobile phone users with each other within seconds.
Currently, PTT users have to belong to the same mobile operator's (carrier's)
network in order to talk to one another. PTT commonly does not use up the
regular airtime minutes that are available for general voice calls, it uses the
GPRS connection, on which the amount of data transmitted is billed, and not the
minutes of conversation. Nextel Communications introduced mobile push to talk
several years ago using iDEN and is currently the leader in this industry. iDEN
technology is also used by SouthernLinc in the southeastern US, and as well as
several other carriers worldwide. Recently, Verizon Wireless and Sprint PCS in the United
States, Advanced Info Service (AIS) in Thailand,
Telstra in Australia and also Bell Mobility (known
as 10-4 service) (CDMA) and Telus Mobility (known as MIKE) (iDEN) in Canada
launched their push to talk services. And more operators all over the world have
announced intentions to launch similar services. Also see PoC.
BACK TO TOP
Q
QCIF -
A standard related to
CIF, QCIF (Quarter CIF), transfers one fourth the amount of data and is suitable
for videoconferencing systems on slower connections or telephone lines.
QoS -
Quality of Service: In the fields of
packet-switched networks and
computer networking, the
traffic engineering term QoS (pronounced "que-oh-ess")
refers to the
probability of the telecommunication network meeting a given traffic
contract, or in many cases is used informally to refer to the probability of a
packet succeeding in passing between two points in the network. In the field of
telephony,
telephony QoS refers to lack of noise and tones on the
circuit, appropriate loudness levels etc., and includes
grade of service. Isochronous traffic requires fixed real-time continuous
sequential bitrates, and is very sensitive to loss and transmission and
processing delays. Some of the problems affecting the performance of
packet based networks are:
 |
dropped packets - the
routers might fail to deliver (drop) some packets if they arrive when
their buffers are already full. Some, none, or all of the packets might be
dropped, depending on the state of the network, and it is impossible to
determine what happened in advance. The receiving application must ask for
this information to be retransmitted, possibly causing severe delays in the
overall transmission. |
 |
delay - it might take a
long time for a packet to reach its destination, because it gets held up in
long queues, or takes a less direct route to avoid congestion.
Alternatively, it might follow a fast, direct route. Thus delay is very
unpredictable. |
 |
jitter - packets from
source will reach the destination with different delays. This variation in
delay is known as jitter and can seriously affect the quality of streaming
audio and/or video. |
 |
out-of-order delivery -
when a collection of related packets are routed through the Internet,
different packets may take different routes, each resulting in a different
delay. The result is that the packets arrive in a different order to the one
with which they were sent. This problem necessitates special additional
protocols responsible for rearranging out-of-order packets once they reach
their destination. |
 |
error - sometimes
packets are misdirected, or combined together, or corrupted, while en
route. The receiver has to detect this and, just as if the packet was
dropped, ask the sender to repeat itself. |
The following are some of the
application requiring QoS:
 | streaming multimedia may
require guaranteed throughput |
 | IP telephony or Voice over
IP (VoIP) may require strict limits on jitter and delay |
 | Video Teleconferencing
(VTC) requires low jitter |
 | dedicated link emulation
requires both guaranteed throughput and imposes limits on maximum delay and
jitter |
 | a safety-critical
application, such as remote surgery may require a guaranteed level of
availability (this is also called hard QoS). |
These types of service are called
inelastic, meaning that they require a
certain level of bandwidth to function - any more than required is unused, and
any less will render the service non-functioning. By contrast, elastic
applications can take advantage of however much or little bandwidth is
available. Obtaining QoS:
 | Per call |
 | In call |
 | In advance: When the
expense of mechanisms to provide QoS is justified, network customers and
providers typically enter into a contractual agreement termed an (SLA,
Service Level Agreement) which specifies guarantees for the ability of a
network/protocol to give guaranteed performance/throughput/latency bounds
based on mutually agreed measures, usually by prioritizing traffic.
|
 | Reserving resources:
Resources are being reserved at each step on the network for the call as it
is set up. An example is RSVP, Resource Reservation Protocol. |
QoS mechanisms: Quality of Service can be provided by generously over provisioning a network so
that all packets get a quality of service sufficient to support QoS-sensitive
applications. This approach is relatively simple, and is economically feasible
for many broadband networks. The performance is reasonable, particularly if the
user is willing to sometimes accept some degradation. For example, commercial
VOIP services are increasingly replacing traditional telephone service even
though no QoS mechanisms are usually operating between the user's connection to
his ISP and the VOIP provider's connection to a different ISP. For narrowband networks more typical of enterprises and local governments,
however, the costs of bandwidth can be substantial and over provisioning is hard
to justify. In these situations, two distinctly different philosophies were
developed to engineer preferential treatment for packets which require it. Early work used the "IntServ"
philosophy of reserving network resources. In this model, applications used the
Resource Reservation Protocol (RSVP) to request and reserve resources through a
network. While IntServe mechanisms do work, it was realized that in a broadband
network typical of a larger service provider, Core routers would be required to
accept, maintain, and tear down thousands or possibly tens of thousands of
reservations. It was believed that this approach would not scale with the growth
of the Internet, and in any event was antithetical to the notion of designing
networks so that Core routers do little more than simply switch packets at the
highest possible rates. The second and currently accepted approach is "DiffServ"
or differentiated services. In the diffserve model, packets are marked according
to the type of service they need. In response to these markings, routers and
switches use various queuing strategies to tailor performance to requirements.
(At the IP layer, differentiated services code point (DSCP)
markings use the 6 bits in the IP packet header. At the MAC layer,
VLAN IEEE 802.1q
and IEEE 802.1D can be used to carry essentially the same information). Routers supporting diffserve use multiple queues for packets awaiting
transmission from bandwidth constrained (e.g., wide area) interfaces. Router
vendors provide different capabilities for configuring this behavior, to include
the number of queues supported, the relative priorities of queues, and bandwidth
reserved for each queue. In practice, when a packet must be forwarded from an interface with
queuing,
packets requiring low jitter (e.g., VOIP or VTC) are given priority over packets
in other queues. Typically, some bandwidth is allocated by default to network
control packets (e.g., ICMP and routing protocols), while best effort traffic
might simply be given whatever bandwidth is left over. Additional mechanisms may be used to further engineer performance, to include:
 | queuing
 | fair-queuing
|
 | first in first out
(FIFO) |
 | weighted round robin,
WRR |
 | class based weighted
fair queuing |
 | weighted fair queuing
|
|
 | buffer tuning |
 | congestion avoidance
 | RED, WRED - Lessens
the possibility of port queue buffer tail-drops and this lowers the
likelihood of TCP global synchronization |
|
 | policing and Traffic
shaping |
As mentioned, while diffserv is
used in many sophisticated enterprise networks, it has not been widely deployed
in the Internet. Internet peering arrangements are already complex, and there
appears to be no enthusiasm among providers for supporting QoS across peering
connections, or agreement about what policies should be supported in order to do
so. QoS skeptics further point out that if you are dropping many packets on elastic
low-QoS connections, you are already dangerously close to the point of
congestion collapse on your inelastic high-QoS applications, without any way
of further dropping traffic without violating traffic contracts. In
addition to the local governmental rules and regulations, the following criteria
need to be addressed in a QoS network design: service security and service
Performance/Cost ratio.
Quantization -
In the MPEG
compression sequence, this step follows the Discrete Cosine Transform (DCT) and
reduces the high-frequency components, leaving a softer picture but offering
greater compression. It uses fewer bits offering greater compression. It uses
fewer bits to describe the same overall quantity of information but with larger
quantum steps. JPEG and MPEG use uniform quantization, in which all the
Quantization steps are of the same size.
QuickTime -
A file-format and
architecture developed by Apple for use with digital audio and video. Available
on most computing platforms. A future version (Quicktime3) will support
streaming.
BACK TO TOP
R
RealAudio -
A proprietary system
for streaming audio (and now video) over the internet. Before Real Audio, users
had to download an entire audio file before they could listen to it. Also
supports real-time broadcast of audio and video programs. Many radio stations
now broadcast on the internet using Real Audio.
Real time -
A transmission that
occurs right away, without any perceptible delay. Very important in video
conferencing, as much delay will make the system very unusable. Occurring immediately. The term is
used to describe a number of different computer features. For example, real-time
operating systems are systems that respond to input immediately. They are used
for such tasks as navigation, in which the computer must react to a steady flow
of new information without interruption. Most general-purpose operating systems
are not real-time because they can take a few seconds, or even minutes, to
react. Real time can also refer to events simulated by a computer
at the same speed that they would occur in real life. In graphics animation, for
example, a real-time program would display objects moving across the screen at
the same speed that they would actually move.
Remote Cloning -
Settings for televisions in the system can be cloned and duplicated throughout
the network, all from the head-end computer control. Any television’s settings
including picture settings and institutional settings (auto power-on,
minimum/maximum volume, etc.) can be downloaded as a "template", and then
uploaded ("cloned") to other televisions throughout the network eliminating the
need to configure each television individually at its physical location.
Replay Attack -
A replay attack is a form of
network attack in which a valid data transmission is maliciously or
fraudulently repeated or delayed. This is carried out either by the originator
or by an
adversary who intercepts the data and retransmits it, possibly as part of a
masquerade attack. Suppose
Alice wants to prove her identity to Bob. Bob requests her password as proof
of identity, which Alice dutifully provides (possibly after some transformation
like a
hash
function); meanwhile, Mallory is eavesdropping the conversation and keeps
the password. After the interchange is over, Mallory connects to Bob posing as
Alice; when asked for a proof of identity, Mallory sends Alice's password read
from the last session, which Bob must accept. A way to avoid replay attacks is using
session tokens: Bob sends a one-time token to Alice, which Alice uses to
transform the password and send the result to Bob (e.g. computing a hash
function of the session token appended to the password). On his side Bob
performs the same computation; if and only if both values match, the login is
successful. Now suppose Mallory has captured this value and tries to use it on
another session; Bob sends a different session token, and when Mallory replies
with the captured value it will be different than Bob's computation. Session tokens should be chosen by a (pseudo-)
random process.
Otherwise Mallory may be able to guess some future token and convince Alice to
use that token in her transformation. Mallory can then replay her reply at a
later time, which Bob will accept. Bob can also send
nonce but should then include a
Message authentication code (MAC), which Alice should check. Timestamping is another way of preventing a replay attack.
Synchronization should be achieved using a secure protocol. For example Bob
periodically broadcasts the time on his clock together with a MAC. When Alice
wants to send Bob a message, she includes her best estimate of the time on his
clock in her message, which is also authenticated. Bob only accepts messages for
which the timestamp is within a reasonable tolerance. The advantage of this
scheme is that Bob does not need to generate (pseudo-) random numbers.
Resolution -
The number of
pixels per unit of area. The greater the number of pixels, the higher the
resolution.
Resource -
In project management terminology,
resources are required to carry out
the project tasks. They can be people, equipment, facilities, funding, or
anything else capable of definition (usually other than labor) required for the
completion of a project activity. The lack of a resource will therefore be a
constraint on the completion of the project activity. Resources may be storable
or non storable. Storable resources remain available unless depleted by usage,
and may be replenished by project tasks which produce them. Non-storable
resources must be renewed for each time period, even if not utilized in previous
time periods. Resource scheduling, availability and optimization are considered key to
successful project management.
RGB (red-Green-Blue) -
A computer color display that provides a separate output of red,
green, and blue
signals, each of which can be controlled. Typically, an RGB monitor offers a
higher resolution than a composite monitor, in which the RGB signals are
combined before output.
RIP -
The Routing Information Protocol
is one of the most commonly used Interior Gateway Protocol (IGP) routing
protocols on internal networks (and to a lesser extent, networks connected to
the Internet), which helps routers dynamically adapt to changes of network
connections by communicating information about which networks each router can
reach and how far away those networks are. Although RIP is still actively
used, it is generally considered to have been made obsolete by routing protocols
such as OSPF and IS-IS. Nonetheless, a somewhat more capable protocol in the
same basic family (distance-vector routing protocols), EIGRP, also sees some
use.
Routing -
In
computer networking the term routing refers to selecting paths in a
computer network along which to send data. Routing directs
forwarding,
the passing of logically addressed packets from their source toward their
ultimate destination through intermediary
nodes (called
routers). The
routing process usually directs forwarding on the basis of
routing tables within the routers, which maintain a record of the best
routes to various network destinations. Thus the construction of routing tables
becomes very important for efficient routing. Routing differs from
bridging in its assumption that address-structures imply the proximity of
similar addresses within the network, thus allowing a single routing-table entry
to represent the route to a group of addresses. Therefore, routing outperforms
bridging in large networks, and it has become the dominant form of
path-discovery on the
Internet. Small networks may involve hand-configured routing tables. Large networks
involve complex
topologies and may change constantly, making the manual construction of
routing tables very problematic. Nevertheless, most of the
public switched telephone network (PSTN) uses pre-computed routing tables,
with fallback routes if the most direct route becomes blocked. Dynamic routing attempts to solve this problem
by constructing routing tables automatically, based on information carried by
routing protocols, and allowing the network to act nearly autonomously in
avoiding network failures and blockages. Dynamic routing dominates the Internet. However, the configuration of the
routing protocols often requires a skilled touch; one should not suppose that
networking technology has developed to the point of the complete automation of
routing.
Packet-switched networks, such as the
Internet,
split data up into
packets, each labeled with the complete destination address and each routed
individually.
Circuit switched networks, such as the
voice telephone network,
also perform routing, in order to find paths for
circuits (such as
telephone calls) over which they can send large amounts of data without
continually repeating the complete destination address. The hardware used in routing includes
hubs,
switches, and
routers. Dynamic routing uses one of two broad classes of routing
algorithms, Distance vector algorithms and Link-state algorithms. Distance
vector algorithms use the Bellman-Ford algorithm. This approach assigns a
number, the cost, to each of the links between each node in the network.
Nodes will send information from point A to point B via the path that results in
the lowest total cost (i.e. the sum of the costs of the links between the
nodes used). The algorithm operates in a very simple manner. When a node first starts, it
only knows of its immediate neighbors, and the direct cost involved in reaching
them. (This information, the list of destinations, the total cost to each, and
the next hop to send data to get there, makes up the
routing table, or distance table.) Each node, on a regular basis,
sends to each neighbor its own current idea of the total cost to get to all the
destinations it knows of. The neighboring node(s) examine this information, and
compare it to what they already 'know'; anything which represents an improvement
on what they already have, they insert in their own routing table(s). Over time,
all the nodes in the network will discover the best next hop for all
destinations, and the best total cost. When one of the nodes involved goes down, those nodes which used it as their
next hop for certain destinations discard those entries, and create new
routing-table information. They then pass this information to all adjacent
nodes, which then repeat the process. Eventually all the nodes in the network
receive the updated information, and will then discover new paths to all the
destinations which they can still "reach". Link-state
Algorithms: When applying link-state algorithms, each node uses its
fundamental data a map of the network in the form of a graph. To produce this,
each node floods the entire network with information about what other nodes it
can connect to, and each node then independently assembles this information into
a map. Using this map, each router then independently determines the best route
from itself to every other node. The algorithm used to do this, Dijkstra's algorithm, does this by building
another data structure, a tree, with the current node itself as the root, and
containing every other node in the network. It starts with a tree containing
only itself. Then, one at a time, from the set of nodes which it has not yet
added to the tree, it adds the node which has the lowest cost to reach an
adjacent node which already appears in the tree. This continues until every node
appears in the tree. This tree then serves to construct the routing table, giving the best next hop,
etc, to get from the node itself to any other node in the network. A routing metric consists of any value used by routing algorithms to
determine whether one route should perform better than another. Metrics can
cover such information as bandwidth, delay, hop count, path cost,
load, MTU,
reliability, and communication cost. The routing table stores only the best
possible routes, while link-state or topological databases may store all other
information as well.
RPC -
A remote procedure call (RPC) is a
protocol that allows a computer program running on one computer to cause a
subroutine on another computer to be executed without the programmer explicitly
coding the details for this interaction. When the software in question is
written using object-oriented principles, RPC may be referred to as remote
invocation or remote method invocation.
RPC is an easy and popular
paradigm for implementing the
client-server model of
distributed computing. An RPC is initiated by the caller (client) sending a
request message to a remote system (the server) to execute a certain procedure
using arguments supplied. A result message is returned to the caller.
RTDBMS -
In a Real-Time DataBase Management
System (RTDBMS), transactions must not only maintain the consistency constraints
of the database but also satisfy their timing constraints. In addition, a RTDBMS
often involves processing both temporal and persistent data. A RTDBMS is
appropriate for applications such as air traffic control, stock trading,
telecommunications, flexible manufacturing and aircraft flight programs. Its
main goal is to meet the timing constraints of data transactions regardless of
system or transaction failures. Our research in this area aims at the
development of techniques to manage concurrency control, nested transactions,
real-time promising, and recovery.
RTOS -
A Real-Time Operating
System is a class of
operating system intended for
real-time applications. Examples include
embedded applications (programmable thermostats, household appliance
controllers,
mobile telephones), industrial
robots,
industrial control (see
SCADA), and
scientific research equipment. A RTOS facilitates the creation of a real-time system, but does not guarantee
the finished product will be real-time; this requires correct development of the
software. A RTOS does not necessarily have high throughput; rather, a RTOS
provides facilities which, if used properly, guarantee that system deadlines can
be met generally ("soft
real-time") or deterministically ("hard
real-time"). A RTOS will typically use specialized scheduling algorithms in
order to provide the real-time developer with the tools necessary to produce
deterministic behavior in the final system. A RTOS is valued more for how
quickly and/or predictably it can respond to a particular event than for the
given amount of work it can perform over time. Key factors in an RTOS are
therefore minimal
interrupt
and thread switching
latency. An early example of a large-scale real-time operating system was the so-called
"control program" developed by
American Airlines and
IBM for the
Sabre Airline Reservations System. Debate exists about what actually constitutes
real-time computing. There are two basic designs: 1-) An event-driven
operating system only changes tasks when an event requires service. 2-) A
time-sharing design switches tasks on a clock interrupt, as well as on events.
The time-sharing design switches tasks more often than is strictly necessary,
but gives "smoother", more deterministic
multitasking, the illusion that a user has sole use of a machine.
RTP -
The Real-time Transport Protocol
defines a standardized packet format for delivering audio and video over the
Internet. It was developed by the Audio-Video Transport Working Group of the
IETF and first published in 1996 as RFC 1889.
It is frequently used in streaming
media systems in conjunction with RTCP as well as videoconferencing and push to
talk systems (in conjunction with H.323 or SIP), making it the technical
foundation of the Voice over IP industry. It goes along with the RTCP and it's
built on top of User Datagram Protocol.
RTCP -
RTP Control Protocol
is a sister protocol of the Real-time Transport Protocol (RTP). It is defined in
RFC 3550 (which obsoletes RFC
1889). RTCP stands for Real-time Transport Control Protocol, provides
out-of-band control information for an RTP flow. It partners RTP in the delivery
and packaging of multimedia data, but does not transport any data itself. It is
used periodically to transmit control packets to participants in a streaming
multimedia session. The primary function of RTCP is to provide feedback on the
quality of service being provided by RTP. RTCP is used for QoS reporting.
RUP - The Rational
Unified Process is an
iterative
software development process created by the
Rational Software Corporation, now a division of
IBM. The RUP is not a
single concrete prescriptive process, but rather an adaptable process
framework.
As such, RUP describes how to develop software effectively using proven
techniques. While the RUP encompasses a large number of different activities, it
is also intended to be tailored, in the sense of selecting the development
processes appropriate to a particular software project or development
organization. The RUP is recognized as particularly applicable to larger
software development teams working on large projects. Rational Software offers a
product (known below as the Rational Unified Process Product) that provides
tools and technology for customizing and executing the process. The static 4:
1-) Roles are who – a role is the behavior and responsibilities of a person or
team, not the person themselves. 2-) Artifacts are what – they are the outcome
of activities, including all the documents and models produced while working
through the process. 3-) Workflow is when – it is a sequence of activities or
the design of processes that must be completed. 4-) Activity is how – it is the
actual tasks a worker performs.
This side of the process is called static because it describes how things are
done. It is not dependent on the project at hand. For example, the description
of the tasks and deliverables of a use-case designer is the same for each
project.
BACK TO TOP
S
SAP -
Standard Accounting Program,
similar in scope and usage to ERP. SAP, started in 1972 by five former IBM
employees in Mannheim, Germany, states that it is the world's largest
inter-enterprise software company and the world's fourth-largest independent
software supplier, overall. The original SAP idea was to provide customers with
the ability to interact with a common corporate database for a comprehensive
range of applications. Gradually, the applications have been assembled and today
many corporations, including IBM and Microsoft, are using SAP products to run
their own businesses.
SAP applications, built around
their latest R/3 system, provide the capability to manage financial, asset, and
cost accounting, production operations and materials, personnel, plants, and
archived documents. The R/3 system runs on a number of platforms including
Windows 2000 and uses the client/server model. The latest version of R/3
includes a comprehensive Internet-enabled package. SAP has recently recast
its product offerings under a comprehensive Web interface, called mySAP.com, and
added new e-business applications, including Customer Relationship Management
(CRM) and Supply Chain Management (SCM). In early 2001, SAP, a publicly
traded company, had 21,500 employees in over 50 countries, and more than 30,000
installations. SAP is turning its attention to small- and-medium sized
businesses. A recent R/3 version was provided for IBM's AS/400 platform
SBC
- A Session Border Controller is a device used in some
VoIP networks. SBCs
are put into the signaling and media path between calling and called party. The
SBC acts as if it was the called VoIP phone and places a second call to the
called party. The effect of this behavior is that not only the signaling
traffic, but also the media traffic (voice, video etc) crosses the SBC. Without
an SBC, the media traffic travels directly between the VoIP phones. Private SBCs
are used along with
firewalls to enable VoIP calls to and from a protected enterprise network.
Public VoIP service providers use SBCs to allow the use of VoIP protocols from
private networks with
internet
connections using NAT. Additionally, some SBCs can also allow VoIP calls
to be set up between two phones using different VoIP signaling protocols ( SIP,
H.323, Megaco/MGCP, etc...) as well as performing transcoding of the media
stream when different codecs are in use. Many SBCs also provide firewall
features for VoIP traffic (denial of service protection, call filtering,
bandwidth management, etc...). In contrast to conventional phone systems,
the OSI layers of a VoIP-based network need not to be operated by a single
company. A VoIP user may purchase her internet access from one internet service
provider and her VoIP service from a second company. Some telecom companies use
SBCs to revert this characteristic in order to retain their current business
model when offering public VoIP services. The concept of the SBC is
controversial to proponents of end-to-end systems and peer-to-peer networking.
 |
SBCs can extend the length of
the media path (the way of media packets through the network) significantly.
A long media path is undesirable, as it increases the delay of voice packets
(especially if the SBC implements transcoding) and the probability of packet
loss. Both effects deteriorate the voice/video quality. Some SBCs can detect
if the ends of the call are in the same subnetwork and release control of
the media enabling it to flow directly between the clients, this is
anti-tromboning. |
 |
SBCs break the end-to-end
transparency. VoIP phones can't use new protocol features unless they are
understood by the SBC. End-to-End encryption can't be used if the SBC does
not have the key. |
 |
Far-end or hosted NAT
traversal can be done without SBCs if the VoIP phones support protocols like
STUN, TURN, ICE, or Universal Plug and Play (UPnP). |
An SBC may provide session media (normally
Real-time Transport Protocol) and signaling (normally
SIP) wiretap
services, which can be used by providers to enforce requests for the
lawful interception of network sessions. Standards for the interception of
such services are provided by
CALEA and ETSI,
among others.
Schedule -
A schedule is a list of
employees
who are
working on any given day, week, or month in a
workplace.
A schedule is necessary for the day-to-day operation of any
retail store
or
manufacturing facility. The process of creating a schedule is called
scheduling. An effective workplace schedule balances the needs of employees,
tasks, and in some
cases,
customers. A daily schedule is usually ordered
chronologically, which means the first employees working that day are listed
at the top, followed by the employee who comes in next, et cetera. A weekly or monthly schedule is usually ordered
alphabetically, employees being listed on the left hand side of a grid, with
the days of the week on the top of the grid. A schedule is most often created by a
manager. In
larger operations, a
Human Resources manager or
specialist
may be solely dedicated to writing the schedule. A schedule by this definition is sometimes referred to as
workflow.
In project management, a schedule consists of a list of a project's
terminal elements with intended start and finish dates. A Gantt chart can
provide a graphical representation of a project schedule. Critical chain
project management warns that terminal-element start dates and finish dates
function as random variables, and suggests managing a project not by its
traditional schedule but rather by using buffer management and a relay race
mentality.
SCM -
Software Configuration
Management is part of configuration management (CM). Roger Pressman, in his
book, Software Engineering: A Practitioner's Approach, says that software
configuration management (SCM) is a "set of activities designed to control
change by identifying the work products that are likely to change, establishing
relationships among them, defining mechanisms for managing different versions of
these work products, controlling the changes imposed, and auditing and reporting
on the changes made." In other words, SCM is a methodology to control and
manage a software development project.
SCM -
Supply chain management (SCM)
deals with the planning and execution issues involved in managing a supply
chain. The components of SCM are:
 | Demand planning
(forecasting) |
 | Demand collaboration
(collaborative resolution process to determine consensus forecasts)
|
 | Order promising (When one
can promise a product to a customer taking into account lead times and
constraints) |
 | Strategic network
optimization (what plants and DC's should serve what markets for what
products) (monthly - yearly) |
 | Production and
distribution planning (Coordinate the actual production and distribution
plans for a whole enterprise) (daily) |
 | Production scheduling (For
a single location create a feasible production schedule) (minute by minute)
|
 | Transportation planning
(For multiple supply, manufacturer, distributor and warehousing points in a
network) |
 | Transportation execution
(Enactment of long term plans on a per shipment basis, typically performed
by focused organizations called forwarders) |
 | Tracking and Measuring (An
ever increasing aspect of supply chain management designed to highlight
potential against the plan and possible process improvements) |
 | Plan of reduction of costs
and management of the performance (diagnosis of the potential and the
indicators, the organization and planifiaction strategic, masters
dysfunctions in real time, evaluation and accounting reporting, evaluation
and reporting quality) |
The SupplyChainDigest web site is very informative
http://www.scdigest.com
SCTP - The Stream Control Transmission Protocol is a
transport layer
protocol defined in
2000 by the IETF
Signaling Transport (SIGTRAN)
working group. The protocol is defined in
RFC 2960, and an
introductory text is provided by
RFC 3286. As a transport protocol, SCTP is equivalent in a sense to
TCP or
UDP. Indeed it provides some similar services as TCP — ensuring reliable,
in-sequence transport of messages with congestion control. (In the absence of
native SCTP support, it may sometimes be desirable to
tunnel SCTP over UDP.
SCTP was originally intended for the transport of telephony (SS7) protocols over
IP, with the goal of
duplicating some of the reliability attributes of the SS7 signaling network in
IP. This IETF effort is known as SIGTRAN. In the meantime, other uses have been
proposed, for example the DIAMETER protocol and Reliable server pooling (RSerPool).
One of the key differences between TCP & SCTP is that TCP transports a
byte-stream while SCTP is capable of transporting multiple message-streams. All
bytes sent in a TCP connection must be delivered in that order, which requires
that a byte transmitted first must safely arrive at the destination before a
second byte can be processed even if the second byte manages to arrive first. If
an arbitrary number of bytes are sent in one step and later some more bytes are
sent, these bytes will be received in order, but the receiver can not
distinguish which bytes were sent in which step. SCTP in contrast, conserves
message boundaries by operating on whole messages instead of single bytes. That
means if one message of several related bytes of information is sent in one
step, exactly that message is received in one step. Multi-streaming refers to the capability of SCTP to transmit several independent
streams of messages in parallel. For example, transmitting two images in a HTTP
application in parallel over the same SCTP association. You might think of
multi-streaming as bundling several TCP-connections in one SCTP-association
operating with messages instead of bytes. TCP ensures the correct order of bytes in the stream by conceptually assigning a
sequence number to each byte sent and ordering these bytes based on that
sequence number when they arrive. SCTP, instead, assigns different sequence
numbers on messages sent in a stream. This allows messages in different streams
to be ordered independently. However, message ordering is optional in SCTP. If
the user application so desires, messages will be processed in the order they
are received instead of the order they were sent, should these differ. Message-based delivery is one of the requirements for
PSTN signaling.
Multi-Streaming also is an advantage when used to transport Public Switched
Telephone Networks Services. If an SCTP connection is set up to carry, say, ten
phone calls with one call per stream, then if a single message is lost in only
one phone call, the other nine calls will not be affected. To handle ten phone
calls in TCP, some form of multiplexing would be required to put all ten phone
calls into a single byte-stream. If a single packet for phone call #3 is lost
then all packets after that could not be processed until the missing bytes are
retransmitted, thus causing unnecessary delays in the other calls.
SDET
- A Software
Design Engineer in Test is a developer who designs, develops,
and maintains automation systems and often expandable suites containing multiple
automation programs to be used by the development and test teams. They are
responsible for utilizing innovative test technologies to develop a product's
testing strategy, and for facilitating the creation and execution of automated
test suites across a diverse set of technologies. They look at source code for
potential problems using Microsoft internal tools. They also reproduce, debug
and isolate problems, and verify fixes.
SDLC - Systems
Development Life Cycle, is defined by the United States Department of Justice as
a software development process, although it is also a distinct process
independent of software or other Information Technology considerations. It is
used by a systems analyst to develop an information system, including
requirements, validation, training, and user ownership through investigation,
analysis, design, implementation, and maintenance. SDLC is also known as
information systems development or application development. An SDLC should
result in a high quality system that meets or exceeds customer expectations,
within time and cost estimates, works effectively and efficiently in the current
and planned information technology infrastructure, and is cheap to maintain and
cost-effective to enhance. SDLC is a systems approach to problem solving and is
made up of several phases, each comprised of multiple steps: The software concept - identifies and defines a need for the new system A
requirements analysis - analyzes the information needs of the end users The
architectural design - creates a blueprint for the design with the necessary
specifications for the hardware, software, people and data resources Coding and
debugging - creates and programs the final system System testing - evaluates the system's actual functionality in relation to
expected or intended functionality. The six official phases are: 1-) Preliminary
Investigation / Feasibility Study, 2-) Systems Analysis / Systems Requirements,
3-) Systems Design / Design Specifications, 4-) Systems Development, 5-) Systems
Implementation, 6-) Systems Maintenance.
SDTV - Standard definition television is
a digital television (DTV) format that provides a picture quality similar to
digital versatile disk (DVD). SDTV and high definition television (HDTV) are the
two categories of display formats for digital television (DTV) transmissions,
which are becoming the standard. Because a compressed SDTV digital signal is
smaller than a compressed HDTV signal, broadcasters can transmit up to five SDTV
programs simultaneously instead of just one HDTV program. This is
multicasting. Multicasting is an attractive feature because television
stations can receive additional revenue from the additional advertising these
extra programs provide. With today's analog television system, only one program
at a time can be transmitted.
SDI -
Serial Digital Interface.
SDL -
Specification and Description Language. SDL is a low level design language
using flowcharts and text. SDL is an International Telecommunications
Union standard used to create object-oriented flowcharts that document the low
level design of, and not limited to, communications and telecommunications
systems networks. SDL files can be used to generate source code as per
specifications.
SECAM
(Sequential
Couleur Avec Memoire)
- A
color television format developed and used in France. SECAM video is
characterizes by 625 scan lines and 25 frames per second.
Self similar -
A self-similar object is exactly or approximately
similar to a
part of itself. A
curve is said to be self-similar if, for every piece of the curve, there is
a smaller piece that is
similar to
it. For instance, a side of the
Koch snowflake is self-similar; it can be divided into two halves, each of
which is similar to the whole. Many objects in the real world, such as
coastlines,
are statistically self-similar: parts of them show the same statistical
properties at many scales. Self-similarity is a typical property of
fractals. It also has important consequences for the design of computer networks, as
typical network traffic has self-similar properties. For example, in
telecommunications traffic engineering,
packet switched data traffic patterns seem to be statistically self-similar.
This property means that simple models using a
Poisson distribution are inaccurate, and networks designed without taking
self-similarity into account are likely to function in unexpected ways.
Scan Doubling - The process
of eliminating the visible video scan lines by doubling them and filling in the
"blank" lines.
Security Mountable -
Institutional Televisions are equipped with heavy-duty mounting blocks on the
bottom of the cabinet for simple, secure mounting to ceiling, wall, or furniture
brackets.
SIGTRAN -
SIGTRAN is the name given to an IETF working group that produced
specifications for a family of protocols that provide reliable datagram service
and user layer adaptations for SS7 and ISDN communications protocols. The most
significant protocol defined by the SIGTRAN group was the Stream Control
Transmission Protocol (SCTP), which is used to carry PSTN signaling over IP. The SIGTRAN group was significantly influenced by
telecommunications engineers intent on using the new protocols for adapting
VoIP networks to
the PSTN with
special regard to signaling applications. Recently, SCTP is finding applications
beyond its original purpose wherever reliable datagram service is desired.
SIP - Session Initiation
Protocol is a
protocol developed by the IETF
MMUSIC Working Group and
proposed standard for initiating, modifying, and terminating an interactive user
session that involves multimedia elements such as video, voice, instant
messaging, online games, and virtual reality. In November 2000, SIP was accepted
as a 3GPP signaling protocol and permanent element of the IMS architecture. It
is one of the leading signaling protocols for Voice over IP, along with H.323. SIP clients traditionally use
TCP and
UDP port 5060 to connect to SIP servers and other SIP endpoints. SIP is
primarily used in setting up and tearing down voice or video calls. However, it
can be used in any application where session initiation is a requirement. These
include, Event Subscription and Notification, Terminal mobility and so on. There
are a large number of SIP-related RFCs that define behavior for such
applications. All voice/video communications are done over
RTP. A motivating goal for SIP was to provide a signaling and call setup protocol for
IP-based communications
that can support a superset of the call processing functions and features
present in the PSTN.
The SIP Protocol by itself does not define these features, rather, its focus is
call-setup and signaling. However, it has been designed to enable the building
of such features in network elements known as Proxy Servers and User Agents. As
such these are features that permit familiar telephone-like operations: dialing
a number, causing a phone to ring, hearing ringback tones or a busy signal.
Implementation and terminology are different in the SIP world but to the
end-user, the behavior is similar. SIP enabled telephony networks can also implement many of the more advanced call
processing features present in
SS7. SIP works in concert with several other protocols and is only involved in the
signaling portion of a communication session. SIP acts as a carrier for the
Session Description Protocol (SDP), which describes the media content of the
session, e.g. what
IP ports to use, the
codec being used etc. In typical use, SIP "sessions" are simply packet
streams of the Real-time Transport Protocol (RTP).
RTP is the carrier for the actual voice or video content itself.
Siren14 -
Polycom’s patented Siren14 algorithm offers breakthrough benefits compared to
earlier wideband audio technology. Siren14 delivers low-latency 14 kHz
super-wideband audio at nearly half the bit rate of the alternative MPEG4 AAC-LD
codec, while requiring one-tenth to one-twentieth of the computing power.
Six Sigma - stands for Six
Standard Deviations (Sigma is the Greek letter used to represent standard
deviation in statistics) from mean. Six Sigma methodology provides the
techniques and tools to improve the capability and reduce the defects in any
process. It was started in Motorola, in its manufacturing division, where
millions of parts are made using the same process repeatedly. Eventually Six
Sigma evolved and applied to other non manufacturing processes. Today you can
apply Six Sigma to many fields such as Services, Medical and Insurance
Procedures, Call Centers. Six Sigma methodology improves any existing
business process by constantly reviewing and re-tuning the process. To achieve
this, Six Sigma uses a methodology known as DMAIC
(Define opportunities, Measure
performance, Analyze opportunity, Improve
performance, Control performance). Six Sigma methodology
can also be used to create a brand new business process from ground up using
DFSS (Design For Six Sigma) principles. Six Sigma Strives for
perfection. It allows for only 3.4 defects per million opportunities for
each product or service transaction. Six Sigma relies heavily on statistical
techniques to reduce defects and measure quality. Six Sigma experts (Green Belts
and Black Belts) evaluate a business process and determine ways to improve upon
the existing process. Six Sigma experts can also design a brand new business
process using DFSS (Design For Six Sigma) principles. Typically
its easier to define a new process with DFSS principles than refining an
existing process to reduce the defects. Six Sigma incorporates the basic
principles and techniques used in Business, Statistics, and Engineering. These
three form the core elements of Six Sigma. Six Sigma improves the process
performance, decreases variation and maintains consistent quality
of the process output. This leads to defect reduction and improvement in
profits, product quality and customer satisfaction.
Six Sigma methodology is also used
in many Business Process Management initiatives these days. These Business
Process Management initiatives are not necessarily related to manufacturing.
Many of the BPM's that use Six Sigma in today's world include call centers,
customer support, supply chain management and project management.
SKU - Stock Keeping Unit.
SLA - Service Level
Agreement. SLA is a
formal written agreement made between two parties: the service provider and the
service recipient. The SLA itself defines the basis of understanding between the
two parties for delivery of the service itself. The document can be quite
complex, and sometimes underpins a formal contract. The contents will vary
according to the nature of the service itself, but usually includes a number of
core elements, or clauses. Generally, an SLA should contain clauses that
define a specified level of service, support options, incentive awards for
service levels exceeded and/or penalty provisions for services not provided.
Before having such agreements with customers the IT services need to have a good
quality of these services, Quality management will try to improve the QoS,
whereas the SLAs will try to keep the quality and guarantee the quality to the
customer.
SmartCard TelevisionTM
- This patented technology has already become an industry standard featuring an
integrated expansion slot on the back of each SmartCard TelevisionTM
where a SmartCard module can easily be inserted, upgrading the capabilities to
fulfill virtually any professional application.
Smart Loader Clone
Programming Device: RL5180CK (normally not included) - Used to clone
program multiple sets, simply plug the Smart Loader into the addressable
interface port and follow simple onscreen menus to download programming
settings. Smart Loader is then used to upload the information into additional
sets.
SmartMuteTM -
Automatically displays Closed Caption service whenever the user activates the
Mute function.
Smart PlugTM
Two-Way Addressable Port - Hospitality Televisions feature the unique Smart
PlugTM on the back which allows for simple, two-way communication
between the set and a remote source, such as a computer or a rack of equipment
with a VCR, DVD player, etc.
SmartSoundTM
- Maintains constant volume levels when changing channels or programs,
automatically pulling high-level sound down by 6dB and raising low-level sound
by 3dB.
SMS - Short Messaging
Service (SMS) is available on many 2G and all 3G wireless networks. With SMS,
subscribers can send short text messages (usually about 160 characters) to and
from wireless handsets. Enhancements are made to support rich text and graphics.
SOAP -
SOAP is a protocol for exchanging
XML-based messages over a computer network, normally using HTTP and also SMTP. SOAP forms the
foundation layer of the web services stack, providing a basic messaging
framework that more abstract layers can build on. SOAP can be used to facilitate
a Service-Oriented architectural pattern. There are several different
types of messaging patterns in SOAP, but by far the most common is the Remote
Procedure Call (RPC) pattern, where one network node (the client) sends a
request message to another node (the server), and the server immediately
sends a response message to the client. Indeed, SOAP is the successor of XML
RPC.
SONET - see Synchronous
Optical Networking.
Special Setup Remote
Transmitter: RG4172BK (normally not included) - Used during initial setup of
televisions, the setup remote allows access to critical TV functions such as
power, channel up/down, volume, color, tint, brightness, sharpness, etc. Once
setup is complete, the setup transmitter is retained in a secure location.
Spill-Resistant Cabinet
- Reduces the risk of damage to the television in the event liquid is spilled on
the cabinet.
Spoofing Attack - in
computer security terms, refers to a situation in which one person or program is
able to masquerade successfully as another. An example from cryptography is
the man in the middle attack, in which an attacker spoofs Kristen into believing
he's Frank, and spoofs Frank into believing he's Kristen, thus gaining access to
all messages in both directions without the trouble of any cryptanalytic effort.
The attacker must
monitor the packets sent from Kristen to Frank and then guess the sequence
number of the packets. Then the attacker knocks out Kristen with a SYN attack and injects his own packets, claiming to have
the address of Kristen. Kristen's firewall can defend against spoof attacks when
it has been configured with knowledge of all the IP addresses connected to each
of its interfaces. It can then detect a spoofed packet if it arrives from an
interface that is not known to be connected to that interface. Many
carelessly designed protocols are subject to spoof attacks, including many of
those used on the Internet.
Another kind of spoofing is "web page spoofing,"
also known as phishing.
In this attack, a web page is reproduced in "look and feel" to another server
but is owned and operated by someone else. It is intended to fool someone into
thinking that they are connected to a trusted site. Typically, a bank's log-in
page might be spoofed by a crook. The crook then harvests the user names and
passwords. This attack is often performed with the aid of DNS cache poisoning in
order to direct the user away from the legitimate site and into the false one.
Once the user puts in their password, the attack-code reports a password error,
then redirects the user back to the legitimate site.
Referrer Spoofing:
Some websites, especially
pornographic paysites, allow access to their materials only from certain
approved (login-) pages. This is enforced by checking the Referrer header of the
HTTP request. This referrer header however can be changed (known as "Referrer
spoofing" or "Ref-tar spoofing"), allowing users to gain unauthorized access to
the materials.
"Spoofing" can also
refer to copyright holders placing distorted or un-listenable versions of works
on file-sharing networks, to discourage downloading from these sources. An
example of this is the spoof of Madonna's album
American Life.
Spyware -
In the field of
computing,
the term spyware refers to a broad category of
malicious
software designed to intercept or take partial control of a
computer's
operation without the
informed consent of that machine's owner or legitimate user. While the term
taken literally suggests software that surreptitiously monitors the user, it has
come to refer more broadly to software that subverts the computer's operation
for the benefit of a third party. Spyware differs from
viruses and
worms
in that it does not usually self-replicate. Like
many recent viruses, however, spyware – by design – exploits infected
computers for commercial gain. Typical tactics furthering this goal include
delivery of unsolicited
pop-up advertisements; theft of personal information (including financial
information such as
credit card numbers); monitoring of Web-browsing activity for
marketing
purposes; or routing of
HTTP requests to advertising sites. As of 2005, spyware
has become one of the pre-eminent security threats to computer-systems running
Microsoft Windows
operating-systems (and especially to users of
Internet Explorer because of that browser's collaboration with the Windows
operating system). Some malware on the
Linux and
Mac OS X
platforms has behavior similar to Windows spyware, but to date has not become
anywhere near as widespread due to their comparatively smaller user base.
SRTP -
Secure Real-time Transport
Protocol defines a profile of RTP, intended to provide encryption, message
authentication and integrity, and replay protection to the RTP data in both
unicast and multicast applications. It was developed by David Oran (Cisco) and
Rolf Blom (Ericsson) and first published by IETF in March 2004 as RFC 3711.
Since RTP is closely related to RTCP which can be used to control the RTP
session.
SRTCP - Secure RTCP
is a sister protocol to SRTP. SRTCP provides the same security-related
features to RTCP, as ones provided by SRTP to RTP.
Utilization of SRTP or SRTCP is
optional to utilization of RTP or RTCP; but even if SRTP/SRTCP are used, all
provided features (such as encryption and authentication) are optional and can
be separately enabled or disabled. The only exclusion is message authentication
feature which is indispensably required the for using SRTCP.
SRV Record -
An SRV record or
Service record is a category of data in the Internet Domain Name System
specifying information on available services. It is defined in
RFC 2782. Newer internet
protocols such as SIP and XMPP often require SRV support from clients. Client
implementations of older protocols (e.g. LDAP, SMTP) may have SRV support added
to it. An SRV record holds the following information:
 | Service: the
symbolic name of the desired service. |
 | Protocol:
this is usually either
TCP or
UDP.
|
 | Domain name: the
domain for which this record is valid. |
 | TTL: standard DNS
time to live field. |
 | Class: standard DNS
class field (this is always IN). |
 | Priority: the
priority of the target host. |
 | Weight: A relative
weight for records with the same priority. |
 | Port: the TCP or
UDP port on which the service is to be found. |
 | Target: the
hostname of the machine providing the service. |
An example SRV record: _sip._tcp.example.com 86400 IN SRV 0
5 5060 sipserver.example.com.
SRV
record is also used for load balancing:
The priority field is similar to an
MX record's
priority value. Clients always use the SRV record with the lowest priority value
first, and only fall back to other records if the connection with this record's
host fails. Thus a service may have a designated "fallback" server, which will
only be used if the primary server fails. Only another SRV record, with a
priority field value higher than the primary server's record, is needed.
SS7 - Signaling System 7
(SS7) is the protocol used in the public switched telephone system for setting
up calls and providing services such as tollfree numbers, call forwarding,
caller ID and local number portability.
Stereo Sound System -
The built-in stereo sound system incorporates an MTS decoder for reception and
reproduction of broadcast stereo television programs (where available).
Stereo Sound System with dbx®
Noise Reduction - Built-in stereo sound system includes MTS/SAP decoder and
dbx® noise reduction to eliminate hiss and high-frequency interference and add
impact to your classroom programs.
Streaming media -
Sending video or audio
over a network as needed, such as Real Audio/Video or Microsoft NetShow, instead
of forcing the user to download the entire file before viewing it. Typically a
few seconds of data is sent ahead and buffered in case of network transmission
delays. (Although some data is buffered to the hard drive, it is written to
temporary storage and is gone once viewing is complete.)
Student Syndrome - In
project management terminology,
Student Syndrome refers to the
phenomenon that many people will start to fully apply themselves to a task just
in the wake of a deadline. This leads to wasting any buffers built into
individual task duration estimates.
Super VGA - A term used
to denote higher than VGA (640 x 480) resolution. Most Super VGA computers/cards
output resolutions up to 1280 x 1024 and 16 million colors.
SVGA/VGA Input with
Loop-Through Output - Typical SVGA or VGA cables with D-shell connectors are
the only additional hardware required for hookup to a PC. Use the same cabling
setup with a VGA/Mac¨ adaptor and a SmartCard TelevisionTM will
accept most Mac® inputs. This port allows display of computer-generated data,
graphic images, animated models, or full-motion video with real-time keyboard
interactivity and display resolutions of 640 x 480, 800 x 600, or 1024 x 768.
Compatible with most PC and Mac® refresh rates, the SCN3NFN module offers
excellent performance from 50-75Hz.
S-Video - Composite
video signal separated into the luminance (black & white) and chrominance
(color), resulting in greater picture definition and superior definition.
S-Video Input - A
standard S-Video input simplifies connection to any S-VHS VCR/camcorder, Web
browser, or DVD player for the highest quality video images possible.
S-Video Input/Output
w/Loop-Thru Capability - Allows connection of high resolution sources such
as DVD, Web Browser or Laser Disc for maximum picture quality. Additionally, the
ProKit1 features separate audio inputs and outputs dedicated to the S-Video
signal. Loop-through capability allows one video source to be looped to multiple
sets.
Success Factors -
During the inception phase of a
RUP project, the key stakeholders should establish criteria by which the project
can be judged to have succeeded. These factors may include problems being
solved, financial or other performance targets to be achieved. Where the factor
is a fuzzy one (such as users being happy), this should be expressed in
measurable terms. A good success factor should always be testable, and normally,
UAT should be based on success criteria.
SYN Attacks - or SYN flood is a form of
denial-of-service attack in which an attacker sends a succession of
SYN
requests to a target's system. When a client attempts to start a
TCP connection to a server, the
client and
server exchange a series of messages which normally runs like this: 1-)
The client requests a
connection by sending a SYN
(synchronize) message to the server. 2-) The server acknowledges
this request by sending SYN-ACK
back to the client, which, 3-)
Responds with an
ACK,
and the connection is established. This is called the
TCP three-way handshake, and is the foundation for every connection
established using TCP/IP protocols. A malicious client can skip sending this last
ACK message. The server
will wait for this bit for some time, as simple network congestion could also be
the cause of the missing ACK. If this so called
half-open connection binds resources on the server or the server software is
licensed per-connection, as is the case in many
operating systems, it may be possible to take up all these resources or run
out of
Client Access Licenses by flooding the server with SYN messages. Once all
resources CALs set aside for half-open connections are reserved, no new
connections (legitimate or not) can be made, resulting in denial of service.
Some systems may malfunction badly or even crash if other operating system
functions are starved of resources this way. Countermeasures include
SYN
cookies or limiting the number of new connections from a source per
timeframe.
Sync - In video, a means
of synchronizing signals with timing pulses to insure that each step in a
process occurs at exactly the right time. For example: Horizontal Sync
determines exactly when to begin each horizontal line (sweep) of the electron
beam. Vertical Sync determines when to bring the electron beam to the top-left
of the screen to start a new field. There are many other types of sync in a
video system. (Also called Sync Signal or Sync Pulse.)
Synchronous
Optical Networking - commonly known as SONET, is a
standard for communicating digital information over optical
fiber. It was developed to replace the PDH system for
transporting large amounts of telephone and data traffic. It is
defined by GR-253-CORE from Telcordia. The more recent
Synchronous Digital Hierarchy (SDH) standard is built
on experience in the development of SONET. Both SDH and SONET
are widely used today; SONET in the U.S. and Canada, SDH in the
rest of the world. SDH is growing in popularity and is currently
the main concern with SONET now being considered as the
variation. SONET differs from PDH in that the exact rates
that are used to transport the data are tightly synchronized to
network based clocks. Thus the entire network operates
synchronously. SDH was made possible by the existence of atomic
clocks. Both SONET and SDH can be used to encapsulate
earlier digital transmission standards, such as the PDH
standard, or used directly to support either ATM or so-called
Packet over SONET networking. The basic SONET signal
operates at 51.840 Mbit/s and is designated STS-1 (Synchronous
Transport Signal one). The STS-1 frame is the basic unit of
transmission in SONET. The Synchronous Transport Module
level 1 (STM-1) is the basic signal rate of SDH.
SONET/SDH Designations and bandwidths
|
Optical Carrier Level |
Frame Format |
SDH Level |
Frame Format |
Line Rate (kbit/s) |
|
OC-1 |
STS-1 |
- |
- |
51 840 |
|
OC-3 |
STS-3 |
SDH-1 |
STM-1 |
155 520 |
|
OC-9 |
STS-9 |
- |
- |
466 560 |
|
OC-12 |
STS-12 |
SDH-4 |
STM-4 |
622 080 |
|
OC-18 |
STS-18 |
- |
- |
933 120 |
|
OC-24 |
STS-24 |
SDH-8 |
STM-8 |
1 244 160 |
|
OC-36 |
STS-36 |
SDH-12 |
STM-12 |
1 866 240 |
|
OC-48 |
STS-48 |
SDH-16 |
STM-16 |
2 488 320 |
|
OC-96 |
STS-96 |
SDH-32 |
STM-32 |
4 976 640 |
|
OC-192 |
STS-192 |
SDH-64 |
STM-64 |
9 953 280 |
|
OC-256 |
STS-256 |
- |
- |
13 271 040 |
|
OC-384 |
STS-384 |
- |
STM-128 |
19 906 560 |
|
OC-768 |
STS-768 |
- |
STM-256 |
39 813 120 |
|
OC-1536 |
STS-1536 |
- |
STM-512 |
79 626 240 |
|
OC-3072 |
STS-3072 |
- |
STM-1024 |
159 252 480 |
System Television Control
- Transmit live or pre-recorded media, control the power, adjust settings and
even lockout local control for individual TVs, select groups to all TVs in the
network.
BACK TO TOP
T
T1 (also known as DS1)
- A leased T1 line,
marketed and serviced by
LECs,
that provides 1.544 Mbps data rate (in N. America; the European E1 provides
2.048 Mbps). T1 is available almost everywhere, and can be fractionated.
Fractional T1 services are less expensive than full T1. Typical interactive
video-mediated telemedicine programs transmit video images at "1/4 T1" rates
(384 Kbps).
T3 (also know as DS3) - A
carrier of 45 Mbps bandwidth. One T3 channel can carry 28 T1 channels.
Transmission of both voice and data digital signals at speeds of 44.736 Mbps and
higher.
T.120 -
T.120 is an ITU-T standard
(International Telecommunications Union) for document conferencing. Document
conferencing allows two or more people to concurrently view and edit a document
across a network. T.120 is the commonly used name to refer to a family of
distinct standards. Many video conferencing companies were developing their own
implementations of this until Microsoft released its free NetMeeting software.
Now, many companies are using NetMeeting, while perhaps enhancing it in some
way.
Tamper-Proof Setup -
Institutional Televisions are designed to provide central control over the
programming features of each set. You can adjust all the things you'd
expect-picture level, brightness, color, tint, sharpness, as well as set up the
professional features that customize the unit exclusively for its intended
purpose via remote programming. To prevent users from tampering with the
controls or changing the programming you've worked so hard to customize, the
Limited Function Remote will give end users access to the basics-on/off, channel
and volume control, etc.
TDMA -
Time Division Multiple Access is a
technology for shared medium (usually radio) networks. It allows several users
to share the same frequency by dividing it into different time slots. The users
transmit in rapid succession, one after the other, each using their own
timeslot. This allows multiple users to share the same transmission medium (e.g.
radio frequency) whilst using only the part of its bandwidth they require. Used
in the GSM, PDC and iDEN digital cellular standards, among others. GSM,
TDMA, iDEN, PDC and PHS are all based on dividing a radio channel into time
slots. Each time slot can handle one call. These technologies differ in radio
channel sizes and the number of time slots. TDMA is also
used extensively in satellite systems, LANs, physical security systems, and
combat-net radio systems.
TDMoIP - takes advantage of
the concept of bundling conversations that are heading to the same destination
and wrapping them up inside the same packets. These can offer near toll quality
audio in a 6-7 kbit/s data stream.
Telecine -
A
film-to-videotape transfer technique that rectifies the respective color frame
rate differences between film and video.
Teleconferencing -
Two or more people who
are geographically distant having a meeting of some sort across a
telecommunications link. Includes audio conferencing, video conferencing, and or
data conferencing.
Telemedicine - The
investigation and monitoring of patients and the education of patients and staff
using systems which allow ready access to expert advice and patient information,
no matter where the patient or the relevant information is located. The three
main dimensions of telemedicine are health service, telecommunications, and
medical computer science.
Telementoring - Interaction
between medical personnel of different training levels- i.e. GMO and
Pulmonologist, Physician's Assistant and Emergency Physician, Medic and
Battalion Surgeon. The use of audio, video, and other telecommunications and
electronic information processing technologies to provide individual guidance or
instruction, for example, involving a consultant guiding a distant clinician in
a new medical procedure. Tele-monitoring The use of audio,
video, and other telecommunications and electronic information processing
technologies to monitor patient status at a distance.
Telenursing - The use of
telecommunications for nursing care.
Telepresence - The use of
robotic and other devices that allow a person (e.g., a surgeon) to perform a
task at a remote site by manipulation instruments (e.g., lasers or dental hand
pieces) and receiving sensory information or feedback e.g., pressure akin to
that created by touching a patient) that creates a sense of being present at the
remote site and allows a satisfactory degree of technical performance (e.g.,
dexterity).
Terminal Element -
a terminal element is the lowest
element (activity or deliverable) in a work breakdown structure(WBS); it is not
further subdivided. Terminal elements are the items that are estimated in
terms of resource requirements, budget and duration, linked by dependencies and
scheduled.
Terminal End Station -
A terminal end station
is the client endpoint that provides real-time, two-way communications. This is
often shortened to just terminal.
THIG - Topology Hiding Interface Gateway.
Thread - A thread in
computer science is short for a thread of execution. Threads are a
way for a
program to split itself into two or more simultaneously running
tasks. (The name
"thread" is by analogy with the way that a number of
threads are
interwoven to make a piece of fabric). Multiple threads can be executed in
parallel on many computer systems. This multithreading generally occurs
by
time slicing (where a single
processor
switches between different threads) or by
multiprocessing (where threads are executed on separate processors). Threads
are similar to
processes, but differ in the way that they share resources. Many modern
operating systems directly support both time-sliced and multiprocessor
threading with a process
scheduler.
The operating system
kernel allows programmers to manipulate threads via the
system
call interface. Some implementations are called kernel threads,
whereas lightweight processes is a specific type of kernel threads that
share the same states and information. Absent that, programs can still implement threading by using timers, signals, or
other methods to interrupt their own execution and hence perform a sort of ad
hoc time-slicing. These are sometimes called user-space threads. An unrelated use of the term thread is for
threaded code, which is a form of code consisting entirely of
subroutine
calls, written without the subroutine call instruction, and processed by an
interpreter or the
CPU. Two threaded code languages are
Forth and early
B programming languages.
Three-Prong Power Cord -
Designed for the most demanding environments, this product is perfect for
applications that require compliance with strict A/V electrical requirements.
Three-tier Architecture - In computing,
Three-tier is a
client-server architecture in which the
user interface,
functional process logic ("business rules"),
data
storage and
data
access are developed and maintained as independent
modules, most often on separate
platforms. The term "three-tier" or "three-layer", as well as the concept of
multitier architectures, seems to have originated within
Rational Software. The three-tier model is considered to be a
software architecture and a
software design pattern. Apart from the usual advantages of modular
software
with well defined interfaces, the three-tier architecture is intended to allow
any of the three tiers to be upgraded or replaced independently as requirements
or
technology change. For example, a change of
operating system from
Microsoft Windows to
Unix would only
affect the user interface code. Typically, the user interface runs on a desktop
PC or
workstation and uses a standard
GUI, functional process logic may consist of one or
more separate modules running on a workstation or
application server, and an
RDBMS on a
database server or
mainframe
contains the
data storage logic. The middle tier may be multi-tiered itself (in which
case the overall architecture is called an "n-tier architecture"). It seems similar, although defined in slightly different terms, to the
Model-view-controller concept and the
pipes and filters concept. Web services usage: In the
Web service field, normally three-tier is used to refer to
Websites,
often
Electronic commerce websites, which are built using three tiers:
- A front end Web server
serving static content
- A middle dynamic content
processing and generation level Application server, for example Java EE
platform.
- A back end Database,
comprising both data sets and the Database management system or RDBMS
software that manages and provides access to the data.
Throughput - The
amount of
data transferred from one
place to another or processed in a specified amount of time.
Data transfer rates for
disk drives and
networks are measured in
terms of throughput. Typically, throughputs are measured in
kbps,
Mbps and
Gbps.
Tier 1 Carrier -
A Tier 1 carrier is a telco or ISP that is at
the top of the telecommunications tier. Although there is no formal
definition, the following statements generally hold: 1-)
Tier 1 operators have operations
in more than one country. 2-)
Tier 1 operators own and operate
their own physical networks, and either own or have IRU's on their international
submarine cable links. 3-)
Tier 1 operators have revenue-neutral or settlement-free peering agreements with
other tier 1 operators in the same market. Furthermore, it is widely
accepted rule of thumb that Tier 1 operators do not pay for transit.
A given Tier 1 operator
might only be considered tier 1 in a particular market or markets (typically a
country or geographical area). For example, Reliance Infocom is undeniably tier
1 in India, but much too small to peer neutrally with Tier 1 operators in the
United States and Europe.
TISPAN - The Telecoms &
Internet converged Services & Protocols for Advanced Networks, formerly
Telecommunications and Internet Protocol Harmonization Over Networks (TIPHON) is
a standardization body of ETSI, specialized in fixed networks and Internet
convergence. TISPAN’s release 1 architecture is based upon the 3GPP IMS
Release 6 and 3GPP2 Revision A architectures. However, TISPAN has adopted a more
generalized model able to address a wider variety of network and service
requirements. This overall architecture is based upon the concept of cooperating
subsystems sharing common components. This subsystem-oriented architecture
enables the addition of new subsystems over the time to cover new demands and
service classes. It also ensures that the network resources, applications, and
user equipment (mostly inherited from IMS where possible) are common to all
subsystems and therefore ensure user, terminal and service mobility to the
fullest extent possible, including across administrative boundaries.
TMSI -
The Temporary Mobile Subscriber Identity is the identity that is most
commonly sent between the mobile and the network. It is a randomly allocated
number that is given to the mobile, the moment it is switched on. The number is
local to a location area, and so it has to be updated, each time the mobile
moves to a new geographical area. The network can also change the TMSI of the mobile at any time. And it normally
does so, in order to avoid the subscriber from being identified, and tracked by
eavesdroppers on the radio
interface.
This makes it difficult to trace which mobile is which, except briefly, when the
mobile is just switched on, or when the data in the mobile becomes invalid for
one reason or another. At that point, the global "international mobile
subscriber identity" (IMSI)
must be sent to the network. This is a unique number that is associated with all
GSM and UMTS network mobile phone users. The number is stored in the
SIM card. The IMSI is
sent as rarely as possible, to avoid it being identified and tracked. A key use of the TMSI is in paging a mobile. "Paging" is the one-to-one
communication between the mobile and the base station. The most important use of
broadcast information is to set up channels for "paging". Every cellular system
has a
broadcast mechanism to distribute such information to a plurality of
mobiles.
Total Control -TVs that
are designed to give you control over the programming features of each set, and
control end user access to your programming. In addition, Front Control
Lockout locks all front controls, preventing anyone from changing the volume,
channel or other television settings.
Traffic Engineering - Traffic engineering uses
statistical
techniques such as
queuing theory to predict and engineer the behavior of
telecommunications networks such as
telephone
networks or the
Internet. The field was created by the work of
A. K. Erlang in whose honor the unit of telecommunication
traffic intensity, the
Erlang
is named. The derived unit of
traffic volume also incorporates his name. His
Erlang distributions are still in common use in telephone traffic
engineering. The crucial observation in traffic engineering is that in large systems the
law of large numbers can be used to make the aggregate properties of a
system over a long period of time much more predictable than the behavior of
individual parts of the system. The queuing theory originally developed for
circuit-switched networks is applicable to
packet-switched networks. The most notable difference between these sub-fields is that packet-switched
data traffic is
self-similar. This is a consequence of the calls being between computers,
and not people.
Traffic Volume - In
telecommunication networks, traffic volume is a measure of the total
work done by a resource or
facility,
normally over 24 hours, and is measured in units of Erlang-hours. It is defined
as the product of the average traffic intensity (in Erlang) and the period of
study (in hours). A traffic volume of one Erlang-hour can be caused by two circuits being occupied
continuously for half an hour or by a circuit being half occupied (0.5 Erlang)
for a period of two hours. Telecommunication operators are vitally interested in
traffic volume, as it directly dictates their revenue.
Transcoder - A device that does transcoding. See below.
Transcoding -
Converting a data
stream from one format to another, such as MPEG 1 to H.263, or an H.320
videoconferencing session to H.323.
Truespeech -
Truespeech is a codec
used for low bandwidth encoding of speech (not music). It was created by the DSP
Group. It is available on Microsoft Windows 98 among other systems.
Turn-key system - A
Telecommunications system in which all components and installation services
needed for operational teleconferencing have been provided by a single vendor or
contractor.
Two-Way Communications -
Transmitter and receiver on different frequencies allows two-way communication
for example between the computer head-end and individual TVs in the network for
monitoring, function controls and event scheduling.
BACK TO TOP
U
UAT -
User Acceptance Testing
UAV -
Unmanned Aerial Vehicle
UGV -
Unmanned Ground Vehicle
UMA -
Unlicensed Mobile Access technology provides access to GSM and GPRS mobile
services over unlicensed spectrum technologies, including Bluetooth and 802.11.
By deploying UMA technology, service providers can enable subscribers to roam
and handover between cellular networks and public and private unlicensed
wireless networks using dual-mode mobile handsets. With UMA, subscribers receive
a consistent user experience for their mobile voice and data services as they
transition between networks. UMA technology characteristics: 1-) Seamless delivery of mobile voice and data services over unlicensed wireless
networks. 2-) Provides the same mobile identity on Cellular RAN and unlicensed wireless
networks. 3-) Seamless transitions (roaming and handover) between Cellular RAN
and unlicensed wireless networks. 4-) Preserves investment in existing/future
mobile core network infrastructure. 5-) Independent of underlying
unlicensed spectrum technology (e.g. WiFi™, Bluetooth™). 6-)Transparent to
existing, standard CPE devices (e.g. access points, routers and modems).
7-)Utilizes standard “always on" broadband IP access networks (e.g. DSL, Cable,
T1/E1, Broadband Wireless, FTTH …). 8-)Security equivalent to current GSM
mobile networks. 9-) No impact to operations of Cellular RAN (e.g.
spectrum engineering, cell planning,…)
UML - Unified
Modeling Language.
UML
is a powerful
tool for developers to use when working on object-oriented
systems. Because its purpose is to document and model a software
system using a language-independent methodology, software
designers can more easily communicate their designs to other
designers and to those who ultimately implement the software.
From a UML model an SDL design can be generated. The SW design
engineer can either use a tool (e.g. Telelogic' SDT) to generate
the actual code, or handover the SDL design to an experienced
coder to generate the code as per the low level design SDL
specifications.
UMTS -
Universal Mobile Telecommunications System (UMTS) is a part of the International
Telecommunications Union’s IMT-2000 vision of a global family of
third-generation (3G) mobile communications systems. This version of 3G is a
W-CDMA (Wideband-CDMA) technology being developed primarily by the European and
Japanese. UMTS is the 3G technology designed to succeed GSM networks worldwide.
UMTS combines the W-CDMA air interface, GSM's Mobile Application Part (MAP)
core, and the GSM family of speech codecs. UMTS standard are 1885-2025 MHz
for uplink and 2110-2200 MHz for downlink. A major difference of UMTS
compared to GSM is the air interface forming Generic Radio Access Network
(GRAN). It can be connected to various backbone networks like the Internet,
ISDN, GSM or to a UMTS network. GRAN includes the three lowest layers of OSI
model. The network layer (OSI L3) protocols form the Radio Resource Management
protocol (RRM). They manage the bearer channels between the mobile terminals and
the fixed network including the handovers. There are other competing 3G
standards, such as CDMA2000 and systems including iBurst from Arraycom, Flarion
and wCDMA-TDD (IPWireless). Both CDMA2000 and W-CDMA are accepted by ITU
as part of the IMT-2000 family of 3G standards, in addition to Enhanced Data
Rates for Global Evolution (EDGE) and China's own 3G standard, TD-SCDMA.
The UMTS spectrum allocated by ITU is already used in North America. The 1900
MHz range is used for 2G (PCS) services, and 2100 MHz range is used for
satellite communications. Regulators are trying to free up the 2100 MHz range
for 3G services, though UMTS in North America will still have to share spectrum
with existing 2G services in the 1900 MHz band. 2G GSM services elsewhere use
900 MHz and 1800 MHz and therefore do not share any spectrum with planned UMTS
services. Until regulators allocate new spectrum specifically for 3G,
there will be no firm answer to what frequencies UMTS will operate on in North
America. AT&T Wireless launched UMTS services in the United States by the end of
2004 strictly using the existing 1900 MHz spectrum allocated for 2G PCS
services. Cingular acquired AT&T Wireless in 2004 and has since then launched
UMTS in select US cities. Initial rollout of UMTS in Canada will also be handled
exclusively by the 1900 MHz band.
Unicast -
Sending each user
their own copy of a video (or other data) stream. As opposed to Multicast, where
one copy is sent and whoever wants it listens to that copy.
Underscan - A decreasing of
the raster size (H & V) so that four edges of the picture are visible on the
screen. Underscanning allows viewing of skew and tracking which would not be
visible in normal (overscanned) mode. It is also helpful when aligning test
charts to be certain they touch all four corners of the raster. Likewise, when
checking the alignment of multiplexer images from a film chain, underscan allows
proper framing of the projected image going into the video camera.
URI - A Uniform Resource Identifier is an
Internet
protocol element consisting of a short
string of
characters that conform to a certain
syntax. The
string comprises a name or address that can be used to refer to a
resource. It is a fundamental component of the
World Wide Web. A URI can be classified as a locator or a name or both. A
Uniform Resource Locator (URL) is a URI that, in addition to identifying a
resource, provides means of acting upon or obtaining a representation of the
resource by describing its primary access mechanism or network "location". For
example, the URL http://www.atksi.com/ is a URI that identifies a
resource (ATKSI's home page) and implies that a representation of that
resource (such as the home page's current HTML code, as
encoded characters) is obtainable via
HTTP from a network host named www.atksi.com. A
Uniform Resource Name (URN) is a URI that identifies a resource by name in a
particular
namespace. A URN can be used to talk about a resource without implying its
location or how to dereference it. For example, the URN urn:ISBN
0-123-45678-9 is a URI that, like an International Standard Book Number
(ISBN), allows one
to talk about a book, but doesn't suggest where and how to obtain an actual copy
of it. The contemporary point of view among the
working group that oversees URIs is that the terms URL and URN are
context-dependent aspects of URI and rarely need to be distinguished.
Furthermore, the term URL is increasingly becoming obsolete, as it is rarely
necessary to differentiate between URLs and URIs, in general. The term web
address has also replaced URL in terms of popular usage.
The
URI syntax is essentially a
URI scheme
name like "http",
"ftp",
"mailto", "urn",
etc., followed by a
colon character, and then a scheme-specific part. The syntax and
semantics
of the scheme-specific part are determined by the specifications that govern the
schemes, although the URI syntax does force all schemes to adhere to a certain
general syntax that, among other things, reserves certain characters for special
purposes, without always saying what those purposes are. The URI syntax also
enforces restrictions on the scheme-specific part, in order to, for example,
provide for a degree of consistency when the part has a hierarchical structure.
Percent-encoding is an often misunderstood aspect of URI syntax. An
example URI: http://somehost/absolute/URI/with/absolute/path/to/resource.txt
User Agent -
A user agent is the
client application used with a particular
network protocol; the phrase is most commonly used in reference to those
which access the
World Wide Web. Web user agents range from
web
browsers to
search engine crawlers
("spiders"), as well as
mobile
phones,
screen readers and
Braille
browsers used by people with disabilities. When Internet users visit a web site, a text
string is generally sent to identify the user agent to the
server.
This forms part of the
HTTP request, prefixed with User-agent: or User-Agent: and
typically includes information such as the application name, version, host
operating system, and language.
Bots,
such as web crawlers, often also include a
URL and/or
e-mail address so that the
webmaster
can contact the operator of the bot. The user-agent string is one of the criteria by which crawlers can be excluded
from certain pages or parts of a website using the "Robots
Exclusion Standard" (robots.txt). This allows webmasters who feel
that certain parts of their website should not be included in the data gathered
by a particular crawler, or that a particular crawler is using up too much
bandwidth,
to request that crawler not to visit those pages.
Uses RF Distribution -
TVs that do not require special cables or wiring but use simple RF distribution
systems currently found in most locations with cable access.
UTRAN -
UMTS Terrestrial Radio Access Network,
is a collective term for the
Node-B's and
Radio Network Controllers which make up the
UMTS
radio access network. This communications network, commonly referred to as
3G (for 3rd Generation Wireless Mobile Communication Technology), can carry many
traffic types from real-time
Circuit Switched to
IP based
Packet Switched. The UTRAN allows connectivity between the UE (user
equipment) and the core network. UMTS is using code division multiple access
(CDMA). See also
GERAN. The UTRAN contains the base stations, which are called Node Bs, and
Radio Network Controllers (RNC). The RNC provides control functionalities for
one or more Node Bs. A Node B and an RNC can be the same device, although
typical implementations have a separate RNC located in a central office serving
multiple Node B's. Despite the fact that they do not have to be physically
separated, there is a logical interface between them known as the Iub. The RNC
and its corresponding Node Bs are called the Radio Network Subsystem (RNS).
There can be more than one RNS present in an UTRAN. There are four interfaces connecting the UTRAN internally or externally to other
functional entities: lu, Uu, lub and lur. The lu interface is an external
interface that connects the RNC to the Core Network (CN). The Uu is also
external, connecting the Node B with the User Equipment (UE). The lub is an
internal interface connecting the RNC with the Node B. And at last there is the
lur interface which is an internal interface most of the time, but can,
exceptionally be an external interface too for some network architectures. The
lur connects two RNCs with each other.
UV -
Ultraviolet
radiation is electromagnetic radiation of a wavelength shorter
than that of the visible region, but longer than that of soft
X-rays. It can be subdivided into near UV (380–200 nm
wavelength) and extreme or vacuum UV (200–10 nm). When
considering the effects of UV radiation on human health and the
environment, the range of UV wavelengths is often subdivided
into UVA (380–315 nm), also called Long Wave or "blacklight";
UVB (315–280 nm), also called Medium Wave; and UVC (280-10 nm),
also called Short Wave or "germicidal".
BACK TO TOP
V
8-VSB - (8-level
vestigial sideband) is a standard radio frequency (RF)
modulation format chosen by the Advanced Television Systems Committee (ATSC) for
the transmission of digital television (DTV)
to consumers in the United States and other adopting countries. In the US, the
standard is specified by the Federal Communications Commission (FCC) for all
digital television broadcasting. Countries in Europe and elsewhere have adopted
the COFDM format.
V.80 -
Application interface defined in
the H.324 ITU videoconferencing standards. It provides a standard method
for H.324 applications to communicates over modems. Also see H.324
ViDe -
Video Development
Group. Currently consists of the Georgia Institute of Technology, North Carolina
State University, the University of North Carolina, Chapel Hill, and the
University of Tennessee, Knoxville, in partnership with NYSERNet (New York State
Education, Research Network).
Video on demand -
Being able to view any
of a number of videos when you want to. Used on the internet and at hotels,
cable systems, etc.
Video server -
A computer server that
has been designed to store large amounts of video and stream it to users as
required. Usually a video server has large amounts of high speed disks and a
large amount of network bandwidth to allow for many users to simultaneously view
videos.
Video Stream -
A bit sequence
of compressed digital video. Another term for a video sequence.
Videoconferencing - also known as a video teleconference is a set of interactive
telecommunication
technologies which allow two or more locations to interact via two-way video
and audio transmissions simultaneously. It has also been called visual
collaboration and is a type of
groupware. Simple analog videoconferences could be established as early as the invention of
the
television. Such videoconferencing systems consisted of two
closed-circuit television systems connected via cable. During the first
manned
space flights, NASA
used two radiofrequency (UHF
or VHF) links, one in
each direction. TV channels routinely use this kind of videoconferencing when
reporting from distant locations, for instance. Then mobile links to
satellites
using special trucks became rather common. This technique was very expensive, though, and could not be used for more
mundane applications, such as
telemedicine,
distance education, business meetings, and so on, particularly in
long-distance applications. Attempts at using normal
telephony
networks to transmit
slow-scan video, such as the first systems developed by
AT&T, failed
mostly due to the poor picture quality and the lack of efficient video
compression techniques. It was only in the
1980s that
digital telephony transmission networks became possible, such as
ISDN, assuring a
minimum
bandwidth (usually 128 kilobits/sec) for compressed video and audio
transmission. The first dedicated systems, such as those manufactured by
pioneering VTC firms, like
PictureTel, started to appear in the market as ISDN networks were expanding
throughout the world. Video teleconference systems throughout the 1990's rapidly
evolved from highly expensive proprietary equipment, software and network
requirements to standards based technology that is readily available to the
general public at a reasonable cost. Finally, in the
1990s, IP
(Internet Protocol) based videoconferencing became possible, and more efficient
video compression technologies were developed, permitting desktop, or personal
computer (PC)-based videoconferencing. VTC arrived to the masses and free
services and software, such as
NetMeeting,
MSN
Messenger,
Yahoo Messenger, and others brought cheap, albeit low-quality, VTC.
The core technology used in a video teleconference (VTC) system is digital
compression of audio and video streams in real time. The hardware or software
that performs compression is called a codec (coder/decoder). Compression rates
of up to 1:500 can be achieved. The resulting digital stream of 1's and 0's is
subdivided into labeled packets, which are then transmitted through a digital
network of some kind (usually ISDN or IP). The use of audio modems in the
transmission line allow for the use of POTS, or the plain telephony network in
some low-speed applications, such as video telephony, because they convert the
digital pulses to/from analog waves in the audio spectrum range. The other components required for a VTC system include:
 | video input: video
camera or webcam |
 | video output:
computer monitor or television |
 | audio input:
microphones |
 | audio output:
usually loudspeakers associated with the display device or telephone
|
 | data transfer:
analog or digital telephone network, LAN or Internet |
There are basically two kinds of VTC systems:
- Dedicated systems
have all required components packaged into a single piece of equipment,
usually a console with a high quality remote controlled video camera. These
cameras can be controlled at a distance to pan left and right, tilt up and
down, and zoom. They became known as PTZ cameras. The console contains all
electrical interfaces, the control computer, and the software or
hardware-based codec. Omnidirectional microphones are connected to the
console, as well as a TV monitor with loudspeakers and/or a video projector.
There are several types of dedicated VTC devices:
- Large group VTC are
non-portable, large, more expensive devices used for large rooms and
auditoriums.
- Small group VTC are
non-portable or portable, smaller, less expensive devices used for small
meeting rooms.
- Individual VTC are
usually portable devices, meant for single users, have fixed cameras,
microphones and loudspeakers integrated into the console.
- Desktop systems are add-ons (hardware boards, usually) to normal PC's,
transforming them into VTC devices. A range of different cameras and microphones
can be used with the board, which contains the necessary codec and transmission
interfaces. Most of the desktops systems work with the H.323 standard. Video
conferences carried out via dispersed PCs are also known as e-meetings.
A fundamental feature of professional VTC systems is Acoustic Echo
Cancellation (AEC). AEC is an
algorithm
which is able to detect when sounds or utterances reenter the audio input of the
VTC codec, which came from the audio output of the same system, after some
time delay.
If unchecked, this can lead to several problems including 1) the remote party
hearing their own voice coming back at them (usually significantly delayed) 2)
strong
reverberation, rendering the voice channel useless as it becomes hard to
understand and 3) howling created by feedback. Echo cancellation is a
processor-intensive task that usually works over a narrow range of sound delays. Simultaneous videoconferencing among three or more remote points is
possible by means of a Multipoint Control Unit (MCU). This is a bridge that
interconnects calls from several sources (in a similar way to the audio
conference call). All parties call the MCU unit, or the MCU unit can also call
the parties which are going to participate, in sequence. There are MCU bridges
for IP and ISDN-based videoconferencing. There are MCUs which are pure software,
and others which are a combination of hardware and software. An MCU is
characterized according to the number of simultaneous calls it can handle. MCUs can be stand-alone hardware devices, or they can be embedded into dedicated
VTC units.
Standards: The International Telecommunications Union (ITU) (formerly:
Consultative Committee on International Telegraphy and Telephony (CCITT)) has
three umbrellas of standards for VTC:
-
ITU
H.320 is known as the standard for public switched telephone networks (PSTN)
or VTC over integrated services digital networks (ISDN) basic rate interface
(BRI) or primary rate interface (PRI). H.320 is also used on dedicated
networks such as T1 and satellite-based networks;
- ITU H.323 is known as the
standard for video over Internet Protocol (IP). This same standard also
applies to voice over IP VoIP);
- ITU H.324 is the standard
for transmission over POTS, or audio telephony networks.
In recent years, IP based videoconferencing has emerged as a common
communications interface and standard provided by VTC manufacturers in their
traditional ISDN-based systems. Business, government and military organizations
still predominantly use H.320 and ISDN VTC. Though, due to the price point and
proliferation of the Internet, and broadband in particular, there has been a
strong spurt of growth and use of H.323, IP VTC. H.323 has the advantage that it
is accessible to anyone with a high speed Internet connection, such as DSL. In addition, an attractive factor for IP VTC is that it is easier to set-up for
use with a live VTC call along with
data collaboration [web conferencing (ITU T.120 standard)]. These combined
technologies enable users to have a much richer
multimedia
environment for live meetings, collaboration and presentations. Videoconferencing is a very useful technology for
telemedicine and
telenursing applications, such as
diagnosis,
consulting, transmission of
medical images, etc., in real time. Using VTC, patients may contact
nurses and
physicians
in medical
emergency or routine situations, physicians and other
paramedical professionals can discuss cases across large distances. Rural
areas can use this technology for diagnostic purposes, thus saving lives and
making more efficient use of health care dollars. Special peripherals such as
microscopes
fitted with
digital cameras,
videoendoscopes,
medical ultrasound imaging devices,
Otoscope,
etc., can be used in conjunction with VTC equipment to transmit data about a
patient.
VLAN -
A
virtual
LAN, commonly known as a vLAN, is a
logically-independent
network. Several VLANs can co-exist on a single physical
switch. A VLAN consists of a network of computers that behave as if connected to the
same wire - even though they may actually physically connect to different
segments of a LAN. Network administrators configure VLANs through software
rather than hardware, which makes them extremely flexible. One of the biggest
advantages of VLANs emerges when physically moving a computer to another
location: it can stay on the same VLAN without the need for any hardware
reconfiguration. The IEEE 802.1Q tagging protocol dominates the VLAN
world. Prior to the introduction of 802.1Q several proprietary protocols
existed, such as Cisco's ISL
(Inter-Switch Link, a variant of IEEE 802.10) and 3Com VLT (Virtual LAN Trunk).
Some users now deprecate ISL in favor of 802.1Q. Virtual LANs operate at layer 2
(the data link layer) of the OSI model. However, administrators often configure
a VLAN to map directly to an IP network, or subnet, which gives the appearance
of involving layer 3 (the network layer). In the context of VLANs, the term "trunk" denotes a network link carrying
multiple VLANs which are identified by labels (or "tags") inserted into their
packets. Such trunks must run between "tagged ports" of VLAN-aware devices, so
are often switch-to-switch or switch-to-router
links rather than links to hosts. (Confusingly, the term 'trunk' also gets used
for what Cisco call "channels" :
Link
Aggregation or Port Trunking). A
router (Layer 3
switch) serves as the
backbone for network traffic going across different VLANs. On Cisco devices, VTP
(VLAN Trunking Protocol) allows for VLAN domains, which can aid in
administrative tasks. VTP also allows "pruning", which involves directing
specific VLAN traffic only to switches which have ports on the target VLAN.
VLR -
The Visitor Location
Register is a database, part of the GSM system, which stores
information about all the mobiles that are currently under the jurisdiction of
the MSC to which VLR is attached. Each
Base Station in the network is served by exactly one VLR, hence a subscriber
cannot be present in more than one VLR at a time. The data stored in the VLR has either been received from the HLR, or collected
from the Mobile Station (MS). Whenever MSC detects a new MS in its network, in
addition to creating a new record in VLR, it also updates the HLR of the mobile
subscriber apprising it about the new location of MS. In practice, for performance reasons, most vendors integrate the
VLR directly to the V-MSC and, where this is not done, the VLR is very tightly
linked with the MSC via a proprietary interface.
Of all the information it stores
about MS, the most important is LAI (Location Area Identity). LAI identifies
under which BSC (Base Station Controller) is the MS currently present. This
information is very vital in call set up process. Data stored includes:
 | IMSI (the subscriber's
identity number) |
 | authentication data
|
 | MSISDN (the subscriber's
phone number) |
 | GSM services that the
subscriber is allowed to access |
 | Access Point (GPRS)
subscribed |
 | the HLR address of the
subscriber |
Voice activated switching -
Automatically
switching the video feed to whomever is speaking in a multipoint video
conference. Usually a function of the MCU (multipoint conferencing unit)
Voice over PSN (Packet
Switching Network) - VoIP and VoFR are
technologies
that use Access Devices (such as VFRADs/Routers and so forth) that employ
sophisticated schemes to overcome the limitations. Prioritization,
fragmentation, silence suppression, voice compression,
packet loss
concealment (PLC)
are example of such schemes.
VoIP -
Voice over Internet Protocol also
known as VoP (Voice over Packets), allows the voice to travel simultaneously
over a single packet network line with both fax and modem data.
VoFR -
VoFR (Voice over Frame Relay)
enables a router to carry voice traffic, such as telephone calls and faxes, over
a frame relay network.
VoATM -
Voice over ATM enables an ATM
switch to carry voice traffic over an ATM network.
VPN - Virtual Private
Network. is a private
communications network usually used within a company, or by several different
companies or organizations, communicating over a public network. VPN message
traffic is carried on public networking infrastructure (e.g. the Internet) using
standard (often insecure) protocols, or over a service providers network
providing VPN service guarded by well defined Service Layer Agreement (SLA)
between the VPN customer and the VPN Service Provider. There are three
main types of VPN: Intranet VPN over a common network
infrastructure, Remote Access VPN mainly for users with laptop
connecting intermittently from vary diverse locations , and Extranet VPN
using the Internet as the backbone network. Secure VPNs use
cryptographic tunneling protocols to provide the necessary confidentiality
(preventing snooping), sender authentication (preventing identity spoofing), and
message integrity (preventing message alteration) to achieve the privacy
intended. When properly chosen, implemented, and used, such techniques can
provide secure communications over unsecured networks. Because such
choice, implementation, and use are not trivial, there are many insecure VPN
schemes on the market. Secure VPN technologies may also be used to enhance
security as a 'security overlay' within dedicated networking infrastructures.
Secure VPN protocols
include the following: 1-) IPsec (IP security), an obligatory part of IPv6.
1a-) L2TP and L2TPv3:
inside of IPsec , 2-) SSL used either for tunneling the entire network
stack, such as in
OpenVPN, or for securing
what is essentially a web proxy. Although the latter is often called a "SSL
VPN" by VPN vendors, it is not really a fully-fledged VPN. 3-) PPTP
(point-to-point tunneling protocol), developed by Microsoft.
Some large ISPs now offer
"managed" VPN service for business customers who want the security and
convenience of a VPN but prefer not to undertake administering a VPN server
themselves. In addition to providing remote workers with secure access to
their employer's internal network, sometimes other security and management
services are included as part of the package, such as keeping anti-virus and
anti-spyware programs updated on each client's computer.
Trusted VPNs do not
use cryptographic tunneling, and instead rely on the security of a single
provider's network to protect the traffic. Multi-protocol label switching
(MPLS) is commonly used to build trusted VPNs. Other protocols for trusted
VPNs include: 1-) L2F (Layer 2 Forwarding), developed by Cisco. 2-) L2TP
(Layer 2 Tunneling Protocol), including work by both Microsoft and Cisco.
3-) L2TPv3 (Layer 2 Tunneling Protocol version 3).
VToA - Voice Telephony over
ATM is based on ATM Forum specification atm-vtoa-0078, which was developed for
carrying CBR (Continuous Bit Rate) services over ATM.
V-Chip Compliant
- Allows viewer to set level of access to certain channels and/or programs. The
access level is dictated by the TV Parental Guidelines rating assigned to all
television programs.
VGA (Video
Graphics Array) - Introduced by IBM in 1987, VGA is an Analog signal with
TTL level separate horizontal and vertical sync. The video outputs to a 15-pin,
HD connector and has a horizontal scan frequency of 31.5 kHz and vertical
frequency of 70 Hz (Mode 1, 2) and 60 Hz (Mode 3). The signal is non-interlaced
in modes 1, 2, 3 and interlaced when using the 8514/A card (35.5 kHz, 86 Hz) in
mode 4. It has a Pixel by Line resolution of 640 x 480 with a color palette of
16/256,000.
Volume Limiter
- Allows both the minimum and maximum volume range to set to a pre-determined
level, preventing volume from being adjusted too high or too low when in use.
Volume Management
- Acting as a volume limiter, this feature offers the ability to limit the
maximum and in some televisions, the minimum volume coming from the set. The
volume can also be set to a volume lock mode so that the volume cannot be turned
up or down. Finally the volume can also be set to an on mode where the volume
will always come up to the right level.
BACK TO TOP
W
WAN - Wide Are Network.
Computer and voice network bigger than a city or metropolitan area.
WAP -
Wireless Application Protocol, a
secure specification that allows users to access information instantly via
handheld wireless devices such as mobile phones, pagers, two-way radios,
smartphones and communicators. WAP is a set
of standards that enables a wireless device to browse content from
specially-coded Web pages. The WAP 2.0 specification integrates capabilities of
the rival i-mode standard.
wavelength - is
the distance between repeating units of a wave pattern. It is commonly
designated by the Greek letter lambda
(λ). In a sine wave, the wavelength is the distance between peaks
W-CDMA - Wideband CDMA
(WCDMA) is a version of CDMA that uses 10 MHz of wireless spectrum: a 5-MHz
uplink from the mobile terminal and a 5-MHz downlink to the mobile terminal. The
version of WCDMA used by NTT DoCoMo in Japan is called FOMA or J-WCDMA; the
European version is referred to as UMTS or E-WCDMA.
WBS -
In project management, a work
breakdown structure (WBS) is an exhaustive, hierarchical (from
general to specific) tree structure of deliverables and tasks that need to be
performed to complete a project.
Web Portal -
Web portals are sites on the
World Wide Web that typically provide personalized capabilities to their
visitors. They are designed to use
distributed applications, different numbers and types of
middleware
and hardware to provide services from a number of different sources. In
addition, business portals are designed to share collaboration in workplaces. A
further business-driven requirement of portals is that the content be able to
work on multiple platforms such as
personal computers,
personal digital assistants (PDAs), and
cell
phones. In the late 1990s,
the Web portal was a hot commodity. After the proliferation of
Web
browsers in the mid-1990s, many companies tried to build or acquire a
portal, to have a piece of the Internet market. The Web portal gained special
attention because it was, for many users, the starting point of their Web
browser.
Netscape Netcenter became a part of
America Online, the
Walt Disney Company launched
Go.com, and
Excite became a
part of AT&T
during the late 1990s.
Lycos was said to
be a good target for other media companies such as
CBS.Many of the portals started initially as either web directories (notably
Yahoo!)
and/or search engines (Excite, Lycos,
AltaVista,
infoseek,
and Hotbot
among the old ones). The expansion of service provision occurred as a strategy
to secure the user-base and lengthen the time a user stays on the portal.
Services which require user registration such as free email, customization
features, and chatrooms were considered to enhance repeat use of the portal.
Game, chat, email, news, and other services also tend to make users stay longer,
thereby increasing the advertisement revenue. The portal craze, with "old media" companies racing to outbid each other for
Internet properties, died down with the dot-com burst in 2000 and 2001.
Disney pulled
the plug on Go.com,
Excite went
bankrupt and its remains were sold to
iWon.com.
Some notable portal sites --- for instance,
Yahoo!,
remain successful to this day. To modern dot-com businesses, the portal craze
serves as a cautionary tale about the risks of rushing into a market crowded
with highly-capitalized but largely undifferentiated me-too companies.
Web service -
According to the W3C
a Web service (or Web Service)
is a software system designed to support interoperable machine-to-machine
interaction over a network. It has an interface that is described in a machine
process-able
format such as WSDL.
Other systems interact with the Web service in a manner prescribed by its
interface using messages, which may be enclosed in a
SOAP envelope, or
follow a REST
approach. These messages are typically conveyed using
HTTP, and normally
comprise XML in
conjunction with other Web-related standards. Software applications written in
various programming languages and running on various platforms can use
web
services to exchange data over
computer networks like the
Internet in
a manner similar to
inter-process communication on a single computer. This interoperability (for
example, between
Java and
Python, or Microsoft Windows and
Linux
applications) is due to the use of
open
standards.
OASIS and the
W3C are the primary committees responsible for the architecture and
standardization of web services. To improve interoperability between web service
implementations, the
WS-I organization has been developing a series of profiles to further define
the standards involved. Web services standards features such as
transactions are currently nonexistent or still in their infancy compared to
more mature
distributed computing open standards such as
CORBA. This is
likely to be a temporary disadvantage as most vendors have committed to the
OASIS standards to implement the Quality of Service aspects of their
products. Web services may suffer from poor
performance compared to other distributed computing approaches such as
RMI, CORBA,
or
DCOM. The standards used:
 | Web
Services Protocol Stack: The Standards and protocols used to
consume a web service, considered as a protocol stack.
|
 | XML: All
data to be exchanged is formatted with XML tags. The encoded
message may conform to a messaging standard such as SOAP or
the older XML-RPC. The XML-RPC scheme calls functions
remotely, whilst SOAP favors a more modern (object-oriented)
approach based on the Command pattern. |
 | Common
protocols: data can be transported between applications
using any number of common protocols, such as HTTP, FTP,
SMTP and XMPP. |
 | WSDL: The
public interface to the web service is described by Web
Services Description Language, or WSDL. This is an XML-based
service description on how to communicate using the web
service. |
 | UDDI: The
web service information is published using this protocol. It
should enable applications to look up web services
information in order to determine whether to use them.
|
 | ebXML: A
modular electronic business framework is enabled using this
set of specifications. The vision of ebXML is to enable a
global electronic marketplace where enterprises of any size
and in any geographical location can meet and conduct
business with each other through the exchange of XML-based
messages. |
 |
WS-Security: The Web Services Security protocol has been
accepted as an OASIS standard. The standard allows
authentication of actors and confidentiality of the messages
sent. |
 |
WS-ReliableExchange: A SOAP-based specification that
fulfills reliable messaging requirements critical to some
applications of Web Services. Accepted as an OASIS standard.
|
 |
WS-Management: This specification describes a SOAP-based
protocol for systems management of personal computers,
servers, devices, and other manageable hardware and Web
services and other applications. |
WDM -
In telecommunications Wavelength
Division Multiplexing is a technology which multiplexes several optical carrier
signals on a single optical fiber by using different wavelengths (colors) of
laser light to carry different signals.
Wideband - a communications
medium or signal that spans a large (continuous) range of frequencies, or is
wide compared to something else.
Wideband Delphi - The Wideband Delphi estimation method is a consensus-based estimation technique
for estimating effort. It was developed in the 1940s at the Rand Corporation as
a forecasting tool. It has since been adapted across many industries to estimate
many kinds of tasks, ranging from statistical data collection results to sales
and marketing forecasts. It has proven to be a very effective estimation tool,
and it lends itself well to software projects.
Windows®-based
Network Control - Allows Windows®-based control of a television network
using existing RF (cable) distribution system wiring with Windows 95/98/NT.
WiBro -
is a Broadband Wireless
internet technology being developed by the Korean telecom industry. In February
2002, the Korean Government allocated 100MHz of electromagnetic spectrum in the
2.3GHz band, and in late 2004 WiBro Phase 1 was standardized by the
TTA (Telecommunications Technology Association) of Korea.
WiBro base stations will offer an
aggregate data throughput of 30 to 50 Mbps and cover a radius of 1-5 km.
SK Telecom and
Hanaro Telecom have announced a partnership to roll out
WiBro nationwide in Korea, excluding Seoul and six provincial cities, where
independent networks will be rolled out. In November 2004, Intel and
LG Electronics executives agreed to ensure
compatibility between WiBro and WiMAX technology. In September 2005,
Samsung Electronics signed a deal with Sprint Nextel Corporation to provide
equipment for a WiBro trial.
Wi-Fi - stands for “Wireless
Fidelity” and is a logo provided by the Wireless Ethernet Compatibility
Association (WECA) for the 802.11b wireless Ethernet standard. Compatible PC
cards and base stations can use the Wi-Fi logo. It is a mark of compatibility.
WiMAX -
WiMAX is defined as Worldwide Interoperability for Microwave
Access by the WiMAX Forum
[1], formed in April 2001 to promote conformance and interoperability of the
standard IEEE 802.16. The Forum describes WiMAX as "a standards-based technology
enabling the delivery of last mile wireless broadband access as an alternative
to cable and DSL." The WiMAX Forum is "the exclusive organization dedicated to certifying the
interoperability of BWA products, the WiMAX Forum defines and conducts
conformance and interoperability testing to ensure that different vendor systems
work seamlessly with one another." Those that pass conformance and interoperability testing achieve the “WiMAX
Forum Certified” designation and display this mark on their products and
marketing materials. Vendors claiming their equipment is “WiMAX-ready,”
"WiMAX-compliant,” "pre-WiMAX," are not WiMAX Forum Certified, according to the
Forum.
[2]The IEEE 802.16 media access controller (MAC) is significantly different from
that of
IEEE 802.11 Wi-Fi
MAC. In Wi-Fi, the MAC uses contention access—all subscriber stations wishing to
pass data through an access point are competing for the AP's attention on a
random basis. This can cause distant nodes from the AP to be repeatedly
interrupted by less sensitive, closer nodes, greatly reducing their throughput.
And this makes services, such as VoIP or IPTV which depend on a determined level
of quality of service (QoS) difficult to maintain for large numbers of users. By contrast, the 802.16 MAC is a scheduling MAC where the subscriber station
only has to compete once (for initial entry into the network). After that it is
allocated a time slot by the base station. The time slot can enlarge and
constrict, but it remains assigned to the subscriber station meaning that other
subscribers are not supposed to use it but take their turn. This scheduling
algorithm is stable under overload and over-subscription (unlike 802.11). It is
also much more bandwidth efficient. The scheduling algorithm also allows the
base station to control Quality of Service by balancing the assignments among
the needs of the subscriber stations. A recent addition to the WiMAX standard is underway which will add full
mesh networking capability by enabling WiMAX nodes to simultaneously operate
in "subscriber station" and "base station" mode. This will blur that initial
distinction and allow for widespread adoption of WiMAX based
mesh
networks and promises widespread WiMAX adoption. WiMAX/802.16's use of OFDMA
and scheduled MAC allows wireless mesh networks to be much more robust and
reliable. These differences between and evolution of Wi-Fi and WiMAX mesh
networks could serve as a separate topic. The original WiMAX standard, IEEE 802.16, specifies WiMAX in the 10 to 66 GHz
range. 802.16a, updated in 2004 to 802.16-2004, added support for the 2 to 11
GHz range, of which most parts are already unlicensed internationally and only
very few still require domestic licenses. Most business interest will probably
be in the 802.16-2004 standard, as opposed to licensed frequencies. The WiMAX
specification improves upon many of the limitations of the Wi-Fi standard by
providing increased bandwidth and stronger encryption. It also aims to provide
connectivity between network endpoints without direct
line
of sight in some circumstances. The details of performance under non-line of
sight (NLOS)
circumstances are unclear as they have yet to be demonstrated. It is commonly
considered that spectrum under 5-6 GHz is needed to provide reasonable
NLOS performance
and cost effectiveness for PtM (point to multi-point) deployments. WiMAX makes
clever use of multi-path signals but does not defy the laws of physics.
Alcatel is demonstrating its IMS (IP Multimedia Subsystem) over WiMAX services.
Wireless Operator -
“Wireless operator” is a general term that refers to either a wireless network
operator or a wireless service operator. The wireless network operator, also
called a “carrier,” maintains the radio towers and infrastructure for a cellular
system. Wireless service operators sell wireless service to subscribers and
contract with wireless network operators to provide their service. Outside of
Europe, the wireless network operator and wireless service operator functions
are combined within one company that is referred to as the “carrier” or wireless
operator.
WLAN - A Wireless LAN is a wireless local
area network that uses radio waves as its carrier: the last link with the users
is wireless, to give a network connection to all users in the surrounding area.
Areas may range from a single room to an entire campus. The backbone network
usually uses cables, with one or more wireless access points connecting the
wireless users to the wired network. WLAN is based on various versions of IEEE
802.11 (Wi-Fi).
802.11b (typically 30ft.), 54 Mbit/s 802.11a (5 GHz) and 802.11g (2.4 GHz).
Security is a major
concern. The fact that someone can sit in the car park (or building next door),
pick-up and store all your wireless traffic, and crack the most common
implementation of Wireless encryption (WEP) in less than a week (and then read
all the stored traffic) has to be a concern to any business operation (see
Wardriving).
Changing the wireless LAN encryption key on a daily or weekly basis, and then
'rolling it out' (by some means other than 'plain text' emails) is an extra
overhead that many Companies never manage to achieve. IPSec is often used by
larger businesses that have the infrastructure to support it. Wi-Fi Protected
Access (WPA) is now available in most access points and provides adequate
security for most purposes.
WMIS - Warehouse Management
Information System.
WSDL -
The Web Services Description
Language (WSDL) is an XML format published for describing Web services. Version
V 1.1 has not been endorsed by the World Wide Web Consortium (W3C), however it
has released a draft for version 2.0 on May 11, 2005, that will be a W3C
recommendation, and thus endorsed by the W3C. It is commonly abbreviated
as WSDL in technical literature and is usually pronounced wiz-dell. WSDL
describes the public interface to the web service. This is an XML-based service
description on how to communicate using the web service; namely, the protocol
bindings and message formats required to interact with the web services listed
in its directory. The supported operations and messages are described
abstractly, and then bound to a concrete network protocol and message format.
WSDL is often used in combination with SOAP and XML Schema to provide web
services over the internet. A client program connecting to a web service can
read the WSDL to determine what functions are available on the server. Any
special datatypes used are embedded in the WSDL file in the form of XML Schema.
The client can then use SOAP to actually call one of the functions listed in the
WSDL. XLang is a extension of the WSDL such that "an XLANG service
description is a WSDL service description with an extension element that
describes the behavior of the service as a part of a business process"
BACK TO TOP
X
XACML
- stands for eXtensible Access Control Markup Language. It is
a declarative
access control policy language implemented in
XML. Version 2.0 was ratified by
OASIS
standards organization on 1 February 2005.
xDSL - The letter x means
generic - term for Digital Subscriber Line equipments and services, including
ADSL, HDSL, IDSL, SDSL, and VDSL. xDSL technology provide extremely high
bandwidth over the twisted-pair that runs from your phone company's central
office to your office or home.
XGA - Extended
Graphics Array card. IBM's graphics standard that includes VGA and extended
resolutions up to 1024 x 768, interlaced; 35 kHz. This card has a 15-pin HD
connector.
XML - The Extensible Markup
Language is a W3C-recommended general-purpose markup language for creating
special-purpose markup languages, capable of describing many different kinds of
data. It is a simplified subset of Standard Generalized Markup Language (SGML).
Its primary purpose is to facilitate the sharing of data across different
systems, particularly systems connected via the Internet. Languages based on XML
(for example, Geography Markup Language (GML), RDF/XML, RSS, MathML, Physical
Markup Language (PML), XHTML, SVG, MusicXML and cXML) are defined in a formal
way, allowing programs to modify and validate documents in these languages
without prior knowledge of their form.
BACK TO TOP
Y
Y/C - Two channel video
channel. One used for color (chrominance) and the other for black and
white (luminance). This designation is used for video signals that keeps
separate the luminance and the chrominance information; thus, preventing some of
the normal NTSC artifacts like E.G., cross-color, and cross-luminance.
YUV - A color encoding
scheme for natural pictures in which luminance and chrominance are separate.
Three
image components that provide alternative representation of red, green, and
blue. (See RGB).
The human eye is less sensitive to color variation than to intensity variation. YUV allows the encoding of luminance (Y) information at full bandwidth and
chrominance (UV) information at half bandwidth.
YUV9 - The color encoding
scheme used in Indeo Video Technology. The YUV9 format stores information
in 4x4 pixel blocks. 16 bytes of luminance are stored for every 1 byte of
chrominance. For example, a 640x480 image will have 307,200 bytes of
luminance and 19,200 bytes of chrominance.
BACK TO TOP
Z
ZV - Zoomed Video -
Technology that allows certain streams of digital information to write directly
to a laptop's screen; thus, bypassing the CPU and its bus (ISA, PCI, EISA,
etc.). Zoomed Video can show full 30 frames per second movies to a laptop
screen. ZV technology is to bring full laptop screen videoconferencing to
laptop.
BACK TO TOP
|
![[Company Logo Image]](images/atksilogo.gif)
